Introduction
NIST stands for the National Institute of Standards and Technology. They were founded in 1901 and are now a part of the US Department of Defense (DoD). NIST is well known for providing standards on all sorts of technologies and they are one of the leaders when it comes to cybersecurity. As a member of the DoD they are heavily focused on helping companies by providing standards that can be used to secure a company's infrastructure. One of the areas they are expanding into is secure coding practices.
Secure coding practices simply means coding practices that minimize the chance that developers will introduce vulnerabilities into their code.
You can imagine how important this is in today’s market where virtually every company relies on software at some level, every software application that is internet facing is a potential entry point for a hacker. A large number of security vulnerabilities, especially in web applications are due to improperly written code. Some popular examples include cross-site scripting (XSS), SQL injections and cross-site request forgery (XSRF) to name a few.
For any business that develops software, it’s important that you invest in teaching your developers secure coding practices to avoid security breaches later down the line. This is also the best way to reassure your customers on privacy concerns. One way to do this is to use well-written standards that outline what developers need to know in a concise way. This is what NIST is currently developing. NIST, in partenership with the government, is aiming to create a new standard on DevSecOps to help companies better understand how they can create secure software.
The NIST standard for secure code practices will take a risk-based approach, which simply means it begins by looking at the threats facing the organization and based on those threats determines what controls need to be in place in order to be secure. The advantage of this approach is that it’s preparing you for the threats you are most likely to face from hackers when your software product hits the market.
NIST’s Value Proposition
As NIST moves towards a risk-based approach for secure software development they have highlighted several areas that will be positively impacted in companies that follow this standard.
More security with little delays
NIST states that this new approach is designed to implement better security while minimizing the delay to software production. Time delays are one of the biggest reasons why things like source code reviews, threat modeling and other security precautions are not done or rushed. It’s important to minimize time delays to have maximum adoption of a standard.
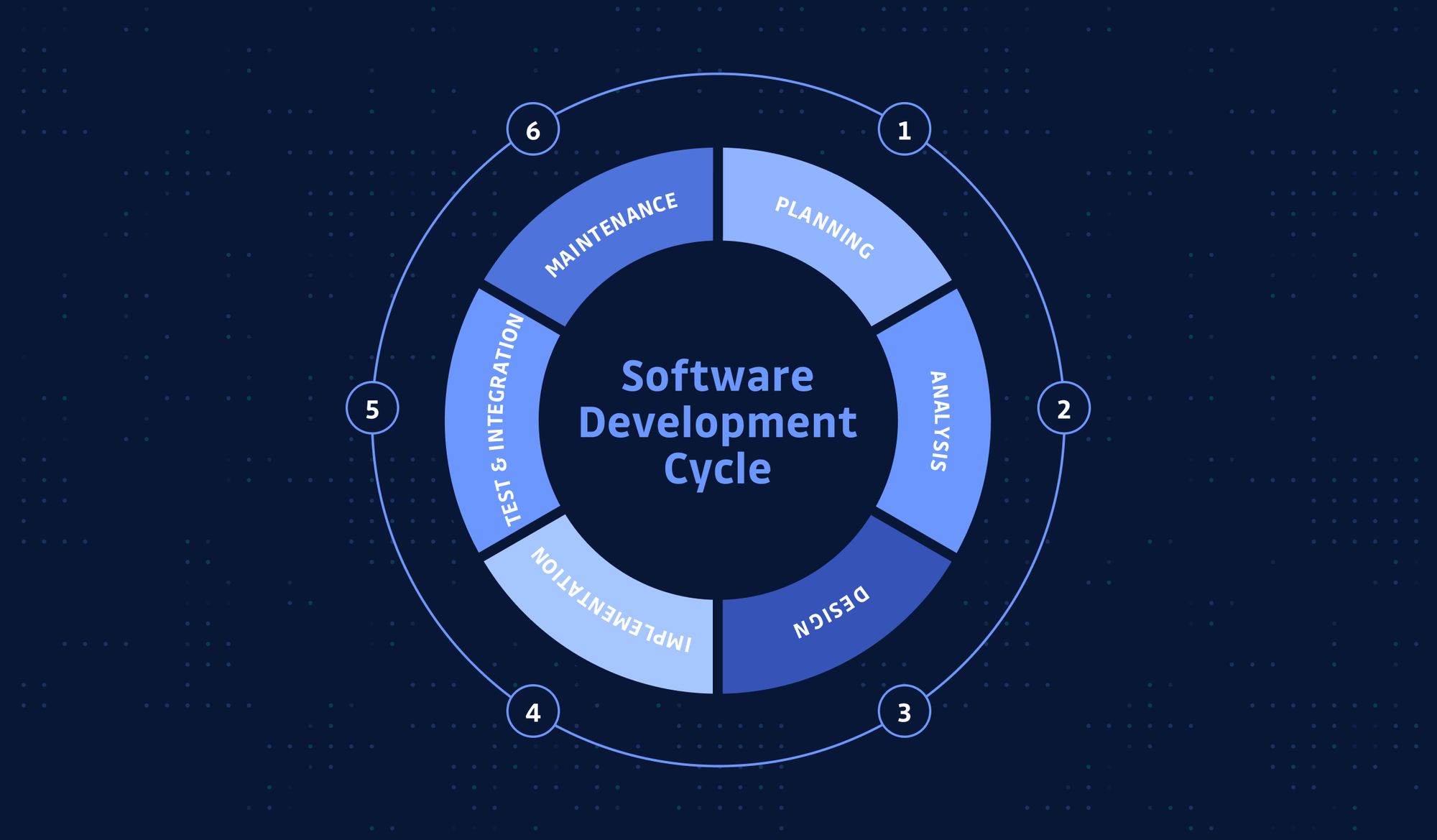
