When you think about the fast-paced world of DevOps, there's a chance that container registries don't necessarily spring to mind first. But much like the often overlooked but crucial crew members on a well-oiled ship, container registries keep our development and deployment journeys sailing smoothly.
Container registries are essential for many development teams. They're where our Docker images, GitHub Container, and GitLab Containers are stored, ready to be pulled, and put to work whenever needed. However, just as we need to secure our codebases and CI/CD pipelines, these storage spaces also require a solid lock to prevent unwanted intruders.
In this post, we're turning the spotlight to GitGuardian's Honeytoken, a clever tool designed to keep our container registries secure by acting as digital decoys that alert us to any unsolicited activity. It's like a silent alarm system, watching over your precious images, ready to sound the alarm if an unauthorized hand tries to reach in.
In the following sections, we will dive into the world of honeytokens, understand how they work, and learn how to use them to secure our Docker Registry, GitHub Packages, and GitLab Container Registry. So, buckle up as we set out on a journey to fortify our registries and ensure smooth and secure sailings.
Understanding Honeytokens
Honeytokens are like digital breadcrumbs sprinkled throughout your systems, but instead of attracting birds, they lure potential cyber attackers. These seemingly valuable data pieces bait unauthorized users, effectively tricking them into revealing their illicit activity.
Each honeytoken is a unique piece of data, often resembling a real credential or secret that an attacker might find useful. However, unlike actual credentials, honeytokens are monitored by systems like GitGuardian's Honeytoken module, ready to raise the alarm when used.
Now, why would we want to use honeytokens in our container registries? Container registries like Docker Registry, GitHub Containers, and GitLab Container Registry are treasure troves of valuable assets that are vital to our development processes. Any unauthorized access to these assets could be catastrophic, making these registries a prime target for cyber attacks.
By placing honeytokens in these registries, you can create a security alert system that lets you know as soon as someone unauthorized has accessed it. It's like having a security guard who never sleeps, constantly watching over your stored artifacts and ready to alert you at the first sign of trouble.
So now that you understand what honeytokens are and how they can help secure your container registries, you might wonder, "How do I create a honeytoken?" The good news is, creating a honeytoken with GitGuardian is as easy as pie! Check out this step-by-step guide to get ready in under 5 minutes:
Once you've got your honeytoken, you'll be ready to start bolstering the security of your container registries. Let's dive into that.
Securing Docker Registry with Honeytokens
Docker, a prevalent name in the world of software development, offers a platform for automating the deployment, scaling, and management of applications using containerization. Docker Registry, a component of Docker, is a storage and distribution system for named Docker images. These images, essentially read-only templates used to create Docker containers, can carry vital components of your applications.
Now, let's bring honeytokens into this mix to secure our Docker Registry. How do we do this? By placing honeytokens within Docker images and pushing them to Docker Registry. Here's how you can do it:
- First things first, ensure that you have a honeytoken ready. If not, create one using GitGuardian's Honeytoken module.
- Next, you're going to insert this honeytoken into a Docker image. This can be done by including it in your Dockerfile, which Docker reads to build an image. Insert the honeytoken as an environment variable using the ENV instruction in the Dockerfile:
FROM python:3.7-slim
WORKDIR /app
# Set environment variables
ENV AWS_ACCESS_KEY="xxxxx"
ENV AWS_SECRET_KEY="xxxxx"
# Remaining Dockerfile instructions...Remember, the environment variables are just placeholders. Replace them with your actual honeytoken values.
