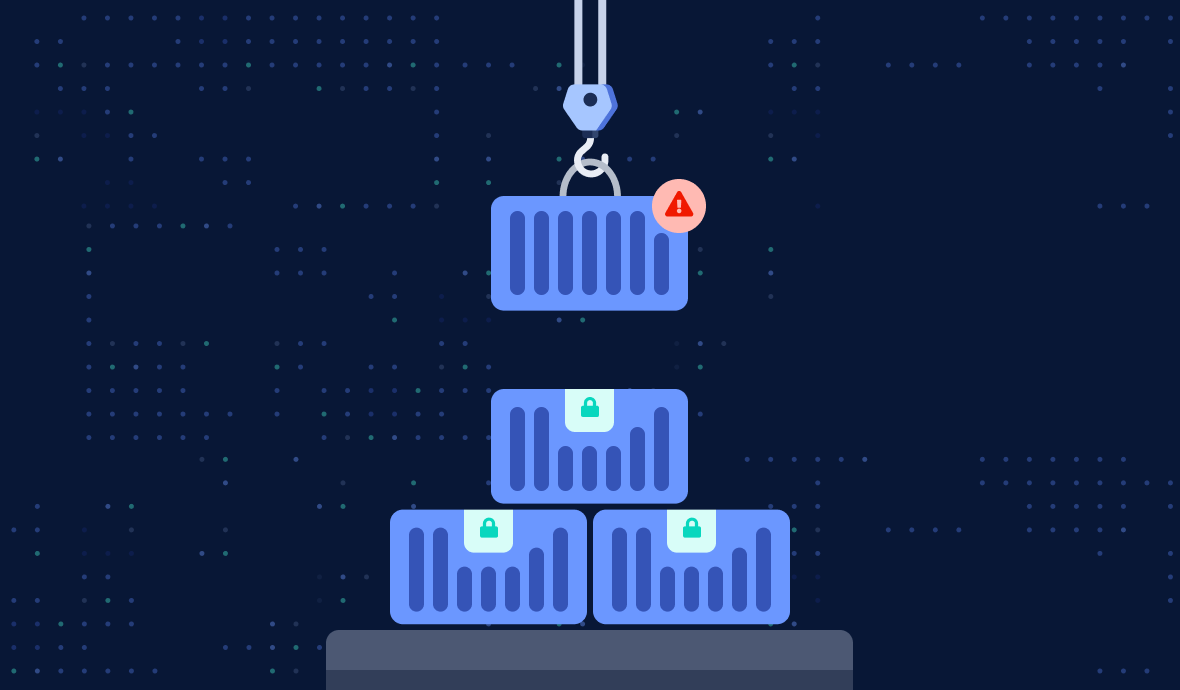
The Challenges of Identity Lifecycle Management for NHIs
Identity lifecycle management is one of the most underestimated security risks in many organizations. You may have structured IAM processes that handle the lifecycle of human identities, but what about your non-human identities (NHIs)?