Mitigate vulnerabilities through the software development lifecycle (SDLC)
This standard doesn’t just focus on the development phase of software development, it aims to improve security across all phases from development to when the code is executed. One reason this is so important is the difference between finding vulnerabilities during source code reviews and security bugs during runtime. It’s important to test an application at both of these points because some vulnerabilities may show up in one set of testing and not the other.
Address root cause of vulnerabilities to prevent reoccurrence
This standard is going to explain the root causes of vulnerabilities in software development so that changes can be made to the workflow to prevent them from happening again. Some examples they gave are “strengthening test tools and methodologies in the toolchain, and improving practices for developing code and operating hosting platforms”.
Reduce friction between Development, Operations and Security Teams
This is essential in order to make sure that the company has the speed and agility needed to meet the organization's goals while taking advantage of the latest security technology. It’s important security teams have visibility into the development teams’ operations and workflow so that they can advise them on any potentially insecure practices that they have.
NIST four steps to a secure coding program
1. Foundational Research
First, NIST is conducting research on the new and emerging development methodologies, tools and techniques and their potential cybersecurity implications. This is a good sign, since technology changes every few years standards designed for just today’s technologies may become obsolete very quickly so considering emerging technology in their design is a good idea.
2. Develop International Standards and Practices
Once the research is completed, they will develop international standards and practices for secure software development. These will be high-level concepts and more of the theory behind why you should perform software development in a certain way. When it comes to implementation these will be more at the policy level, overseeing software development processes in the company as opposed to being at the operational level.
3. Creating practical guidelines
Next, NIST will make practical guidelines that can be applied in organizations to produce software in a secure way. While the standards will be more high level, these will be actionable steps that companies can take to improve their software. These guidelines could be adopted by organizations as a methodology to be used when developing software so that you have a systematic way of ensuring that your software is created with as few security bugs as possible.