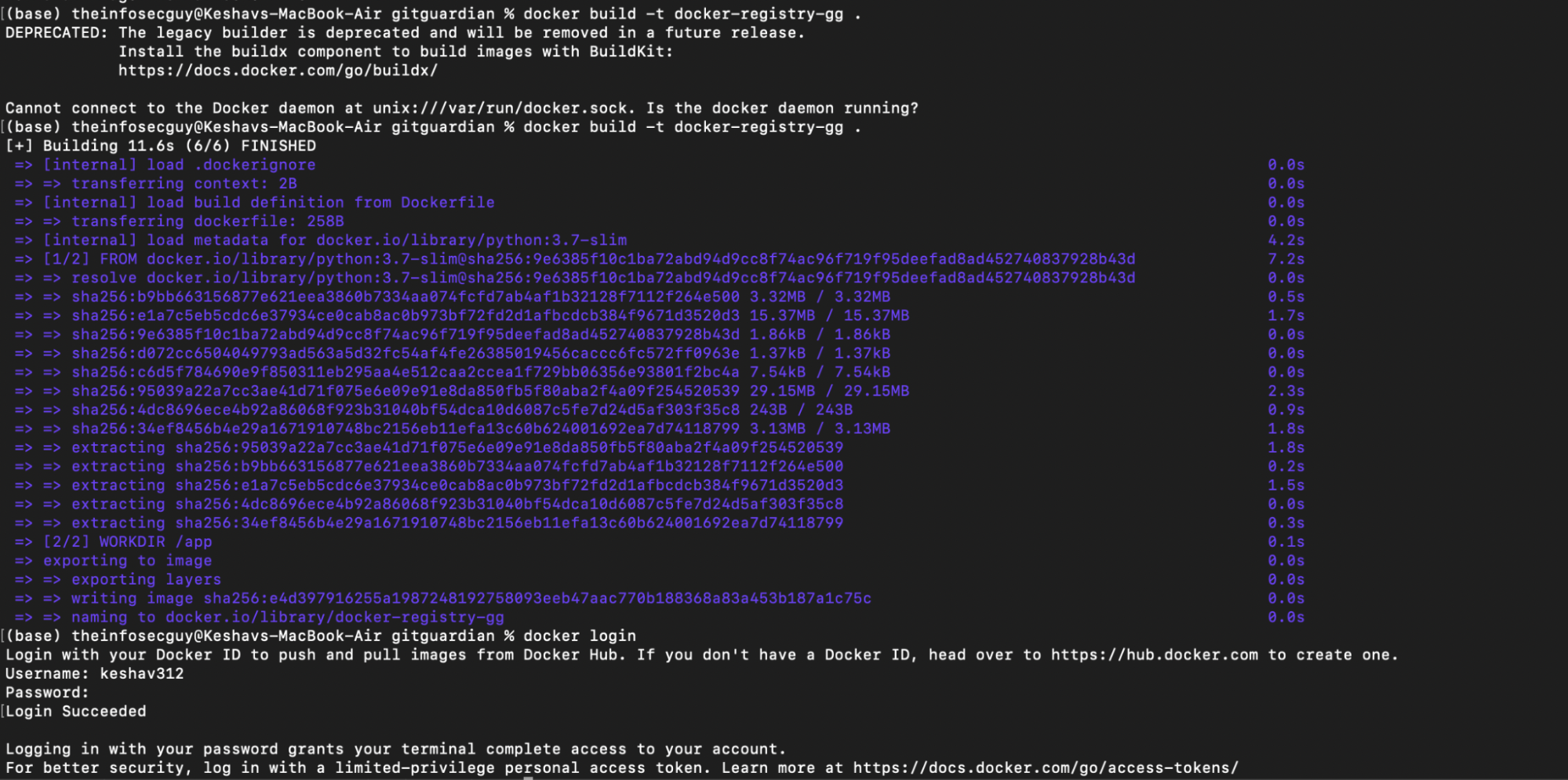
After Dockerfile is set, build the Docker image with the command:
docker build -t your-image-name .
