In 2024, we face a big challenge with the rise of non-human identities (NHIs), including managing their secrets. Gartner says organizations typically have many more NHIs than human users (e.g., 10,000 NHIs for every 1,000 human users). As we look at the past 6 months, we see that there has been an increase in cyber attacks that involve the exploitation of NHIs such as secrets.
- Business intelligence company Sisense has seen secrets compromised in its GitLab repositories
- The New York Times had their entire codebase leaked
- Nation-state hackers accessed Microsoft source code and stole secrets
- Stolen Okta Auth tokens led to Cloudflare breach
Securing secrets in software development is a critical challenge. Exposing secrets—from source code to build systems, container images, and dev tools (like Slack, Jira, Confluence, Teams, etc.) —can let attackers compromise the software supply chain.
Organizations require a specialized end-to-end secrets security program as a part of their broader strategy for managing non-human (or machine) identities.
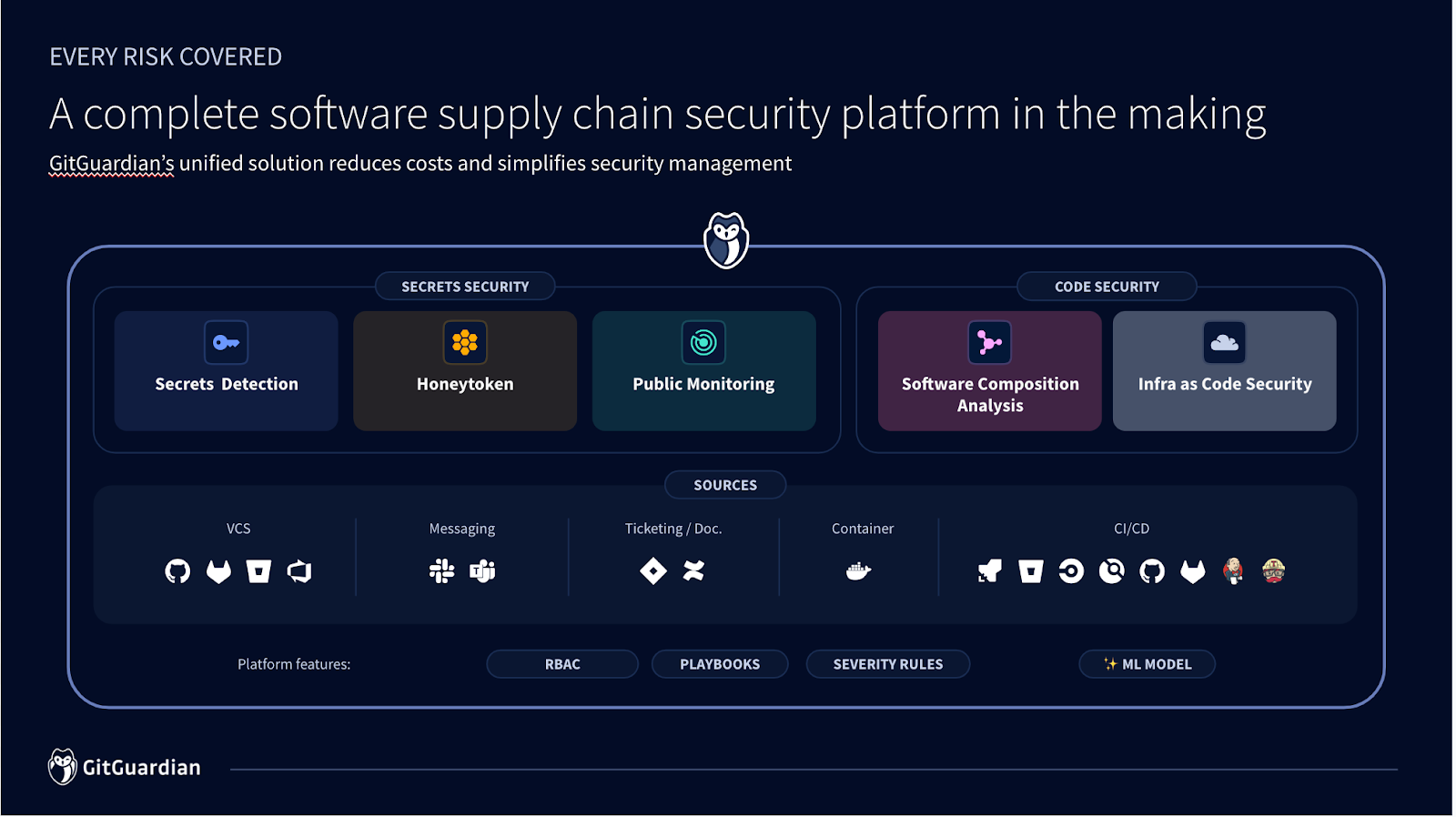
As we progress towards platformization, GitGuardian consolidates various secrets and code security capabilities into its unified platform. Our suite of tools addresses the extensive risks associated with secrets comprehensively:
- Our Secrets Detection product monitors repositories and other data sources for leaked secrets across SDLC components like code repos, CI/CD pipelines, dev tools, and more. Good internal hygiene is important to reduce the risk of accidentally exposing sensitive secrets in public spaces or during a breach.
