In the past, the development of software was something that required a lot of effort and resources. Basically, every piece of code was developed in-house, and code reuse was quite limited. The situation is now the opposite. Open-source packages are so widely used that they make up the bulk of the total amount of software produced by passionate hobbyists and virtually all the software professionals in tech companies. The convenience of reusing and fine-tuning components made open-source is just too strong for most software engineers to ignore it and keep "reinventing the wheel".
To get a better idea of how big open source has become, we have some recent insights: according to a survey from Gartner, over 90% of the respondents stated that they rely on open source components. In another report from Synopsis, 98% of the audited codebases contained at least one open-source component, and 75% of the source code came from open-source. The report also noted that 85% of the audited codebases contained components "more than four years out of date".
This last data reveals the growing concern about the reliability and security of all this open-source material found in private code bases. Packages that are not maintained anymore cannot be patched for recently discovered vulnerabilities. Therefore it's become critical for organizations to be able to inventory open-source components and assess their vulnerabilities, making the use of open-source software composition analysis mandatory. But not all SCA tools are created equal.
This blog post will provide eight factors to consider when choosing an SCA tool.
What is SCA (Software Composition Analysis)?
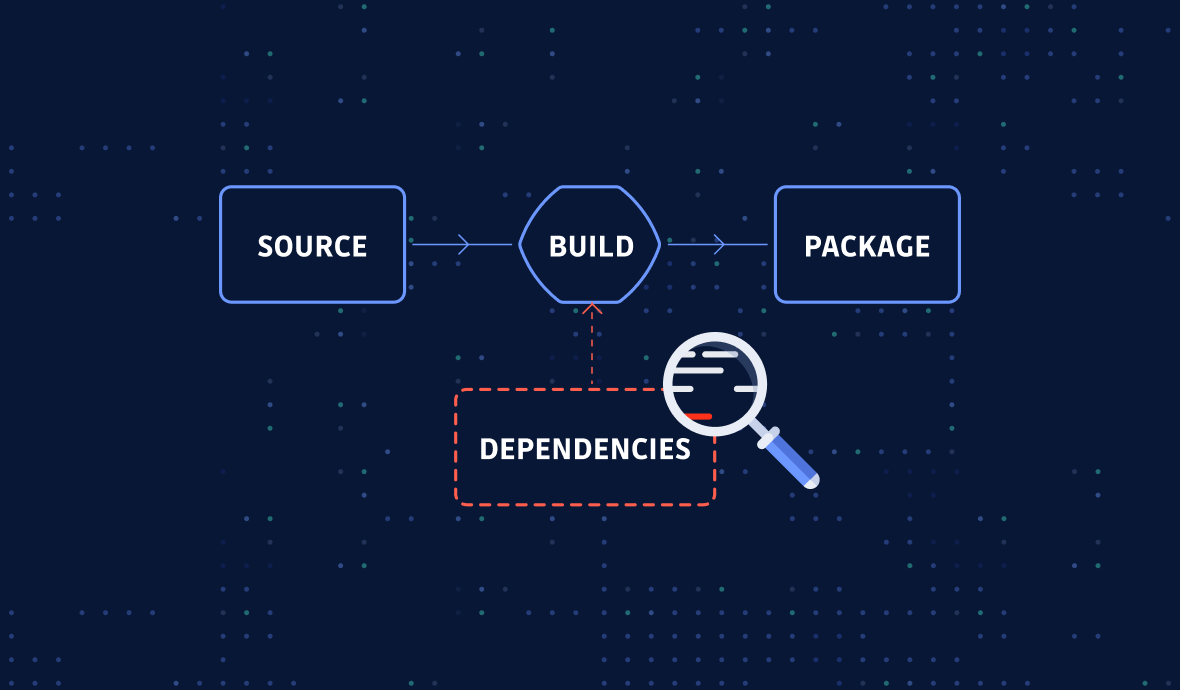
SCA is the process of analyzing an application's dependencies to determine if it is affected by known security vulnerabilities. Organizations can more effectively manage security risks by understanding the dependencies between components.
SCA can be performed either manually or using automated tools. Manual open-source software composition analysis is not scalable as the engineers must constantly check a vulnerability database such as NVD (National Vulnerability Database, maintained by NIST) and then compare the vulnerable versions with their existing dependencies. Much more efficient is to use automated SCA security tools, which can be triggered manually or integrated into the CI/CD pipeline for continuous checks.
Importance of Software Composition Analysis
SCA is integral to application security, as it helps identify and mitigate risks associated with using third-party components. SCA can help identify vulnerabilities in third-party components that attackers could exploit. It can also help track the versions of third-party components and ensure that they are up to date. By keeping track of the components used in an application, SCA can also help ensure compliance with license and security policies.
In short, SCA is an essential part of the code security toolkit, focused on third-party components.
SAST vs SCA: what’s the difference?
SAST is a software testing technique that involves analyzing the source code of a software application to identify potential security vulnerabilities such as injection attacks, cross-site scripting (XSS), improper error handling, and insecure use of cryptographic functions.
SAST aims to identify security vulnerabilities early in the software development cycle to mitigate them before the application is compiled and deployed.
While SAST is an analysis technique used to check for known vulnerabilities in source code, SCA is used to scan dependencies for security vulnerabilities and license issues.
Both are usually performed pre-build (against source code), or post-build (against binaries), as they don't require an application's execution to identify potential vulnerabilities. Both are equally important in ensuring the security of a software application.
How to Choose an SCA tool?