Next, you need to authenticate to the Docker Registry:
docker login
After successful authentication, you can push the Docker image to the registry with the following:
docker tag your-local-image your-username/your-docker-image:latest
docker push yourusername/your-docker-image:latest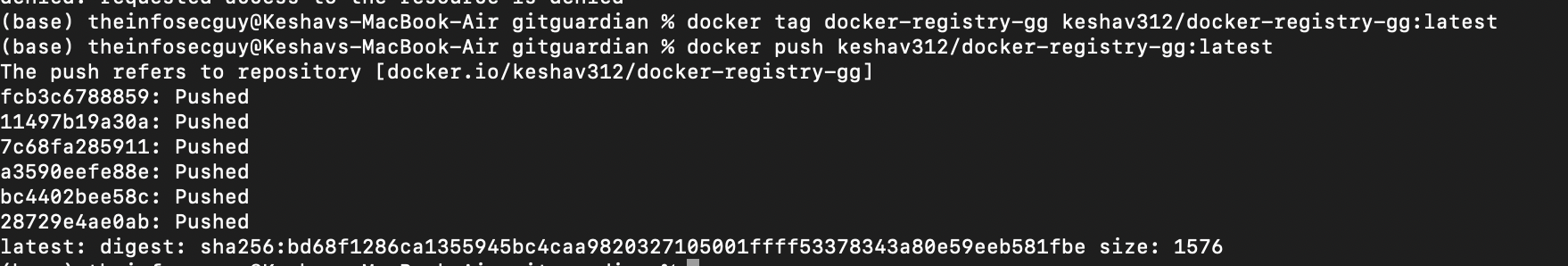
And there you have it! Your Docker image, equipped with a honeytoken, is securely stored in your Docker Registry. Any unauthorized access to this image will trigger the honeytoken, alerting you immediately.
This method lets you strategically place honeytokens in multiple images, forming a vigilant security shield around your Docker Registry. Up next, let's discuss securing GitHub Packages with honeytokens.
Also Read: How to Handle Secrets in Docker
Securing GitHub Container Registry with Honeytokens
The GitHub Container Registry allows you to seamlessly host and manage Docker container images in your GitHub repositories. Like with Docker Registry, you can add an extra layer of protection by integrating honeytokens into your Docker images. Let's go through the process step by step:
Preparing Your Dockerfile
To start, you'll need a Dockerfile with a honeytoken embedded. Here's an example Dockerfile, where the honeytoken is placed as an environment variable:
FROM ubuntu:latest
ENV AWS_ACCESS_KEY="xxxxx"
ENV AWS_SECRET_KEY="xxxxx"
