You must choose.
But choose wisely.
For as the True Grail will bring you life.
The False Grail will take it from you.
–Knight guarding the Holy Grail, Indiana Jones and the Last Crusade.

If you have not seen the third film in the Indiana Jones series, then SPOILER ALERT (for a movie that came out in 1989).
At the climax of Indiana Jones and the Last Crusade, our hero makes it past perilous traps and hazards on his quest to reach the Holy Grail, only to find a room full of dozens of drinking vessels. A knight guarding the holy relic explains that only one is the real grail and to choose wisely. We soon see what happens when you pick the wrong grail when the film's antagonist drinks from a false grail and rapidly turns to dust.

Placing multiple decoy grails in the way to keep bad actors from finding and exploiting your valuable credentials is at the heart of ggcanary, our open-source project that lets you quickly deploy honeytokens throughout your environments. While we can't help by turning bad actors into dust, we can help you stop them in their tracks with false grails secrets. And you can automate the whole process.
Protecting Your Holy Grail - Your Data And Servers
Malicious attackers are not going after a golden cup but your hardcoded credentials, which they can use to gain access to your valuable data and resources. We call those GitGuardian Canary Tokens, or ggcanary tokens for short, and you can deploy them right now for free to enhance your security. If you like webinars, you can check out the one we recorded about ggcanary.
In an ideal world, you would be able to stop all malicious attackers from ever getting through your defenses. But in all reality, given the nature of supply chain attacks and the high probability of misconfigurations occurring somewhere in our ever-growing DevOps environments, the odds are never truly zero that unauthorized actors will gain access to internal systems, including scripts, code, and configuration files.
Worse yet, if an attacker gains access to credentials, it is extremely difficult to immediately detect if they use those secrets. In retrospect, it can be clear when examining the logs that suspicious activity occurred on a data server; by that point, it is too late, as the data has already been compromised.
Honeytokens For the Defense of Your Software Supply Chain
One way to fight back against attackers is to set traps; false credentials that can trigger alerts when used. You might see these called honeytokens, canary tokens, canary traps, or honey credentials, among other names. If a honeytoken is used, not only will it not grant access, but it will also raise an alert that it has been invoked. Based on that alert, you can immediately act to stop the attack.
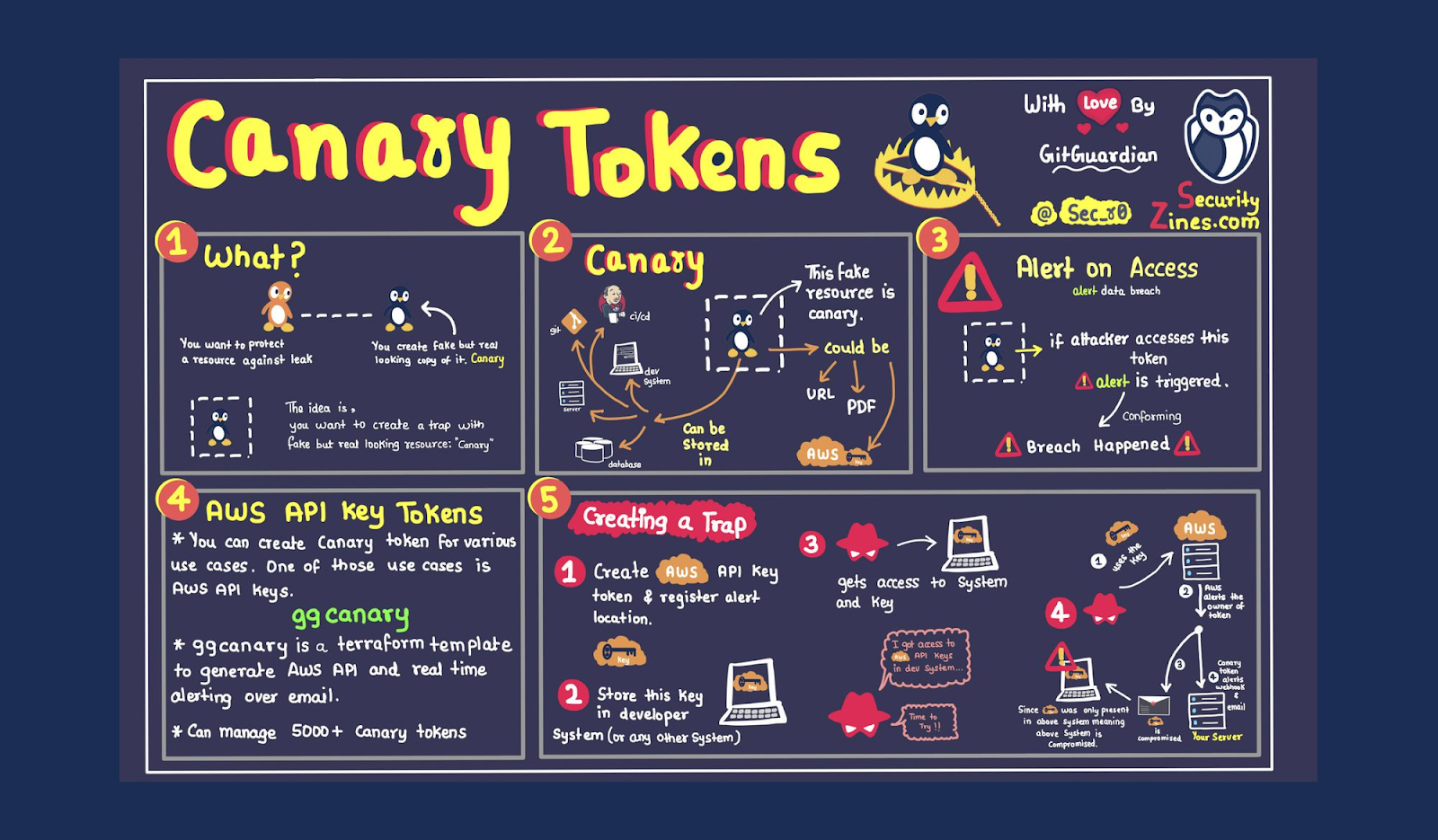
You might be familiar with the term honeypot, which is a closely related concept, and are wondering what the differences are. To put it simply, honeypots are typically entire servers or parts of a service designed to ensnare or mislead attackers. Honeytokens are generally not an entire system themselves, only tokens with specific characteristics that trigger specific behavior when used.
