Another month brings with it another bunch of CVEs we can analyze, while WordPress plugins certainly got some of the goods this month with much to talk about, and even a very juicy critical CVE allowing RCE via a file upload (honorable mention CVE-2024-5084) . This month I have picked a different vulnerability, CVE-2024-24919 connected to CheckPoint, this vulnerability is interesting not just because of its criticality but because of who the potential victims are.
What does the vulnerability do?
This vulnerability affects CheckPoint Quantum Security Gateways and is an arbitrary file read vulnerability. CheckPoint explained it in a post:
"exploiting this vulnerability can result in accessing sensitive information on the Security Gateway. This, in certain scenarios, can potentially lead the attacker to move laterally and gain domain admin privileges." The decrypted version of this is basically, the vulnerability that allows an unauthorized user to read files and potentially get credentials to move into different systems.
Originally CheckPoint described it as an “information disclosure vulnerability” however researchers at WatchTowr rightfully reassigned it as an arbitrary file read vulnerability.
Why is this vulnerability so interesting?
So this is clearly a very critical vulnerability but there are several things that lead this to being very interesting.
- Ease of exploit, this is a very easy exploit to use which means
- Criticality, It is a very critical vulnerability that grants unauthorized access to potentially sensitive file.
- Types of victims, CheckPoint is a well-established brand with great products. This means many very large organizations and government entities use the software
- Use in the wild, This exploit has been observed in the wild by several different threat actors.
What are security gateways?
Security Gateways are advanced firewalls that are able to monitor traffic and block malicious requests. Quantum Security Gateways are advertised as:
“Quantum security gateways and firewalls deliver uncompromising performance with advanced threat prevention, policy management, remote access VPN, IoT security, SD-WAN, and more."
This particular security gateway is very advanced in the market and used but multiple large companies making the potential victims very interesting for hackers.
What is an arbitrary file read vulnerability?
This is a very interesting vulnerability, essentially the security gateways had root access to the server machines, which meant any actor, without authentication, could craft a payload that would get them access to any file on the system (provided they knew the location). For example, gaining access to the etc/passwd file which could contain additional sensitive information for an attacker to use.
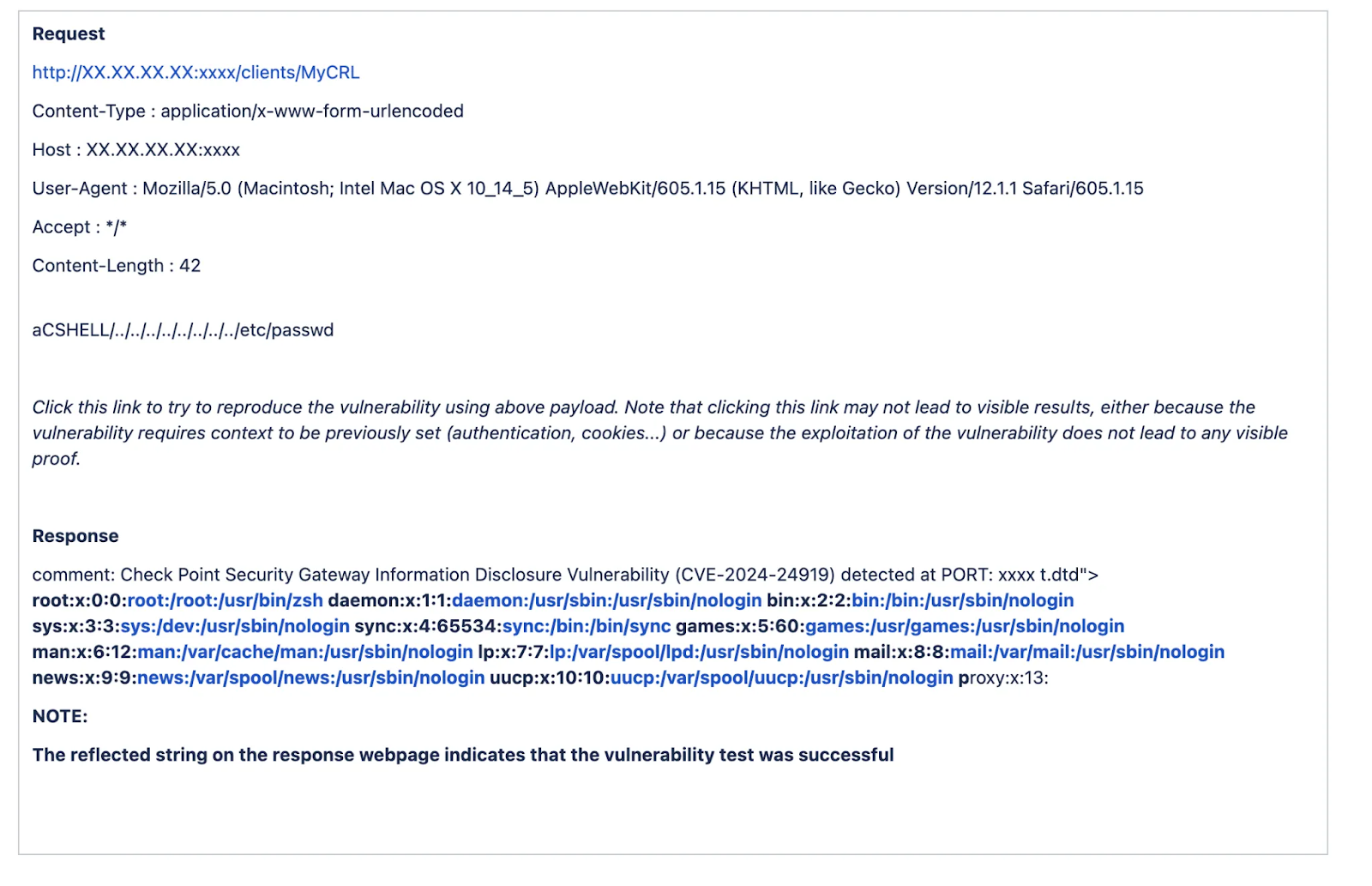
Example of a payload trying to access the etc/passwd file from Qualys QID (Source)
Exploited in the wild!