# Remaining DockerfileBuilding Your Docker Image
After your Dockerfile is prepared, you can build your Docker image:
docker build -t ghcr.io/your-username/your-docker-image .
Replace your-username and your-docker-image with your GitHub username and desired image name.
Authenticating with GitHub Container Registry
To push an image to the GitHub Container Registry, you need to authenticate using a personal access token with the appropriate scopes. Create a new personal access token and select the write:packages scope. You can do this from your GitHub account's settings.
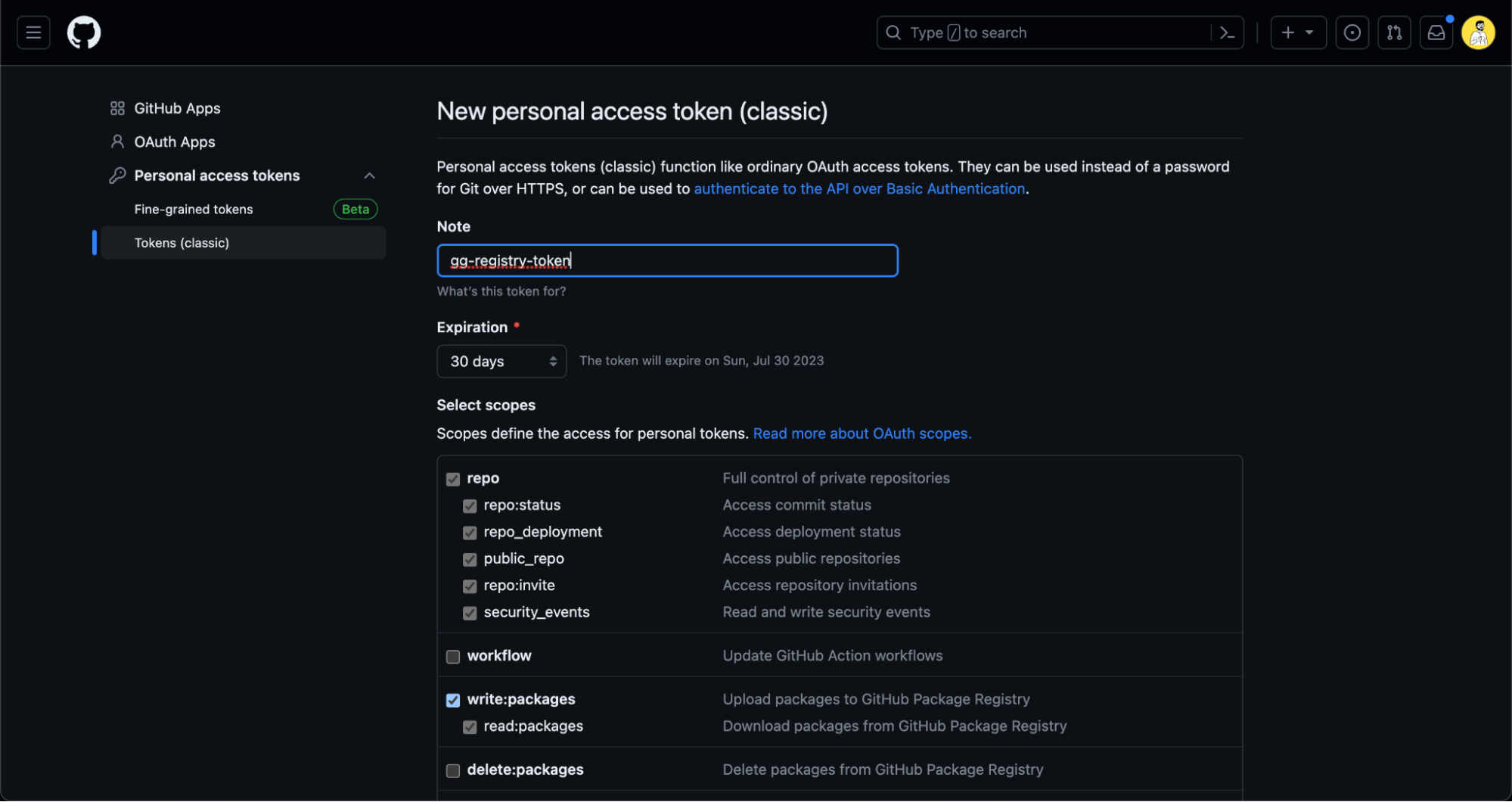
Next, save this token as an environment variable in your terminal:export CR_PAT=YOUR_TOKEN
Remember to replace YOUR_TOKEN with your actual token. Then, you can log in to the GitHub Container Registry:echo $CR_PAT | docker login ghcr.io -u your-username --password-stdin
Replace your-username with your actual GitHub username. If successful, you should see Login Succeeded.
Pushing the Docker Image
After you're logged in, you can push your Docker image:
docker push ghcr.io/your-username/your-image-name:latest
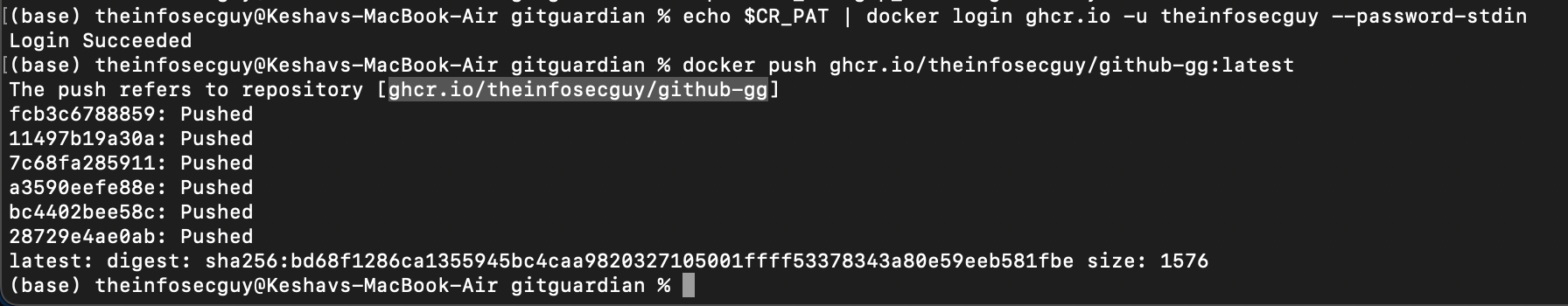
Congratulations! You've just added a honeytoken to your Docker image and pushed it to the GitHub Container Registry. If someone unauthorized tries to access this image, the honeytoken will immediately alert you. This way, you've strengthened the security of your GitHub Container Registry.
