
HMAC Secrets Explained: Authentication You Can Actually Implement
A developer-first guide to implementing HMAC signatures correctly.

A developer-first guide to implementing HMAC signatures correctly.

A practical guide to the Backend for Frontend pattern for secrets management.

Why outsourcing auth doesn't mean outsourcing risk.
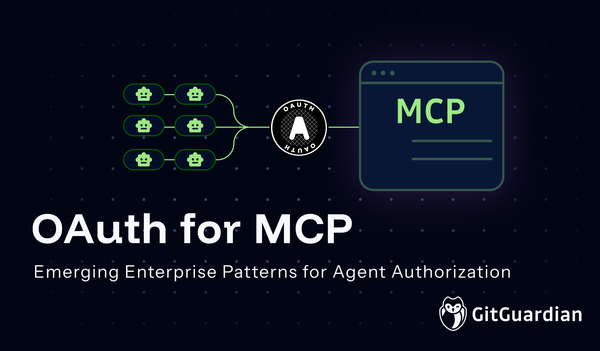
Why agents break the old model and require rethinking traditional OAuth patterns.

Any developer has to set up his Git config at least once. Our cheat sheet will help you make this process a breeze, ensuring that you never push with the wrong profile again!
GitHub's Push Protection is now enabled by default for all public repositories, a big milestone for open-source security! Find out the key points you need to keep in mind before using it to safeguard your code repositories.
![GitHub Actions Security Best Practices [cheat sheet included]](/content/images/size/w600/2022/05/22W18-blog-GitHubActionsSecurityCheatSheet.png)
Learn how to secure your GitHub Actions with these best practices! From controlling credentials to using specific action version tags, this cheat sheet will help you protect against supply-chain attacks. Don't let a malicious actor inject code into your repository - read now!

Researchers successfully extracted valid hard-coded secrets from Copilot and CodeWhisperer, shedding light on a novel security risk associated with the proliferation of secrets.

Learn how to safely remove confidential information from your git repository. Whether you need to excise an entire file or edit a file without removing it, this tutorial will guide you through the process. Plus, get tips on preventing future headaches with GitGuardian!

Organizations spend 32.4% of security budgets on code security, yet only 44% of developers follow secrets management best practices. Get the full insights in our 2024 report.
![Precision & Recall [Security Zines]](/content/images/size/w600/2024/10/Recall-in-Detection.png)
Or how to find a key in a code haystack

Exciting news! Our first book, "Crafting Secure Software," is now available. Learn how to embed security throughout the SDLC, mitigate risks, and foster a security culture. Get your copy today and level up your software security game!