- Our Public Monitoring product scans for leaked secrets in public spaces, including developers’ personal repositories, to safeguard corporate projects from any external threats.
- The Honeytoken product leverages deception techniques by planting decoy secrets to detect and alert on intrusions in the development pipeline.
2024 has been an exciting year so far, filled with major feature releases and improvements in these products. So we decided to do a half-year review reflecting on our product achievements. Here are some highlights:
Secrets Detection and Remediation
Detection
In line with industry trends, we have added and updated new specific detectors and validity checkers. Among the new detectors:
- Sentry (APM)
- Longchain (GenAI)
- OpenAI additional detectors (GenAI)
- Groq (ML inference)
- Sourcegraph (code search)
- Vercel (PaaS)
- Nx Cloud (CI)
- …
Each detector is linked to a specific page in our documentation. There you can find detailed information about the type of secret, its scope, and how to revoke it.
Challenge: Managing false positives
Organizations commonly struggle with false positives in secrets detection, leading to wasted time, increased stress, and potentially overlooking genuine threats. These false alerts can disrupt workflows and diminish the overall effectiveness of security measures.
Answer: 50% less false positives with machine learning
GitGuardian’s FP Remover is powered by an advanced machine-learning model that cuts false positives by 50%. This enhancement improves detection accuracy, allowing security and engineering teams to focus more on actual threats rather than sifting through incorrect alerts. FP Remover refines the detection process by intelligently filtering out false positives, ensuring that teams spend less time on false alarms and more on addressing real vulnerabilities.
Remediation
Challenge 1: Retrieving information more efficiently
Detection without remediation is just noise. Organizations often face delays in remediation due to the challenge of managing large volumes of alerts, leading to information overload and frustration. The process of manually configuring filters can be time-consuming and inefficient, particularly when users need to find specific information quickly.
Switching between different data perspectives often requires reselecting filters, which can be tedious and time-consuming. This can slow down productivity and create frustration, particularly when users need to access specific views frequently.
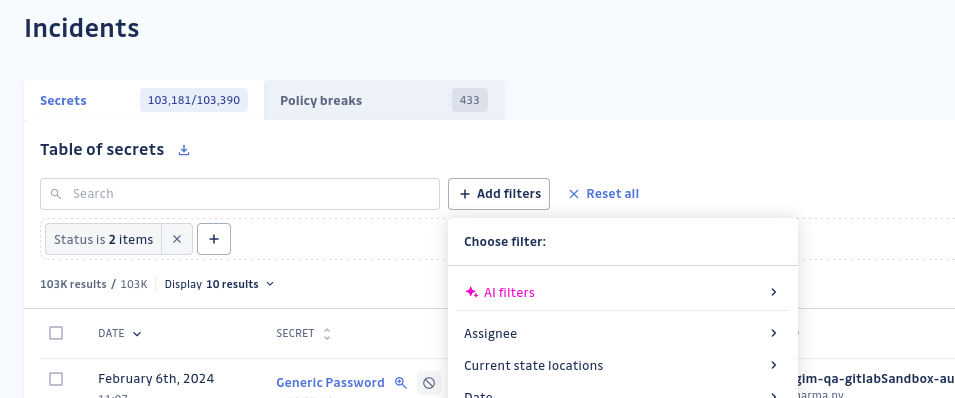
Answer 1: AI-powered filtering
Our AI-powered filters enhance the user experience by speeding up the use of existing filters across Incidents, Perimeter, and Audit Logs. This allows users to navigate large datasets more efficiently, improving usability and reducing time spent on filtering.
The AI filters translate user prompts into SQL queries, streamlining the filtering process. Users can provide feedback on the generated queries, allowing for continuous improvement and customization based on their needs.