Let's move on to securing GitLab Container Registry with honeytokens next.
Securing GitLab Container Registry with Honeytokens
In GitLab, you can utilize the built-in Container Registry to host Docker container images for your projects. Similar to GitHub and Docker, you can strengthen your security by incorporating honeytokens into your Docker images. This section will guide you through the process:
Preparing Your Dockerfile
You start with a Dockerfile that contains an embedded honeytoken. Let's say you are adding the honeytoken as an environment variable in your Dockerfile:
FROM ubuntu:latest
ENV AWS_ACCESS_KEY="xxxxx"
ENV AWS_SECRET_KEY="xxxxx"
# Remaining Dockerfile instructions...Building Your Docker Image
Next, build your Docker image using your Dockerfile:
docker build -t registry.gitlab.com/your-namespace/your-project/your-image .
Replace your-namespace, your-project, and your-image with your GitLab namespace (username or group), your GitLab project, and your desired image name, respectively.
Authenticating with GitLab Container Registry
To push an image to GitLab's Container Registry, you need to authenticate with the registry. You can do this by logging in to Docker with your GitLab credentials:
docker login registry.gitlab.com -u your-username
Replace your-username and enter your password once prompted your-password. If you have two-factor authentication enabled, you'll need to use a personal access token instead of your password.
Pushing the Docker Image
After you've successfully logged in, you can push your Docker image to GitLab's Container Registry:
docker push registry.gitlab.com/your-namespace/your-project/your-image:latest
Again, replace your-namespace, your-project, and your-image with your GitLab namespace (username or group), your GitLab project, and your Docker image name, respectively.
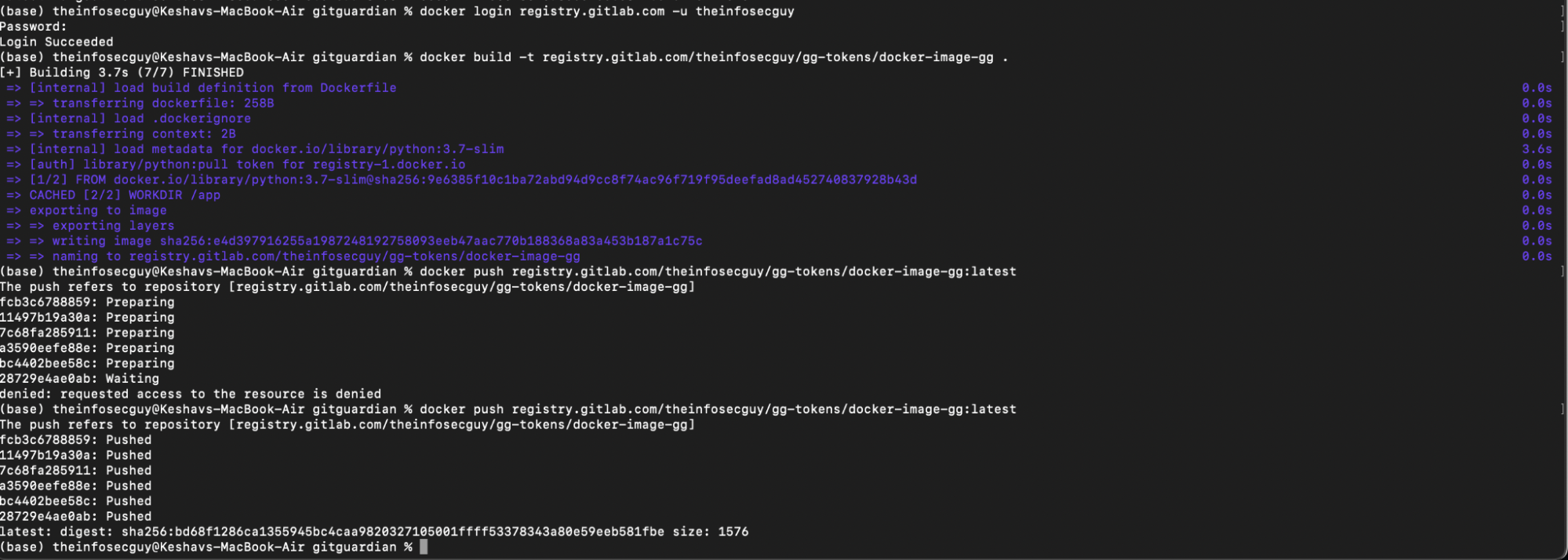
And that's it! You've successfully added a honeytoken to your Docker image and pushed it to GitLab's Container Registry. If an unauthorized party attempts to access the image, the honeytoken will be triggered, and you'll be notified. You've effectively fortified the security of your GitLab Container Registry.
In the next section, we'll wrap up the guide and discuss some additional measures you can take to secure your container registries.
Best Practices for Using Honeytokens in Container Registries
Implementing honeytokens in your container registries is a robust measure toward securing your DevOps pipeline. However, as with any tool, its efficacy lies in its proper utilization. In this section, we will explore a few tips and recommendations to get the most out of your honeytokens:
- Strategic Placement: The placement of your honeytokens is crucial. Remember, these are digital tripwires meant to be triggered by unauthorized access. Position them in sensitive areas of your registries or within your Docker images where they are likely to be discovered during illicit activity.
- Use Separate Tokens: Don't just use one token for every environment. Deploy different tokens for every service or environment. This process will help in tracing back the incidents & will reduce the time to detect & mitigate.
- Monitor Your Honeytokens: Honeytokens are only as good as your ability to respond when they're triggered. Ensure you have a robust monitoring system in place, and ensure that alerts from honeytokens get the highest priority.
- Use with Other Security Measures: While honeytokens are powerful, they shouldn't be your only line of defense. Combine them with other security measures like firewalls, access controls, and intrusion detection systems to create a comprehensive security strategy.
Incorporating honeytokens into your security protocols can greatly enhance the protection of your container registries. Remember, the goal isn't necessarily to prevent every single breach but to detect and respond to them swiftly when they occur. With a well-implemented honeytoken strategy, you'll be well-equipped to meet that goal.
Conclusion
As we navigate through the dynamic world of digital transformations, the role of securing container registries has become a paramount concern. Undeniably, it's an essential cog in the wheel of a robust DevOps pipeline. With GitGuardian's Honeytoken, it's possible to weave an extra layer of security into your system - one that doesn't just passively defend but actively alerts you about any unauthorized attempts at access.
Think about Honeytoken as an innovative approach to fortifying your DevOps ecosystem. By seamlessly integrating honeytokens into your pipelines, you'll be notified of security breaches faster than ever before. This proactive strategy can significantly enhance your responsiveness to potential threats, thereby elevating the overall resilience of your operations.
As we reach the end of this guide, it's time for you to embrace the proactive protection offered by GitGuardian's Honeytoken. Consider this an invitation to upgrade your container registry security and experience the tangible difference it makes. With GitGuardian Honeytoken, you aren't just defending your DevOps pipeline - you're arming it. Ready to get started? Your journey towards more secure DevOps begins here.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.