Now you’ve met Philippe, let’s talk about a very common misconception that security professionals may have: “I have already bought this “all-in-one” or “one-size-fits-all” solution, so now I should be safe.”
Let’s listen to what Philippe has to say about this.
When talking to various organizations, I regularly meet IT teams who would love to find THE solution. You know, this perfect tool that you would just have to install and you’d be protected against all possible attacks… As you can imagine, such a solution does not exist despite claims from unscrupulous vendors.
Quite often, we see security solutions that are not properly implemented or simply do not work as expected. This often leads to generating too many false positives where normal events get miscategorized as security incidents and end up being ignored over time (until real security incidents occur). This is what we call “security fatigue”. On the other hand, some security solutions are not properly configured leading to false negative, where real security incidents do not even generate an alert.
When we successfully penetrate an organization’s IT infrastructure, either we do not trigger an alert because their notification systems have been disabled, or, they have so many alerts that the alert that really matters is lost in the mix and gets ignored. This is one of the reasons why, one of our last phases after a successful compromise is to voluntarily perform actions that should generate alerts in order to measure the detection capabilities of our customers. And surprisingly, most of the time this does not trigger any response.
For example, we create a new rogue domain admin user. This is typically easy to detect and could be an indicator that something wrong is happening: an admin user is not created every day, and its creation should follow a strict change management process. As such, these types of events should be under strict surveillance.
The bottom line here is that security teams (and real-time monitoring solutions) should focus on compromise indicators rather than trying to look at everything all the time. They should also evaluate each solution to ensure that it does what it claims and they should run diagnostics to evaluate what solutions are needed and how they should be implemented.
One piece of advice: Do not take for granted vendors’ claims. I cannot count the number of times we bypassed so-called “new generation security tools” with very basic techniques.
For instance, a few years back, one of our clients spent over 6 months (and a lot of money) to deploy a new generation antivirus throughout their organization, and it took us less than 5 minutes to realize that it could be deactivated by simply uninstalling the application. This demonstrates a typical issue when organizations overprotect one door, but they leave another door wide open. As an attacker, if you run into a security solution that is efficient you simply try to go around it.
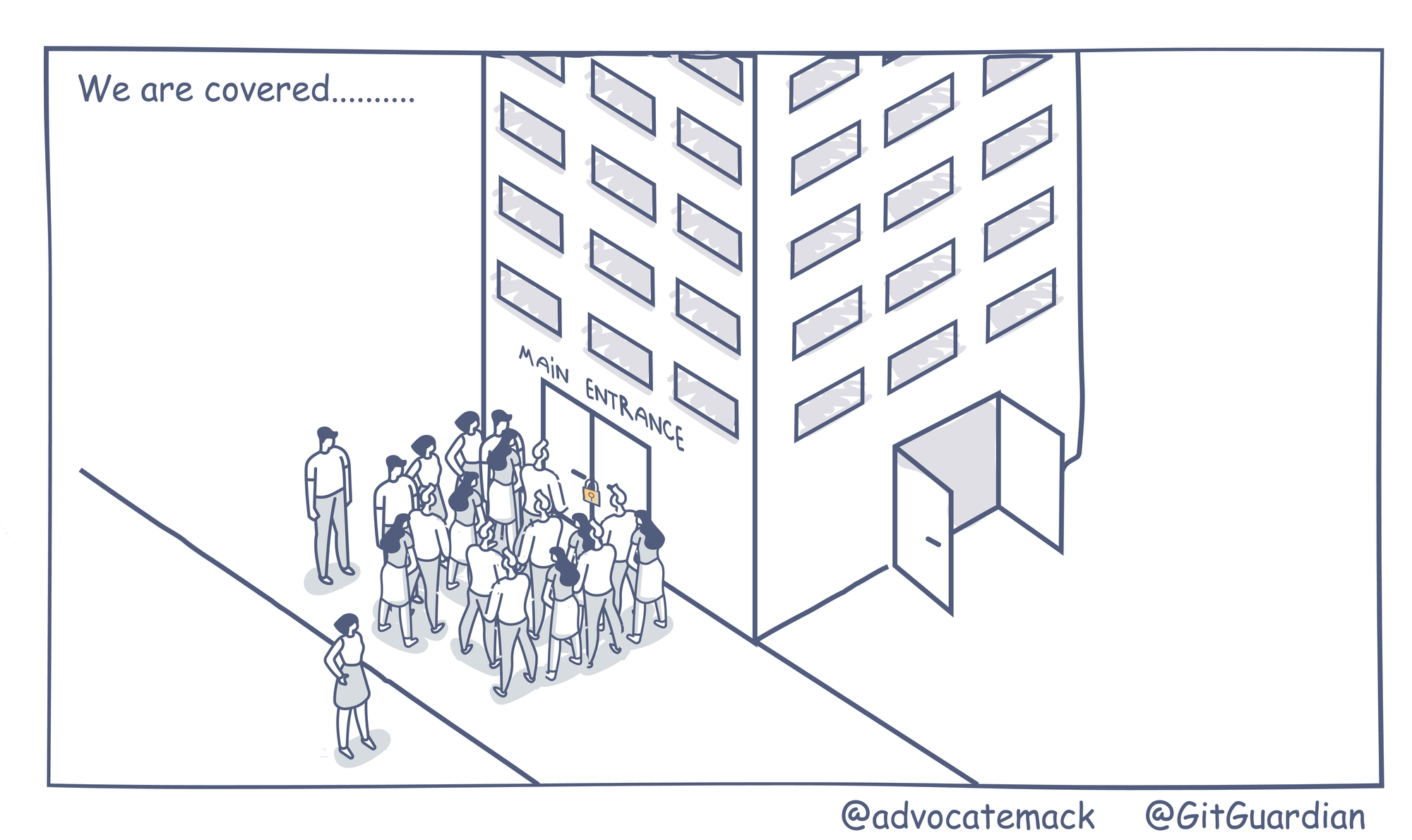
When evaluating your security posture, you should always try to look at your environment like an attacker would. This is why our slogan is "We protect you from people like us."
You should think of all possible entry points and have a holistic approach to cover all your bases, rather than try to build a fortress around your crown jewels. This is why running red team exercises internally or externally is important.
As you can see, Philippe has some interesting stories to share as well as some useful recommendations to make. If you are interested, keep following the Red Team Chronicles by subscribing to our newsletter or following us on twitter or LinkedIn.
Checkout Episode 3!