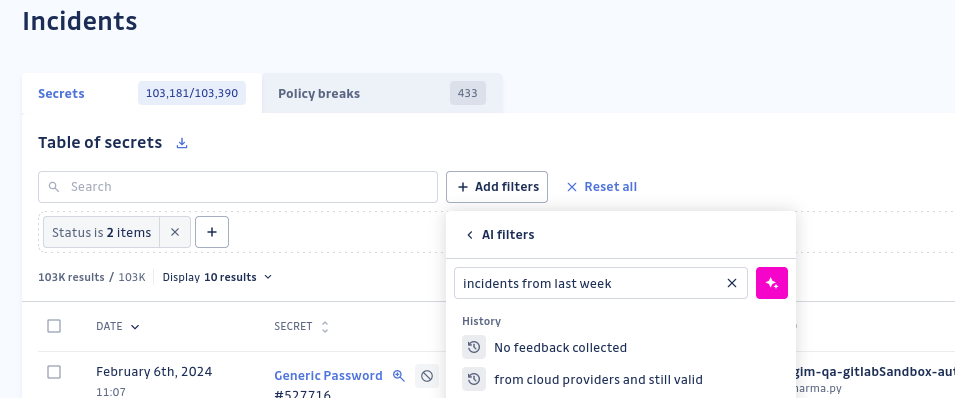
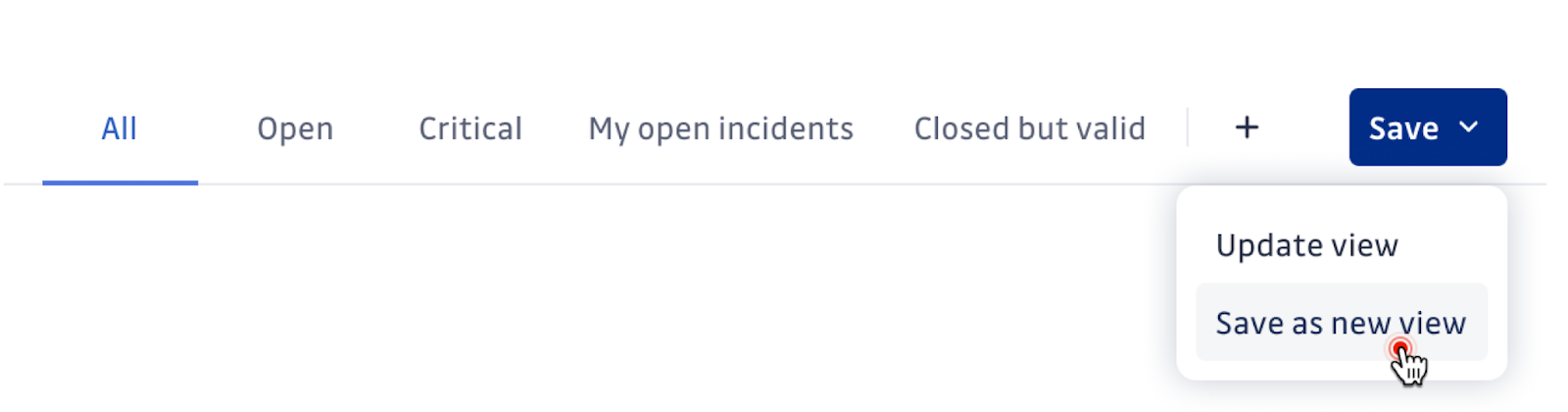
Answer 2: Enhancing productivity with "Saved Views’
The "Saved Views" feature allows users to save and quickly access their most frequently used filter sets. This eliminates the need to reconfigure filters each time, enhancing productivity and making it easier to switch between data perspectives.
Users can start with views recommended by GitGuardian, such as Open Incidents, Critical Incidents, My Incidents, and Closed but Valid. Also, we’ve introduced dynamic views that adapt to the person using them, such as “My Incidents.” Users can create private views for personal use, while workspace managers can create public views accessible to all members. This feature is available across Secrets Incidents, Perimeter, and Honeytoken pages.
Challenge 2: Streamlining remediation and collaboration
Secrets require an active remediation for code cleaning and rotation. Despite the importance of vaulting and rotating secrets, human error can still cause vulnerabilities, especially when developers hardcode credentials to quickly finish their tasks.