So many software composition analysis vendors are present on the market today that it can be hard to decide which tool is the right one for your needs. To help you select the right one, we have curated a list of 9 things you should look out for in an SCA tool:
- Check for language & package manager support
- Choose an accessible and well-documented tool
- Make sure the tool supports binary scanning
- Verify how the tool reports transitive dependencies
- Test the tool for false positives (noise) and false negatives (undetected vulnerabilities)
- Choose a tool with API and webhooks support
- Make sure the backing vulnerability database is rich enough
- Evaluate the time to onboard new CVEs
- Ask for detailed reports with remediation guidelines if possible
1. Language Support
When opting for an SCA tool, it's vital to check what all languages are supported by the tool. Software composition analysis is language, end even ecosystem-dependent (package managers, build system, etc.): for instance, most SCA tools rely on lock files such as package-lock.json or Pipfile.lock to find dependencies and their respective versions. So you need to be careful here.
2. Accessible to Use/Developer Friendliness
The SCA tool you choose should make your life easier, not harder. It should be intuitive and easy to use so that you can focus on your work, not on learning the tool. It should also be developer friendly so that you can easily integrate it into your existing development process. Also, it should be scalable to grow with your organization.
The vendor should also have proper technical documentation available for the developers and having technical support for the tool is always a plus.
3. Support for Binary Scanning
When looking for a Software Composition Analysis (SCA) tool, choosing one that supports the scanning of binary files is essential. Many SCA tools don't support this type of scanning, which can leave vulnerabilities in the binaries used by the developers unchecked.
Scanning binary files such as wheel files(.whl) are essential because it can find vulnerabilities that would otherwise be missed by scanning the dependencies. If you are not doing binary scanning used by your developers, you are not getting the complete picture of your code's security.
4. Direct vs. Transitive Dependencies
There are two types of dependencies in software development: direct and transitive. A direct dependency is when one piece of software directly depends on another piece of software. For example, if software A directly uses software B, then A has a direct dependency on B. Conversely, if software A uses software B, and software B uses software C, then A has a transitive dependency on C.
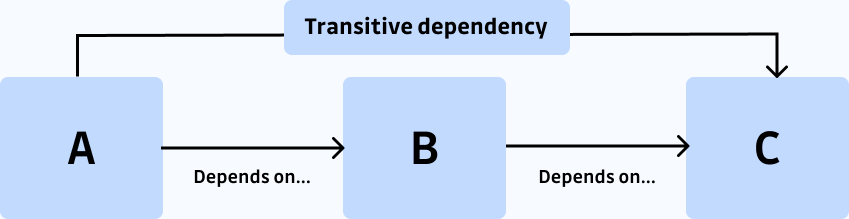
The SCA tool should be able to provide you with the information if the vulnerability is in the direct dependency or transitive dependency. This is important because both types of dependencies can pose a security threat to a software project.
5. False positives / False negatives
If you are not familiar with the concept of false positives and false negatives, you should read this article about accuracy, precision, and recall. In a nutshell, false positives are vulnerabilities wrongly flagged as such by the tool, and false negatives are genuine vulnerabilities that the detection tool silently skipped. This is an important factor to consider when choosing a software composition analysis tool because false positives can lead to wasted time and resources. Developers may spend a significant amount of time manually reviewing and investigating these results, even though most are not security threats. This (also known as "alert fatigue") can be frustrating for developers and decrease their trust in the tool, potentially leading them to ignore or not use the tool as frequently as they otherwise would.
The numbers reported by vendors can be challenging to verify. The best way to ensure that an SCA tool can accurately identify security threats while minimizing the number of false positives is to test it (for free, when possible).
6. Webhooks & API Support
When looking for an SCA tool, it's essential to check if the tool has proper API and webhook support so that you can easily integrate it into your CI/CD pipeline.
Having proper API and webhook support will allow you to automate SCA scanning as part of your CI/CD process, which will help ensure that your applications are always up-to-date and compliant with security standards. Without proper API and webhook support, you may have to manually trigger SCA scans, which can lead to delays in your pipeline.
7. Rich Vulnerability Database
A good SCA vendor should have a rich vulnerability database to detect vulnerabilities in your open-source packages. Such a database would enable the SCA vendor to provide you with customized alerts and recommendations on the best way to fix the identified vulnerabilities.
In addition, the SCA vendor should have a team of expert analysts who can help you understand the nature of the vulnerabilities and their potential impact on your organization in case you need any support.
8. Time to Onboard New CVEs
SCA tools are used by many organizations to keep track of vulnerabilities and potential security risks. It's essential to check how much time the SCA tool takes to onboard new CVEs on their platform from the vulnerability database. This allows organizations to plan for and respond to new security risks promptly. Additionally, it helps to ensure that SCA tools are up-to-date and provide accurate information about the latest security threats.
9. Detailed Reporting/Remediation
The scanning should provide detailed reporting that helps the security team understand the scan results of the open-source packages. The report should include a list of all the packages that were scanned, as well as the results of the scan, including
- Vulnerability description
- CVSS score
- CVSSv3 score
- Version impacted
The SCA tool should also provide proper remediation steps so that the developers can fix the issues.
Conclusion
Open source has become the norm in the software development world, with nearly 80% of companies using open-source software in some form or another. For many companies, open source is the preferred choice for software development due to its flexibility, cost-effectiveness, and vast ecosystem of available tools and resources.
However, with the increasing popularity of open source, there is also an increase in the number of vulnerabilities of open-source packages. This can create several risks and challenges for companies, including vulnerabilities in developed applications, licensing issues, and potential security breaches.
Having a software composition analysis solution in your build and deployment pipeline can help you avoid security risks that might arise from any open-source dependency. You should now be more informed about the important factors to consider before selecting such as tool.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.