Vulnerabilities, even critical ones, can be very narrow in their scope and while often exploitation is technically possible, it can be difficult to find an allowing situation in the wild. This vulnerability however has been observed in the wild multiple times. Censys has observed tens of thousands of vulnerable instances.
“As of May 31, 2024, Censys observed 13,802 internet hosts exposing either a CloudGuard instance, Quantum Security, or Quantum Spark gateway.” Source
While this vulnerability was disclosed at my checkpoint on May 28th, it was being exploited as far back as April 7th nearly 2 months BEFORE any public notification of it. But since public notification, we have see a massive spike in exploitation in the wild as shown in this graph by Gey Noise
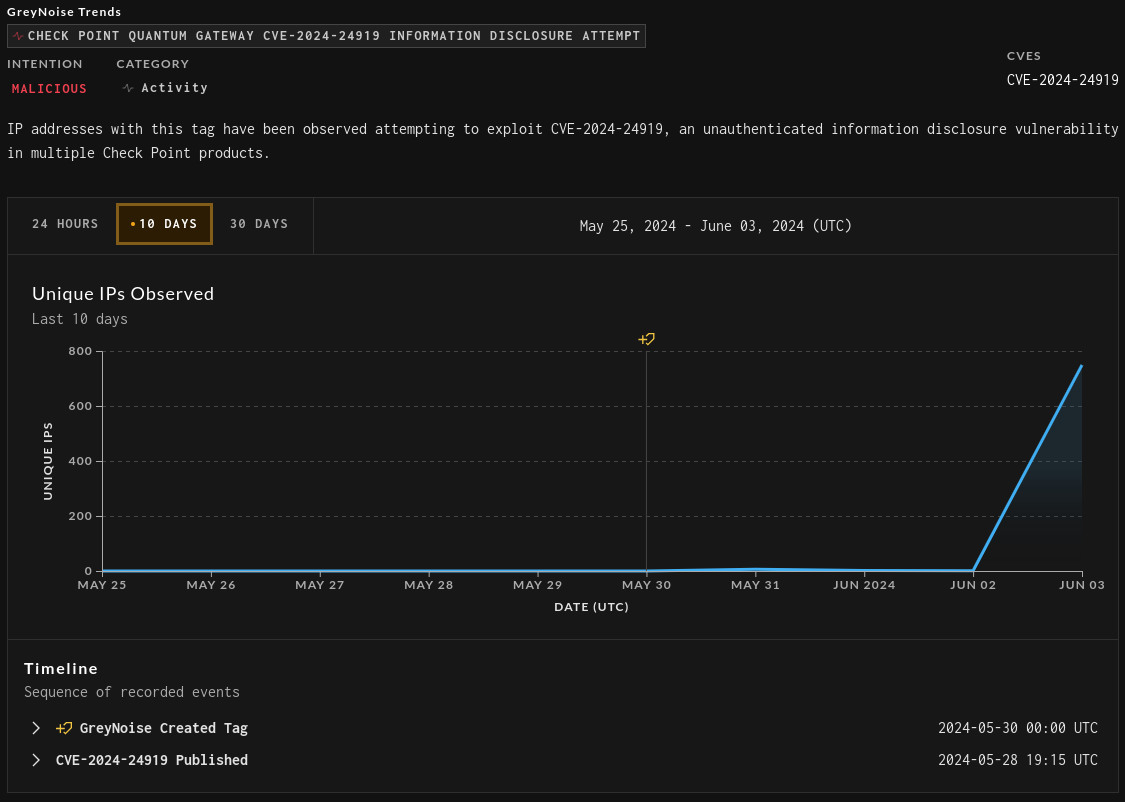
Part of the reason we are seeing this regularly exploited in the wild is due to the ease of exploitation. Watchtowr researcher described it as Extremely easy to exploit.
“wasn’t too difficult to find, and was extremely easy to exploit once we’d located it.” Source
How was the vulnerability discovered?
In this case, it was the vendor that actively disclosed the vulnerability (as opposed to a security researcher disclosing it). While the CVE outlined it as a critical vulnerability, no technical analysis of the vulnerability was issued (this is usually created by the researchers that discover the vulnerability).
The first technical writeup explaining the vulnerability and how to exploit it came from WatchTowr who used a technique called “Patch-Driffing” which essentially compares the patched system and vulnerable systems to expose what was changed and therefore what the bug was.
What should you do?
While this vulnerability does have a fairly wide blast radius, not all CheckPoint Security Gateways are affected. CheckPoint has issued a hotfix to solve the vulnerability for any affected systems, it is essential that if you use CheckPoint Security Gateways you check to see if you are affected and update to the latest version. More information from CheckPoint can be found here https://support.checkpoint.com/results/sk/sk182336