Organizations often face overwhelming volumes of security incidents, leading to information overload and inefficiencies in the remediation process. Security teams struggle to prioritize critical vulnerabilities, track progress, and collaborate effectively with development teams, slowing down the overall resolution of security risks.
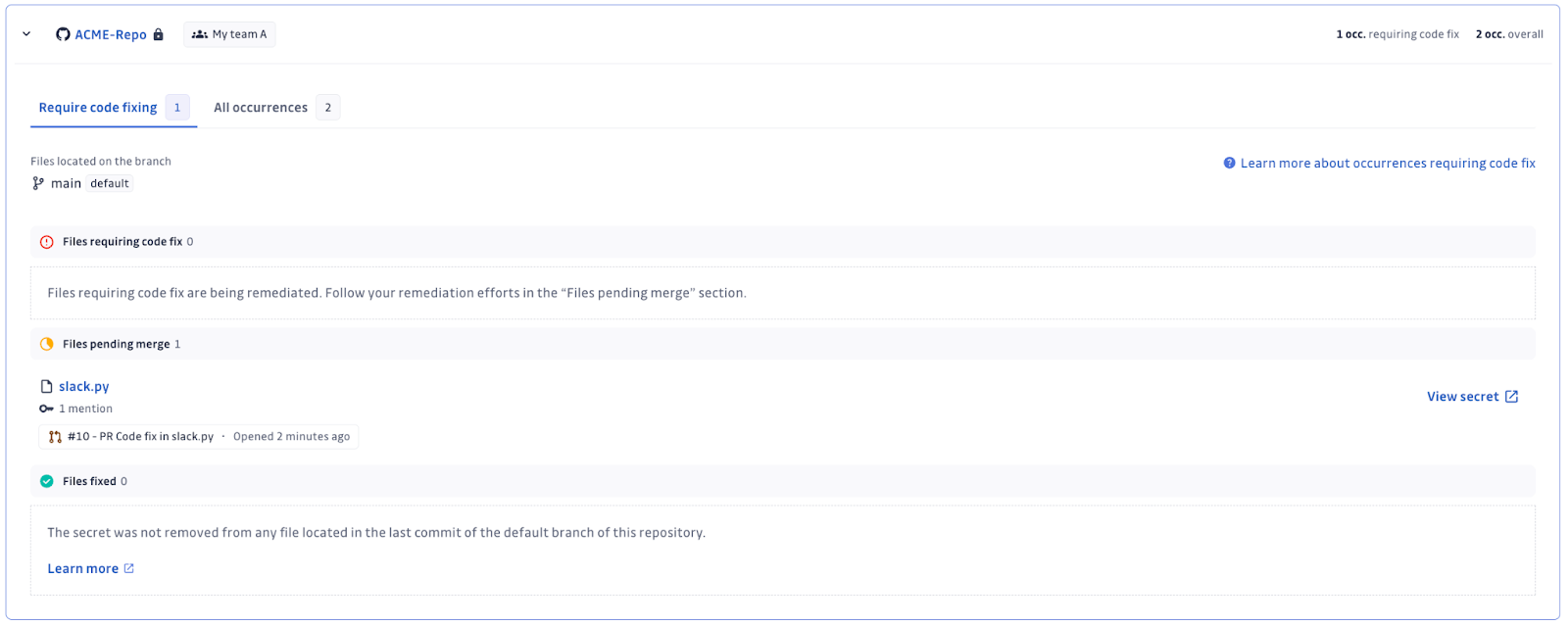
Answer 1: Code fixing with precise location data
The Remediation Tracking feature enhances GitGuardian's secrets remediation workflow by providing precise location information for code fixes. A new "Impacted Perimeter" section categorizes occurrences by source, isolates files that require immediate code fixing, and highlights specific files and lines of code on the default branch. This helps streamline the remediation process by focusing on critical areas needing attention.
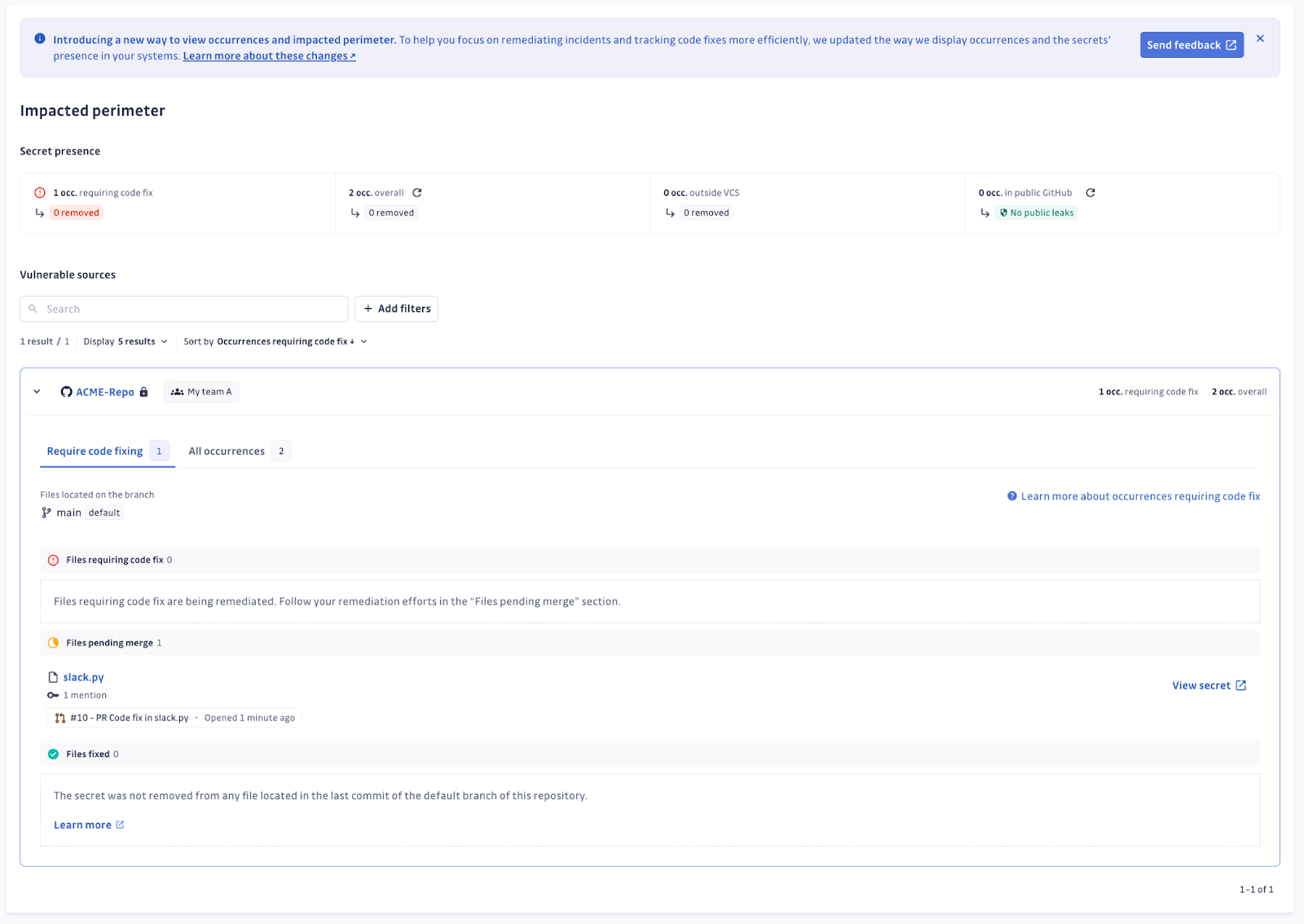
Answer 2: Granular tracking of code fixes in real-time
The feature also introduces real-time monitoring of remediation merge requests, offering comprehensive visibility into the progress of fixes. Users can track the status of files impacted, access relevant files and merge requests directly, and ensure that remediation efforts are on track, improving collaboration between incident managers and developers.
