![Shai-Hulud 2.0 Exposes Over 33,000 Unique Secrets [Updated Nov, 27]](/content/images/size/w600/2025/11/shai-hulud--2--1.png)
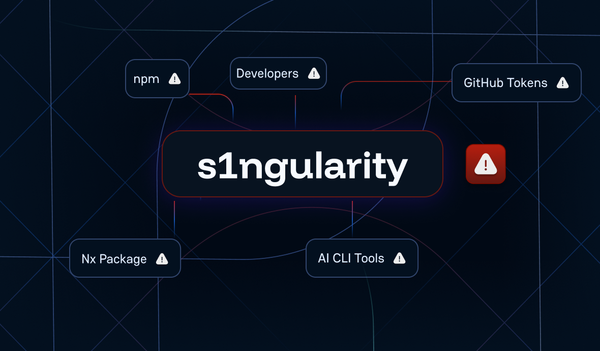
Shai-Hulud 2.0 Exposes Over 33,000 Unique Secrets [Updated Nov, 27]
On November 24, a new wave of the Shai-Hulud supply chain attack emerged. The threat actors exfiltrate stolen credentials directly to GitHub repositories created with compromised tokens.