Honeytokens enable live intrusion detection by planting decoys that alert security teams when accessed. Implementing fake credentials, unused code blocks, SSH keys, and more turns cybersecurity proactive. Adopting a zero-trust approach with honeytokens secures pipelines.
Traditional Pipeline Security Limits
A lot of organizations today heavily rely on perimeter-based security technologies like identity and access management (IAM) systems, virtual private networks (VPNs), firewalls, and cloud security posture management (CSPM) tools to protect their software development lifecycle (SDLC).
However, the primary challenge with these perimeter solutions is their reactive nature—security teams only receive alerts after an incident has occurred. As a result, the perimeter can be bypassed using stolen login credentials or successful phishing attacks, etc.
To overcome these limitations, organizations can adopt a zero-trust security model along with proactive technologies like honeytokens. Zero trust mandates strict identity verification for every person and device attempting to access resources, regardless of whether they are inside or outside the network perimeter.
Honeytokens, which encompass fake credentials, access keys, decoy accounts, and other traps embedded throughout IT infrastructure and codebases, immediately alert security teams when cybercriminals interact with them. This provides real-time visibility into breaches before lateral movement occurs.
When you look at the SDLC as a whole, there are multiple places where you can embed honeytokens in various formats, which we are going to explore in this article.
Code Repositories
Code repositories are often targeted in cyber attacks, so placing honeytokens like fabricated AWS API keys can help organizations set traps for attackers. These traps could look like valuable credentials and alert the security team when accessed or used.