Answer 3: CyberArk Conjur Cloud integration
GitGuardian has integrated with CyberArk Conjur Cloud, providing a robust solution for detecting and managing exposed secrets. This integration enables security teams to detect leaks in public repositories and enforce secrets management policies effectively.
It also supports continuous monitoring to identify hardcoded secrets in the internal perimeter and triggers remediation processes.
By streamlining the detection and response to exposed secrets, this integration significantly reduces the time required to address these vulnerabilities, enhancing overall security while allowing developers to concentrate on their core tasks.
Honeytoken
Challenge 1: Manual honeytoken deployment
Deploying honeytokens manually across hundreds or thousands of code repositories is inefficient and impractical. Organizations need to monitor for unauthorized access or intrusions, but the manual process of creating and inserting honeytokens into each repository is time-consuming and resource-intensive. This challenge becomes even more pronounced as the number of repositories grows, making it nearly impossible to ensure comprehensive coverage without a streamlined approach.
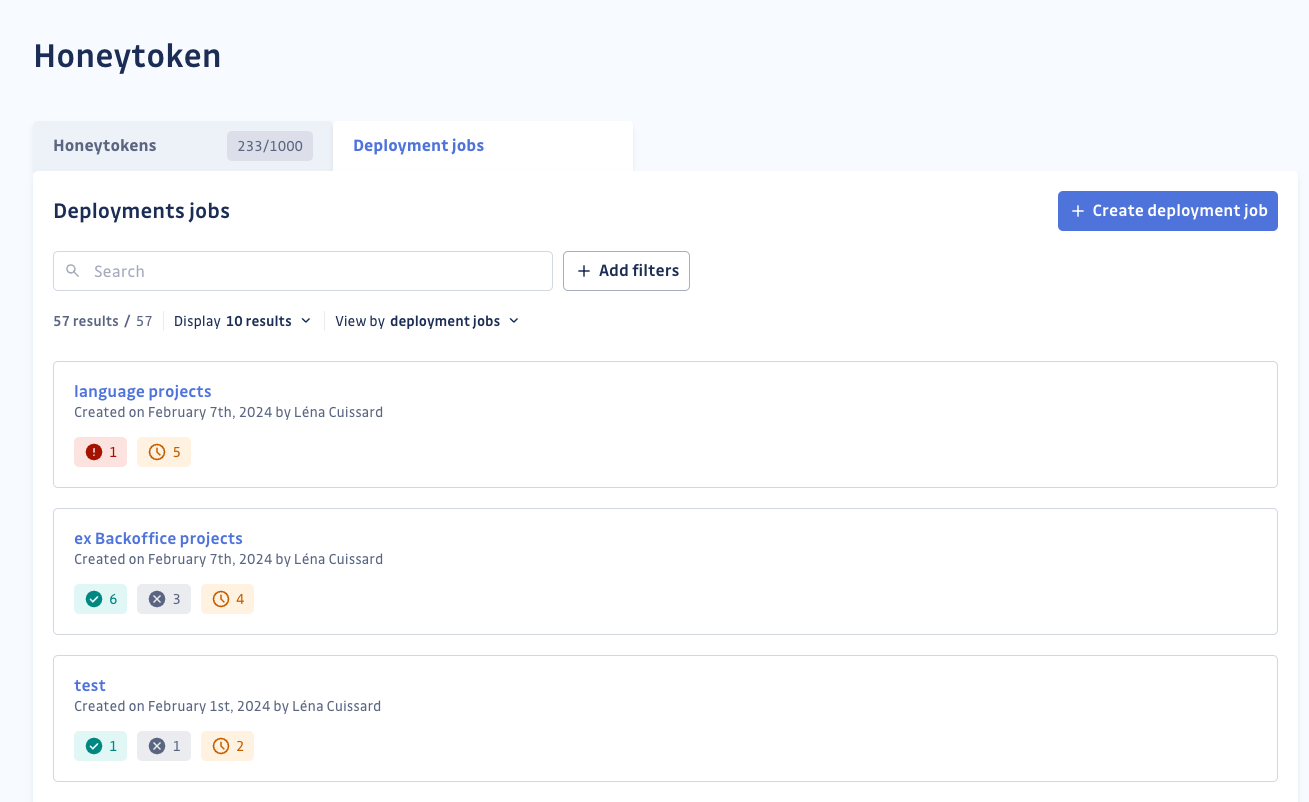
Answer 1: Efficient "deployment jobs"
The new “deployment jobs” feature introduces a semi-automated process for deploying honeytokens at scale. This feature allows users to create honeytokens, insert them into selected repositories, and generate pull requests to integrate them. By automating these tasks, organizations can efficiently deploy honeytokens across multiple repositories without any manual overhead.
