Today, we're thrilled to unveil an exciting feature in your arsenal for early breach detection: Honeytoken Deployment Jobs. It's now easier than ever to leverage honeytokens for peace of mind during your lengthy secrets remediation processes. In this blog post, we'll explore how this new feature, requested by many of our users, can revolutionize the way you protect your code repositories.
What Are Honeytokens?
First things first, let's talk about honeytokens. These clever little decoy credentials do not grant access to customer resources or data instead act as digital tripwires, alerting you to potential security breaches and providing essential information about the attacker, such as their IP Address, User Agent, and Location.
With honeytokens strategically placed throughout your code repositories, your team gains peace of mind knowing that any unauthorized access attempts to your assets will be swiftly detected before they escalate. This newfound sense of ongoing safety will allow your team members to focus more on their core tasks, without constantly having to worry about potential breaches going undetected.
Read more about why you should use honeytokens in our blog post:

Creating honeytokens manually is always an option. This is useful, particularly in scenarios beyond traditional code repositories. Protect assets like your CI/CD environment, software artifact registries, project management tools, messaging apps, or even your developers' desktops. Once you've identified where you want to deploy your honeytoken, simply name the honeytoken, give it a description specifying its deployment location, add relevant labels, and voila! You'll receive the corresponding decoy AWS key, ready to be placed on the asset. If a breach occurs, the honeytoken will most likely be triggered, and you can rest assured that your repository's secrets are under vigilant watch.
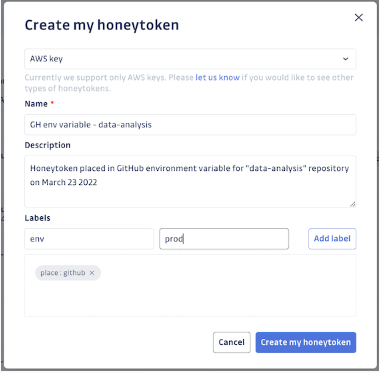
But what if you have hundreds, or thousands of repositories to protect?
Manually deploying honeytokens to each one would be a monumental task. That's where our new feature, Deployment Jobs, comes in handy. You can automate the creation and deployment of these virtual decoys across multiple private repos you are protecting with just a few clicks.
This automated deployment process provides broader coverage and takes the hassle out of deploying at scale. Simply select the repositories where you want to deploy honeytokens, and GitGuardian handles the rest. From creating and inserting honeytokens into relevant files to generating pull requests for seamless and efficient deployment, we've got you covered.
Seeing is Believing
Let's dive into the nitty-gritty of how Deployment Jobs make your deployment process easier than ever.
Prerequisites
Before diving into deployment jobs, there are a few prerequisites to keep in mind. Firstly, Deployment jobs are currently exclusively available for workspaces under a Business plan. Additionally, GitHub users require the “GitGuardian: write” GitHub app, which grants write access to the repositories being monitored. You can read the full documentation about the configuration of write permissions, including troubleshooting guidelines, in our public documentation.
Here is a step-by-step guide for creating your first Deployment Job:
Step 1: Access the Honeytoken dashboard in your GitGuardian workspace, navigate to the Honeytoken Deployment Jobs tab, and click on “Create deployment job.”
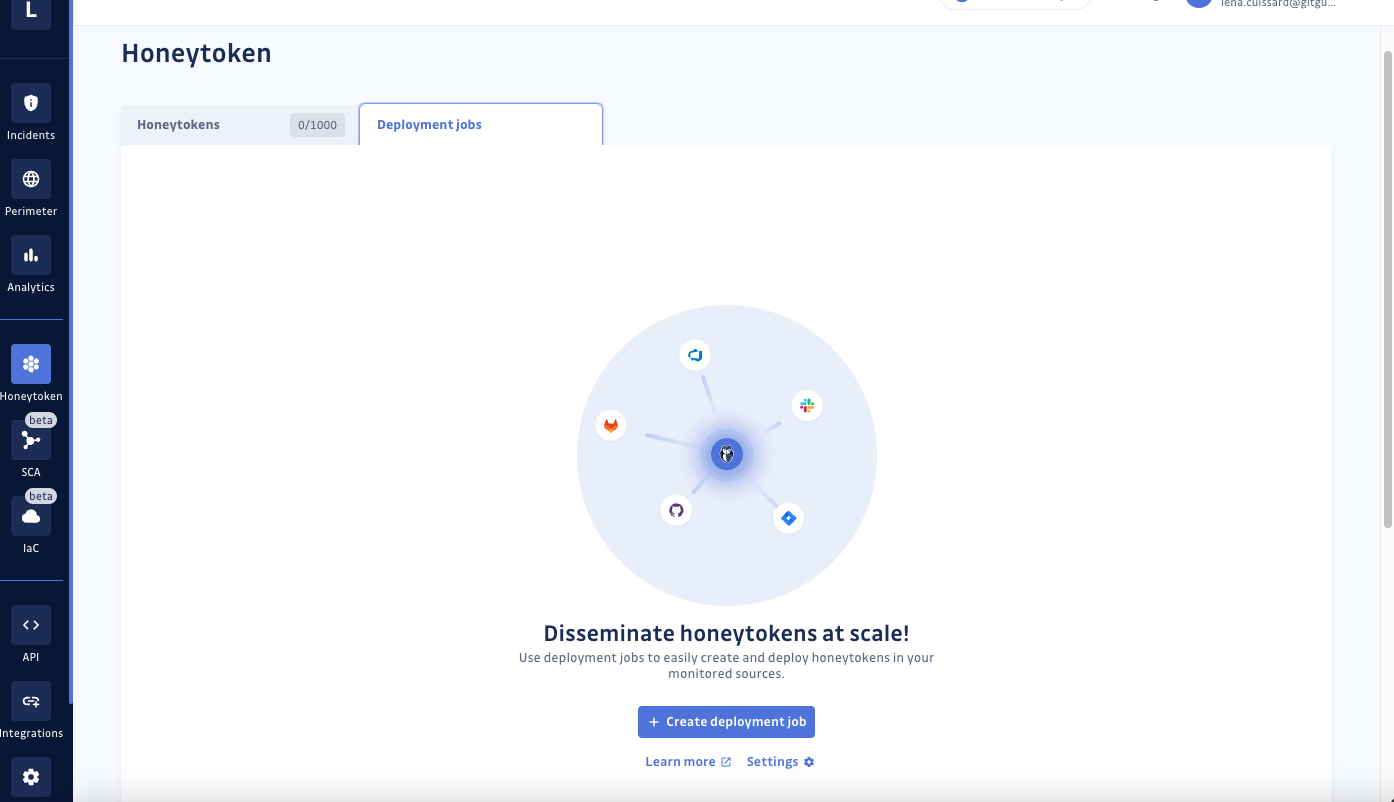
Step 2: Here’s where the magic happens:
a. Give your deployment job a descriptive name to indicate its scope or purpose.