If a bad actor does gain access to an environment, you want to give them multiple false credentials to try, thereby increasing the likelihood of triggering an alert. Even if you are already consistently leveraging secrets managers like Hashicorp Vault or AWS Secrets Manager, you can still leverage Honeytokens by planting them as hardcoded plaintext credentials. Imagine an attacker getting access to an .env file that contains no real credentials, just false keys that set off alarm bells and lead you back to the source of the intrusion in seconds.
Approved users and systems won't even need to know that these honeytokens exist, as they will already have the correct credentials for their access. Only someone trying an attack and seeing what keys give access to what resources will likely fall into this trap.
Open Source
At GitGuardian, we strongly believe in open source, which is one of the drivers behind our projects like ggshield and sample_secrets, a repository to help with secret detection testing. We are very proud to make ggcanary open source as well.
ggcanary provides a simple Terraform configuration allowing you to create and manage GitGuardian Canary Tokens. These tokens can be deployed in multiple places along the software development lifecycle, SDLC. Tokens can be created and deployed in your code repositories, CI/CD pipelines, project management, and ticketing systems like Jira or even instant messaging tools like Slack.
Fortune And Glory Through Automation
Since ggcanary tokens are created by Terraform scripts, you can build GitGuardian Canary Tokens into any of your infrastructure as code, IaC, deployments. Automating the use of honeytokens, or any security tool is the best way to ensure consistent security throughout all of your environments.
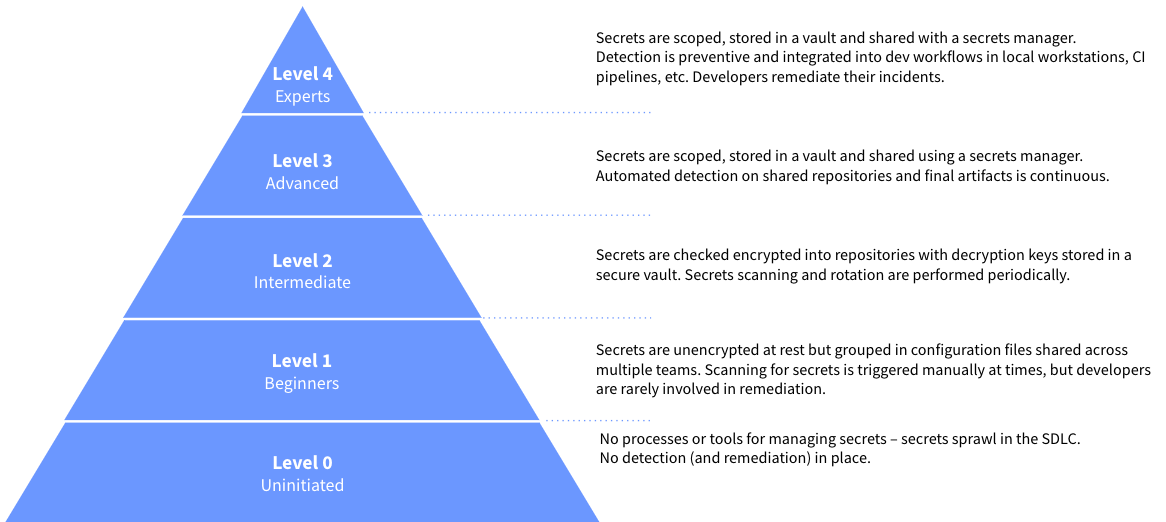
We see teams reaching the Expert level of Secrets Management Maturity consistently making use of tools for storing and accessing credentials as well as advanced automation for detection and remediation. Building in honeytokens is one more way to enhance your crusade for secrets management maturity.
Start The Engine
While we can't help you melt the faces off of malicious attackers trying to exploit your resources, we can help you on your quest to guard your holy grail, your true secrets. Good security means making it as hard as possible for attackers to succeed. While bad actors might never stop trying, we can set traps and act with expediency when tripwires are triggered.
We are committed to helping everyone improve their secrets management maturity. You can get started with ggcanary today completely for free. Combine honeytokens, such as ggcanary tokens, with the power of the GitGuardian Platform to detect and remediate incidents, and you can go down in history as a secret management expert.
The GitGuardian Honeytoken module is now available!
Read the release announcement for more information, and watch the demo to see what GitGuardian Honeytoken is all about.