4. Demonstrate the use of current and emerging secure development frameworks, practices and tools to fix cybersecurity challenges
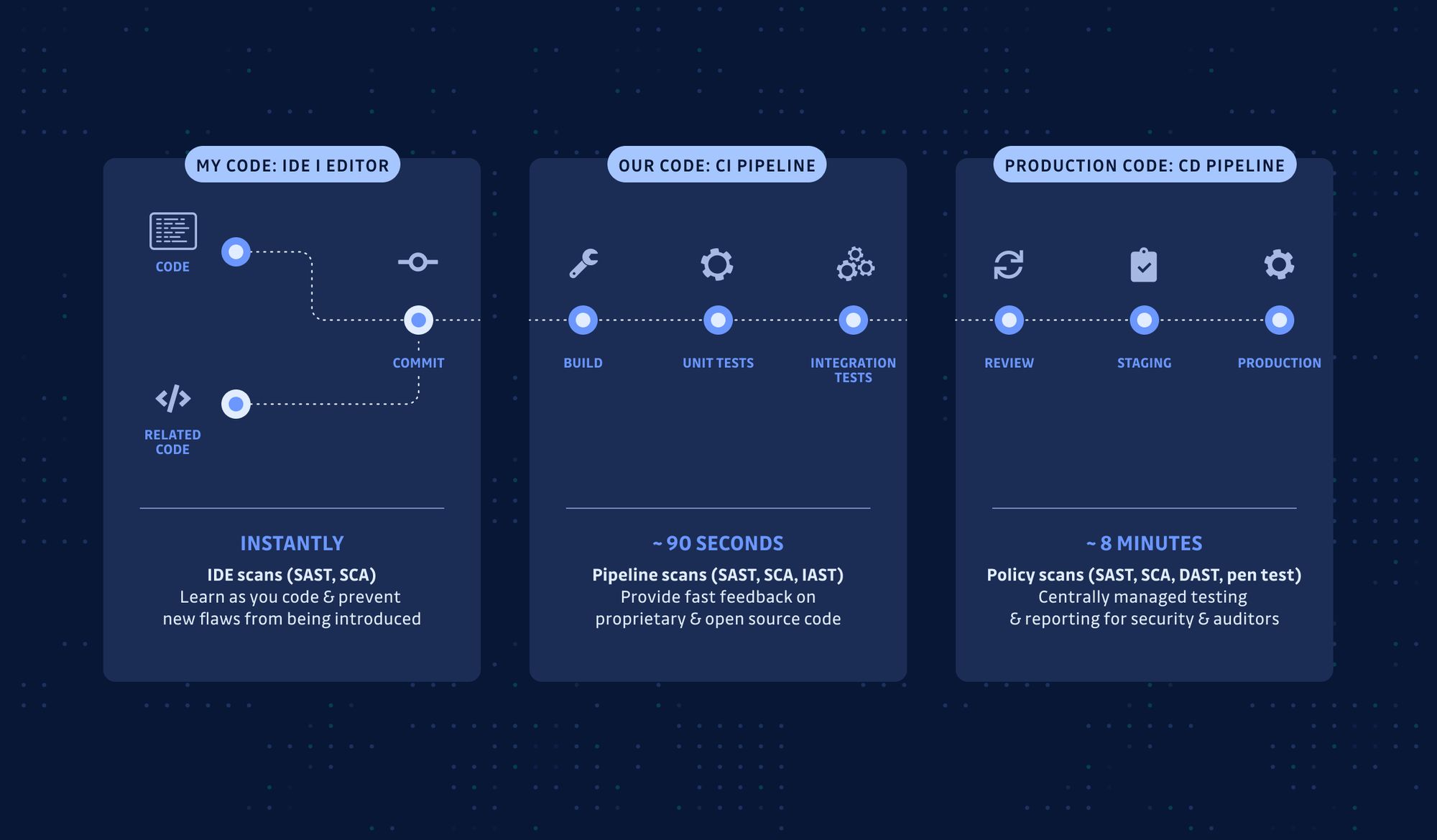
The last phase of the NIST plan for secure coding practices is to demonstrate how the current and emerging secure development tools can be used to address security issues. Nowadays we don’t rely solely on manual code reviews, we use source code analysis tools such as SAST and DAST tools, dependencies vulnerabilities detection, and secrets detection, which allow us to test our source code and code at runtime for errors. This is just one example of the type of innovation we have in the secure coding area that can be used to improve security without adding big-time delays to software development projects.
Conclusion
NIST is looking to develop a set of practices that will help companies produce secure software without having a big impact on the speed of production. The end users should benefit from stronger rules and guarantees to preserve the privacy of their data.
While this project is still in development we know that it will focus on securing all elements of the SDLC and will be compatible with the latest trends in software development, which means these guidelines should be useful for years to come.
In the meantime, NIST is well known for publicizing some security standards that are still useful for securing your company today. Some examples of this include NIST’s cybersecurity framework and Secure Software Development Framework (SSDF).
Also, the NIST has been mandated "with enhancing cybersecurity through a variety of initiatives related to the security and integrity of the software supply chain" by the governement's Executive Order 14028
We will be covering each of these steps, with a first article on the definition of "Critical Software"
Finally, read about NIST recommendations on secrets in this article:

This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly












