We're thrilled to announce our GitHub Security Audit is now just one click away! With just your company domain, you can uncover potential security risks in minutes (an email verification is needed to get the report's details for confidentiality):
Are You Exposed on Public GitHub? Discover Now!
Why This Matters
Leverage GitGuardian's unique 7-year knowledge base of publicly exposed secrets on GitHub and get a comprehensive, confidential audit report instantly.
Enter your domain name—e.g. mycompany.com—and get an answer to the following:
- What's my developer footprint? How many of your company's developers are active on GitHub (not just counting GitHub organization members, but also the wider scope of people using a company email to contribute anywhere)?
- What's my attack surface? What's the size of your public GitHub exposure?
- What's my leak assessment? How many of my developers' secrets have been leaked in the past 3 years?
- What are the immediate risks? How many leaks are still valid, posing immediate risk?
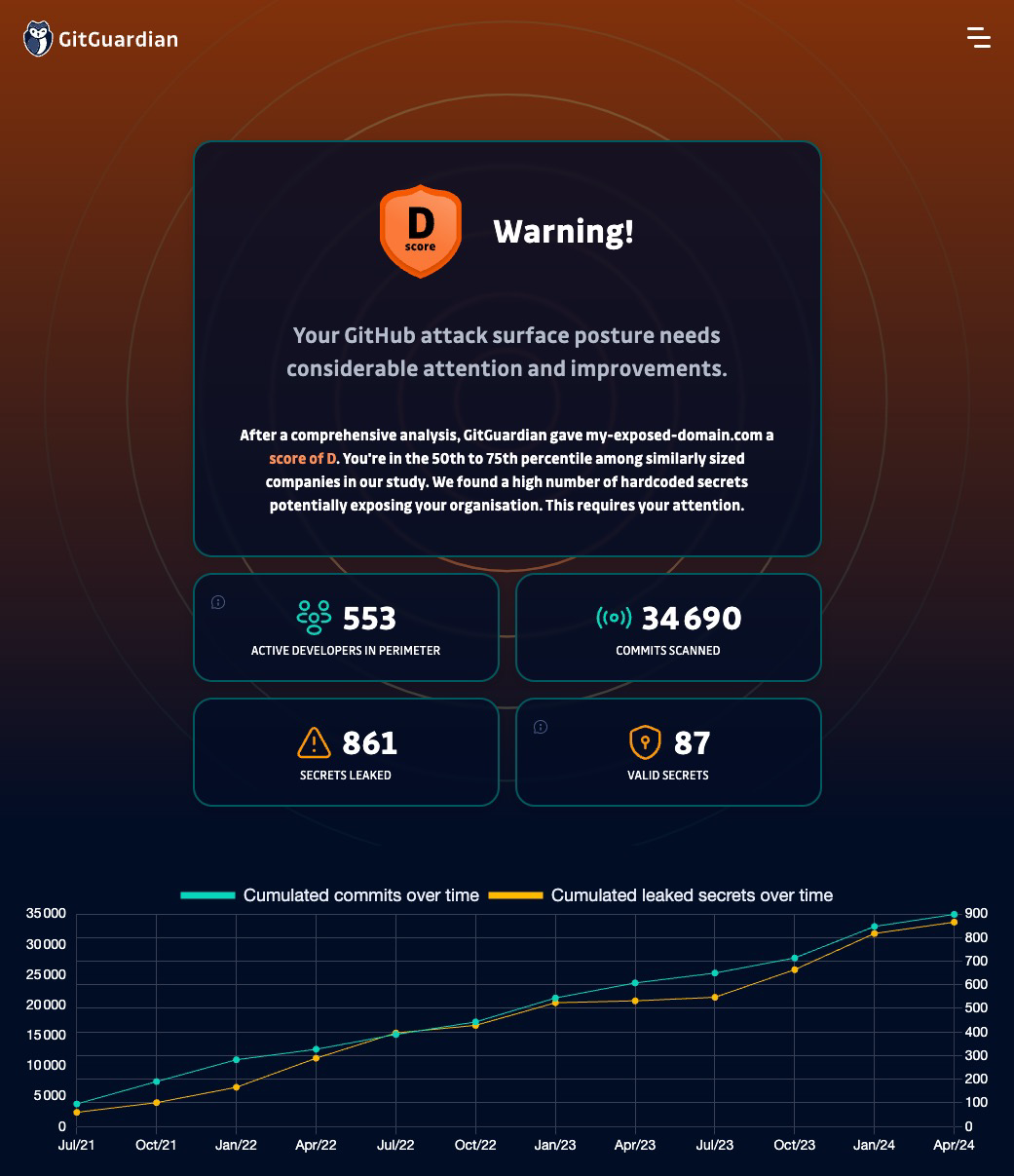
Introducing the Public GitHub Attack Surface Score
All these metrics are summarized in the Public GitHub Attack Surface Score, ranging from A to E, to give you a quick overview of your security posture.
But that's not all.
Dive Deeper with Full Report Access
The full report access is automatically sent to your email (the domain needs to match for confidentiality). Here's what you'll find in it:
- Secrets breakdown by category: Percentage of secrets leaks for each category (eg. Private key, Version control platform, Cloud provider, Messaging system, Data storage, etc.).
- Direct company mentions in commits: Commits that mention your company domain in the committed code.
- Developers involved in leaks: Developers from your perimeter who have leaked at least one secret.
- Secrets sensitive files: Secrets that were published inside a file that is sensitive in itself, such as a configuration file.
- Public repository events: When private repositories are made public. This is sensitive as it discloses the entire history of a repository, where sensitive data could be found.
- Secrets erased from GitHub: Secrets that can no longer be found on GitHub but have been leaked and can be found in GitHub archives (a.k.a. zombie leaks).
Why It's Critical
Even if your organization doesn’t engage in open source, your developers or subcontractors may inadvertently leak sensitive information on their personal GitHub repositories. Don't risk exposing corporate secrets or source code: get your free GitHub Leaks Audit today and take control of your security posture:
Launch Your Free GitHub Security Audit
GitGuardian’s secrets detection engine has been running in production since 2017, analyzing billions of commits coming from GitHub. The algorithms and detectors constantly train against a dataset of 4 billion commits. The latest State of Secrets Sprawl 2024 reveals 12.8 million new secrets occurrences were exposed on GitHub in 2023. GitGuardian can tell you how many leaks are tied to your company by first identifying your developers active on GitHub.