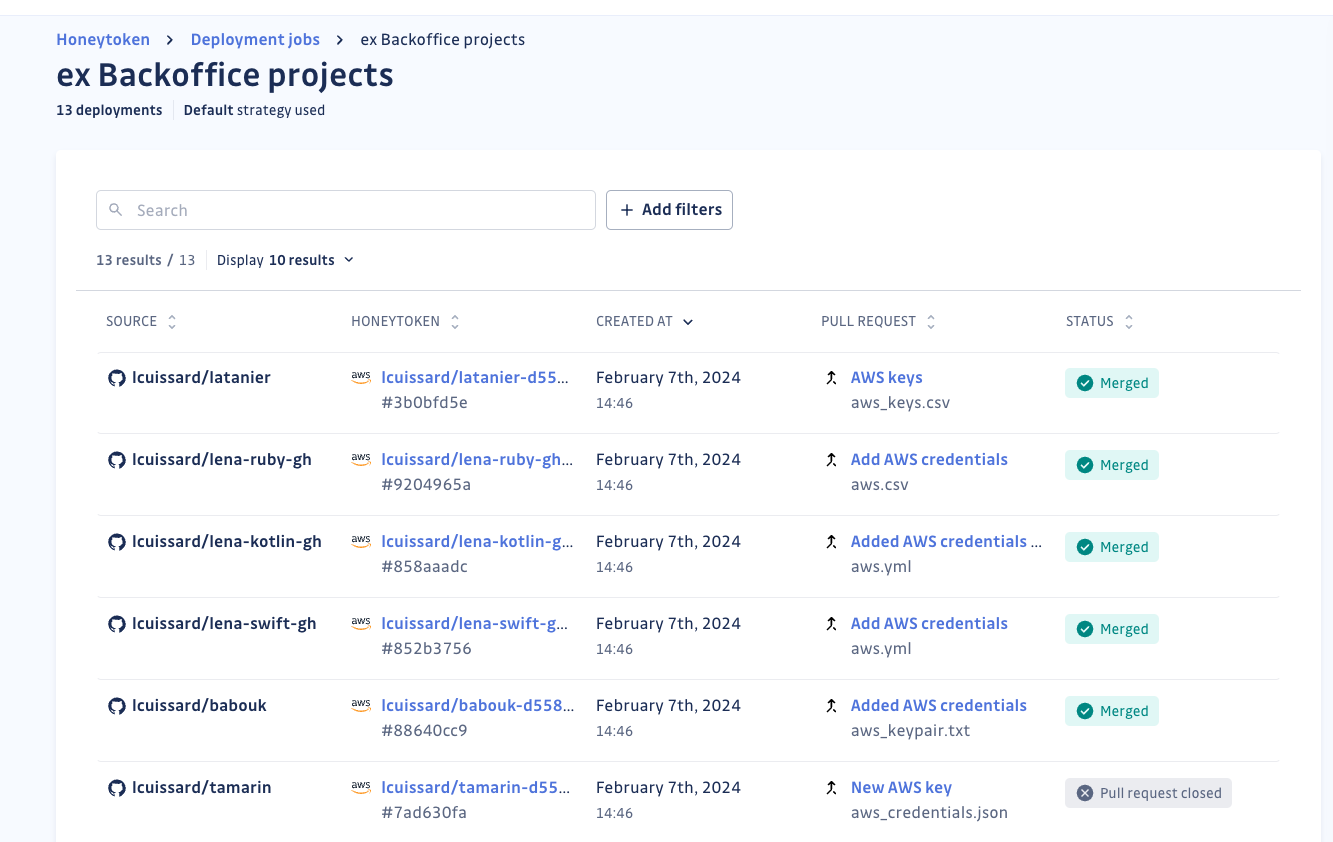
Answer 2: Flexible context creation
The feature supports the configuration of flexible context creation strategies, enabling users to define where honeytokens should be placed in their files. This provides flexibility to adapt to different repository structures and enhances the relevance of the honeytokens.