b. Choose a strategy for the types of files to be used for honeytoken insertion.
c. Assign labels to the honeytokens generated for easy identification.
d. Select the “sources” or repositories where you want to deploy
honeytokens. We currently support GitHub, GitHub Enterprise, and GitLab.
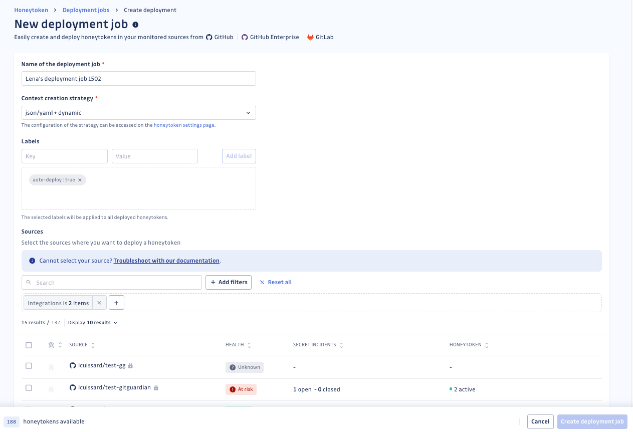
GitGuardian will automatically create honeytokens for each selected repository and create a pull request to insert them into relevant context files to the repository.
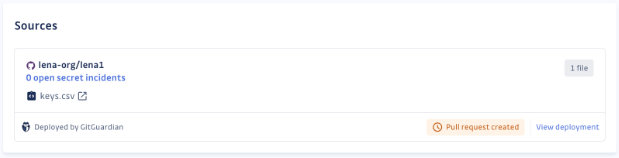
Step 3: Track its progress every step of the way. From pending pull requests to successful deployments, GitGuardian keeps you in the loop with real-time updates. And remember, a honeytoken is considered deployed as soon as the pull request is created, even if it’s not merged into the main branch. This means that repositories are immediately protected upon the creation of the pull request, providing an additional layer of security against unauthorized access attempts.
You will see that each honeytoken is named based on its respective source.
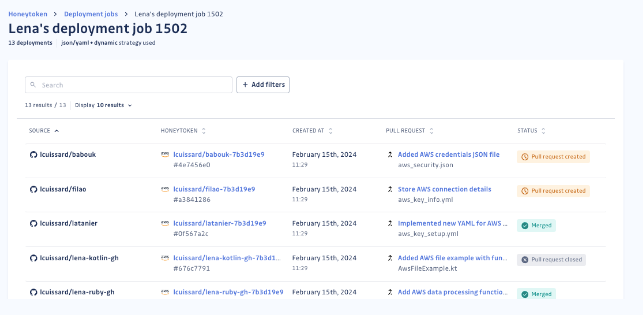
Step 4: Review the generated pull requests and merge them into the main branch. You can perform this directly in your VCS. We want our customers to decide whether to proceed with the merge. If you wish to modify the file's content or name, you can choose to simply close the pull request.
Step 5: Monitor the deployment status and activity of your honeytokens via our centralized dashboard.
Honeytokens created via deployment jobs have unique characteristics, including their name, labels, and deployment link. Each honeytoken is tailored to its source, making it easy to identify and manage across your repositories.
Secure your codebase with minimal time and effort
We understand the challenges of managing secrets sprawl effectively and the constant need to defend against intruders. So, we're committed to assisting you regardless of the size of your development team or the complexity of your codebase.
With GitGuardian Honeytoken Deployment Jobs, protecting your codebase is easier than ever. We trust that our simple guide will prove valuable as you integrate honeytokens with Deployment Jobs in your repositories. After deploying your first Deployment Job, you'll likely uncover some additional powerful use cases of our Honeytoken technology.
So what are you waiting for? Upgrade to the Business plan or sign up for a demo to discuss our Enterprise solution and let's start deploying honeytokens like a pro! We would be delighted to assist you in exploring our features every step of the way.
If you're not yet a GitGuardian Secrets Detection user, signing up not only helps you identify hardcoded secrets but also grants you 5 free honeytokens.
See upcoming sessions









