In the previous episode, Philippe emphasized the need for a shift in the security posture toward better detection. So let’s dig into this subject.
We will first look at the timeline of a compromise:
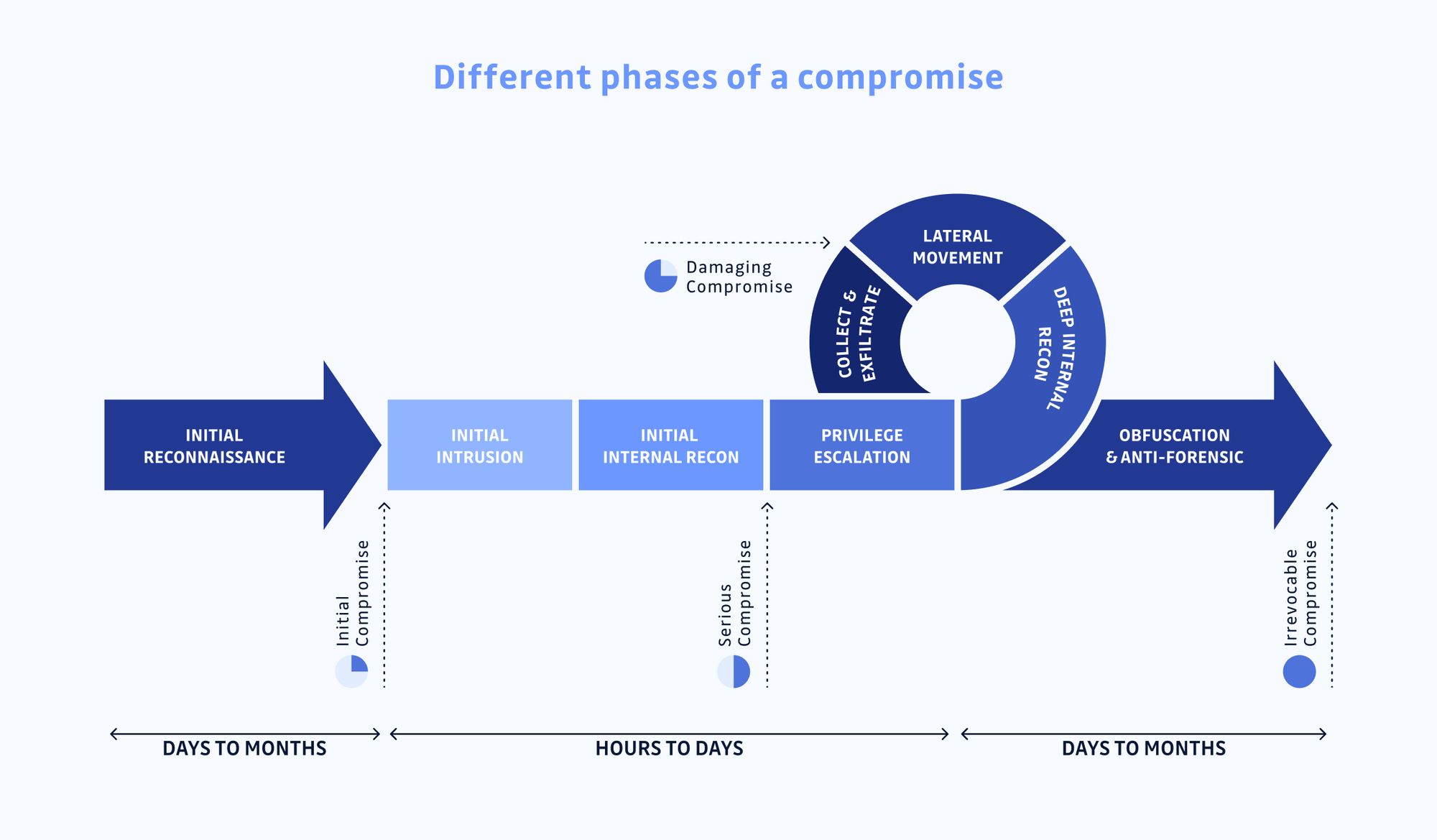
Philippe, can you drive us through this process, please?
Here, you go: during the initial reconnaissance phase, hackers will gather as much information as possible. The objective being to make initial access into the target system. Once you have access to the first system the initial intrusion happens. Hackers benefit from the trust that is put in the system they entered.
The next phase will be to try to elevate privileges. One thing that I usually do when I access a server is then to use the “history” command to gather a list of the previous 500 commands made and store them. It can give us credentials or file names that could store secrets.
Hackers will then move laterally to access critical data and exfiltrate them. Once this is done, they will obfuscate their traces. This is then very difficult for the security teams to know what exactly happened.
Most organizations focus on preventing the initial intrusion, but as we saw with examples provided in previous episodes, it is a bit of a lost cause. Security teams should also focus on putting in place a proper alerting system for the phase between initial compromise and serious compromise. When hackers have access to legitimate admin profiles, it is too late. They will not trigger any alerts anymore.
Even if ransomware is put in place during the initial phase it is limited to 1 or 2 machines, but after it can be the whole company. We see more and more of this type of corporate ransomware. They are much more profitable for hackers. In the past, hackers would cash in as soon as they compromised one machine, now they stay and take the time to escalate, move laterally and compromise the whole organization.
Alerting should be in place for key events leading to privileges, like admin profile creation for example, and for anomalies (server and services reboot, NTP synchronization, authentication failures).
Do you have other best practices for us?
Know your environment, not just what is exposed to the outside world. Where is your code, who has access to it, what are the passwords for?
If you have legacy servers, isolate them. Think that hackers are bouncing from one spot to another, try to block them in dead ends.
Install security patches, I repeat install security patches...
Do not use professional email addresses for external sites that are not essential to your business, or at least use password generators to avoid pattern copying.
Do not have a check box approach to security. Try to think like hackers to adapt your security approach to your environment.
And of course make some intrusion tests, internally or with external providers or bug bounty programs.
We hope that you enjoyed this first series of the Red Team Chronicles with Philippe Caturegli and that detection is now part of your agenda!