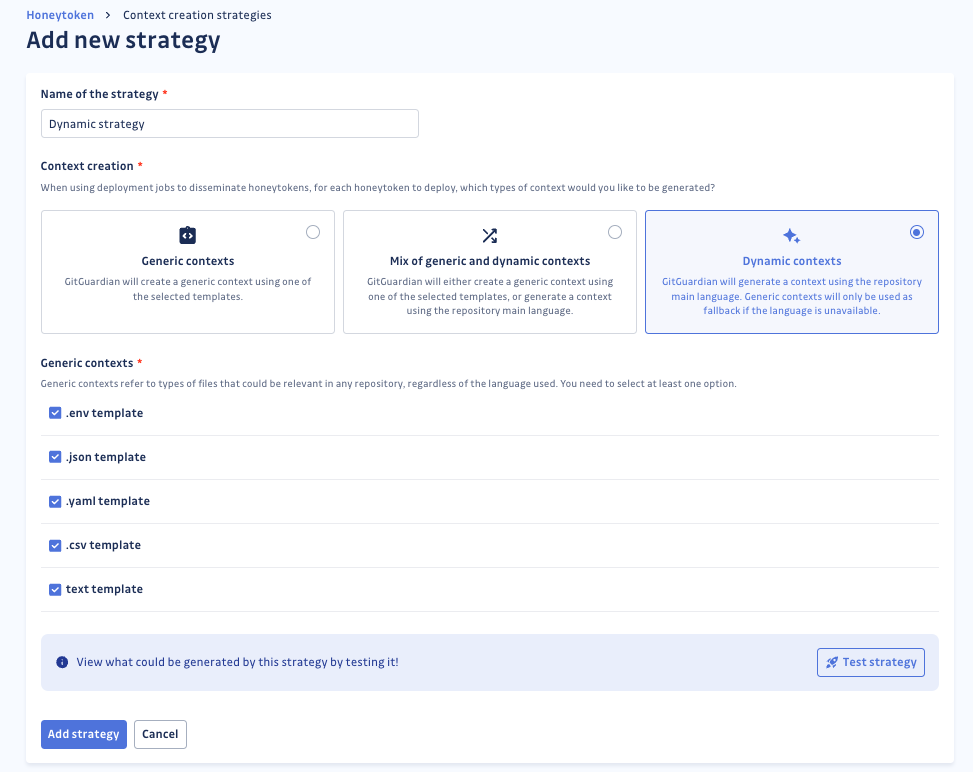
Public Monitoring
Challenge 1: Visibility of sensitive secrets and incident prioritization
Swiftly identifying and resolving what’s most relevant amid overwhelming data is a common challenge.
Organizations also face difficulties in prioritizing incidents due to a lack of visibility into all applicable severity rules. This can lead to inefficiencies in triaging and managing incidents, as users may not see the full picture of how different severity rules impact their incidents.
Answer 1: AI-prioritized tagging
At GitGuardian, we’re tackling this challenge head-on with pioneering AI-driven incident analysis. We have introduced a new AI-powered tag to enhance incident detection. This feature uses a machine-learning model to identify and tag the most critical incidents from the remaining data, with high precision and recall. This new tagging system helps users quickly focus on the most important and pressing issues, improving the efficiency of secret management and response.
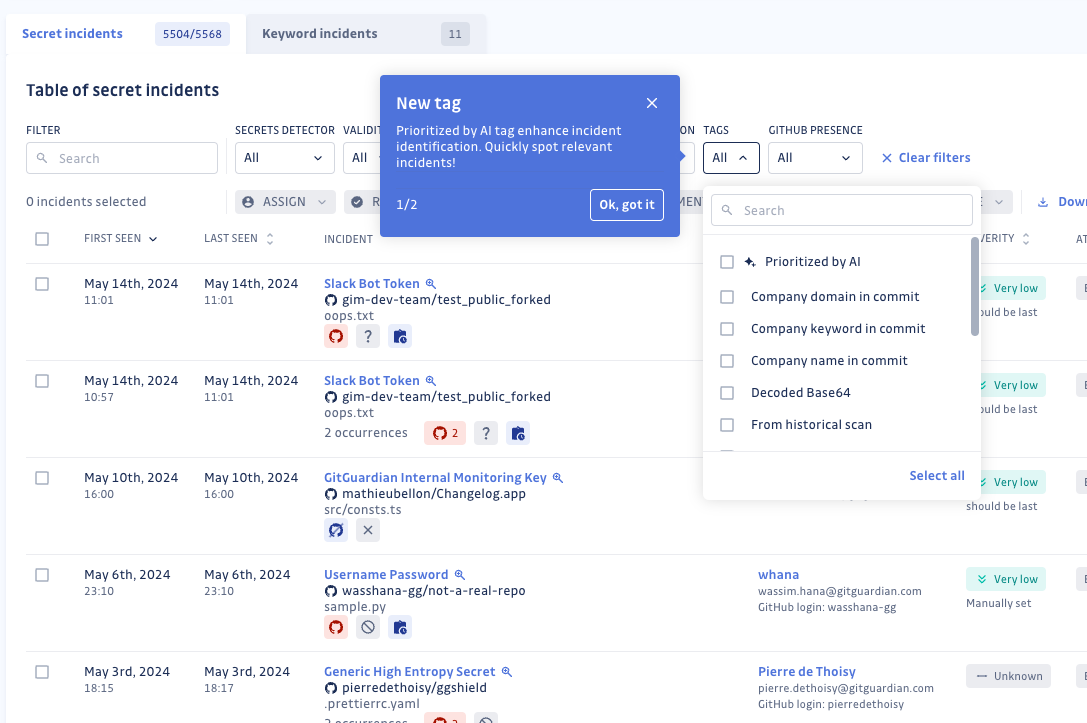
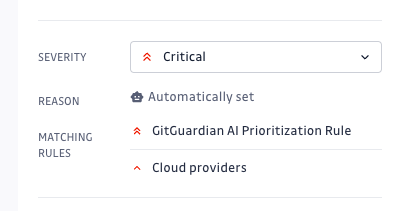
Answer 2: Enhanced severity rules display and filtering
We have enhanced the severity rules functionality by introducing two key updates. First, we now display all severity rules that match an incident’s metadata, while still applying the highest severity rule.
Second, we’ve added a severity rules filter on the GitHub secret incidents page, allowing users to view all incidents that match a selected rule. These updates improve incident triage and management by providing a more comprehensive view of severity rules and enabling more precise filtering.
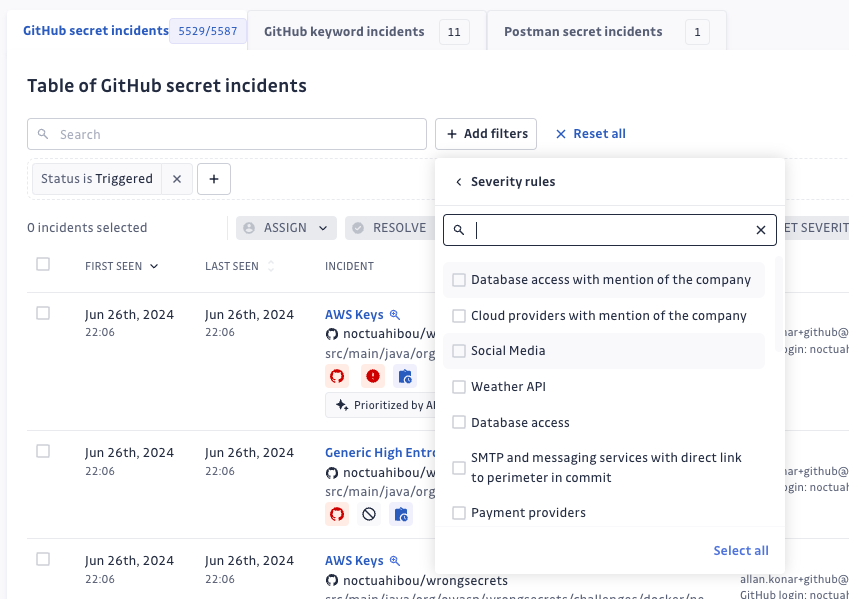
Challenge 2: Limited filtering options
Organizations often struggle with filtering data effectively due to limited options for specifying criteria. The current filtering system restricts users to broad or imprecise filters, making it difficult to retrieve specific information accurately.
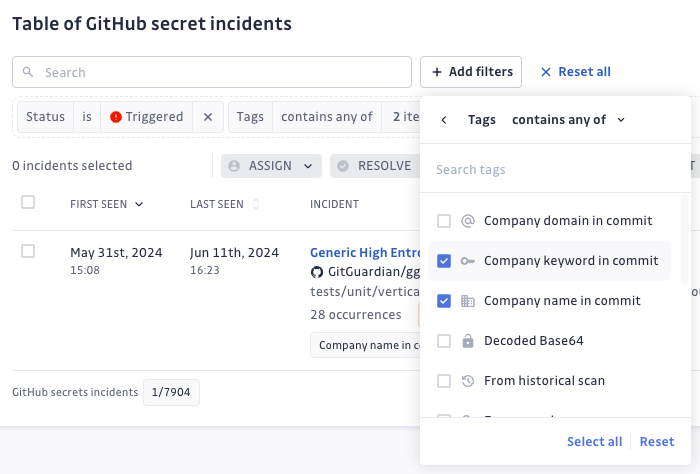
Answer 1: Enhanced filtering with operators
We introduced operators in the filters on the Incidents page. This update allows users to apply more precise and detailed criteria by using operators such as "is", "is not", "contains", and "does not contain". This enhancement improves the accuracy and flexibility of data retrieval, enabling users to refine their searches more effectively and efficiently.
What the remainder of 2024 holds for the GitGuardian
Our H1 product releases showcase our unwavering commitment to enhancing GitGuardian’s secrets security with advanced in-house machine-learning capabilities. These features will help you harden your software supply chain’s security posture, protect the secrets within, and improve your overall secrets security hygiene. Shoutout to all our valued customers, partners, investors, and the GitGuardian Team for being part of this journey and continuously propelling us forward!
As we step into H2, our pace will only quicken as we want to be the only platform that manages the full lifecycle of a secret. We are exploring new ways to enhance observability and lifecycle management for secrets, focusing on advanced approaches to centralize, rotate, and secure sensitive data and provide analytics to assess your secrets management maturity and risk.
Stay informed about our latest features, updates, and more by watching our public release notes and roadmap!
If you have any questions or feedback for our team, please write to your account manager or customersuccess@gitguardian.com.