To give you an example, organizations could add a file named aws_credentials.txt to their code repository containing honeytoken AWS API keys.
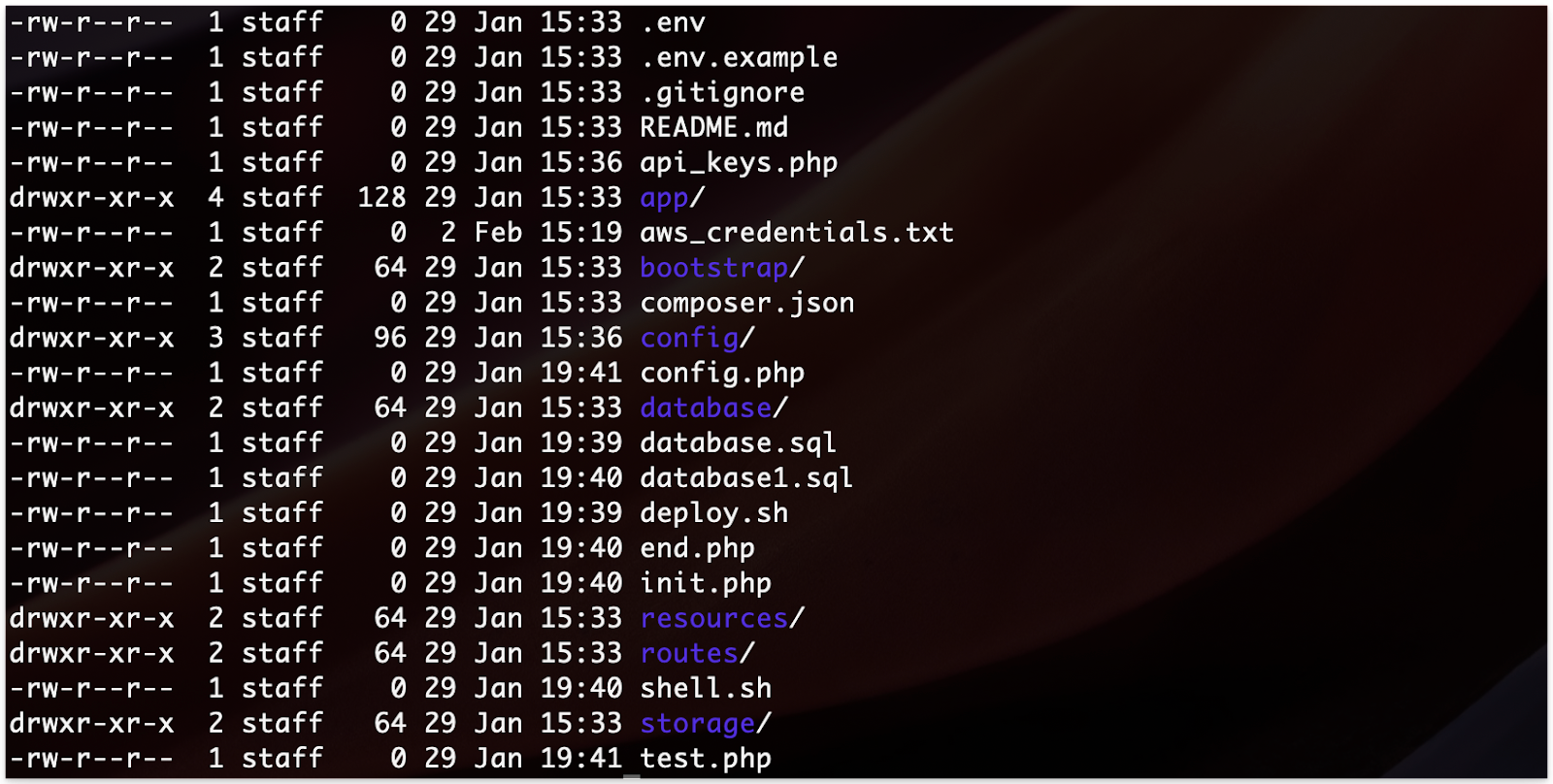
In the event of an attacker trying to utilize these fraudulent keys, the honeytoken service will send an immediate alert to the security team.
Infrastructure As Code (IaC)
Many organizations manage their cloud infrastructure using infrastructure as code (IaC) templates, such as AWS CloudFormation or Terraform configurations. These templates define the desired state of the infrastructure and can include sensitive information like AWS credentials.
To introduce a honeytoken into your IaC templates, you can include fabricated AWS API keys within the configuration blocks or files.
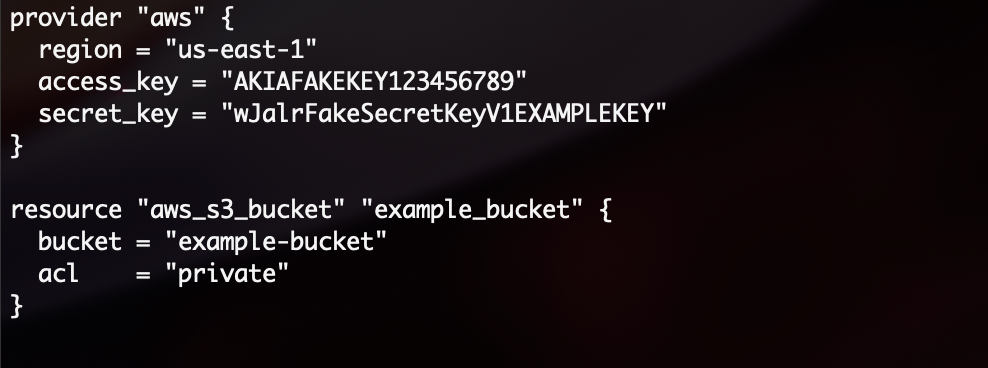
In this example, the Terraform configuration creates an S3 bucket and includes fabricated AWS access and secret keys in the provider block.
These fabricated AWS API keys act as honeytokens within your Terraform configuration. Any attempt to use or access these keys would trigger an alert, allowing you to detect and respond to potential unauthorized access to your infrastructure configuration.
Project Management Tools
Project management tools are used for coordinating development efforts. They often store sensitive information like software features, release timelines, and bug-tracking data. It’s possible to embed honeytokens within these solutions as well.
For example, you can create a ticket related to a "sensitive" upcoming feature or a task that references access to a critical system. These entries would be populated with details and documentation that contain honeytokens.
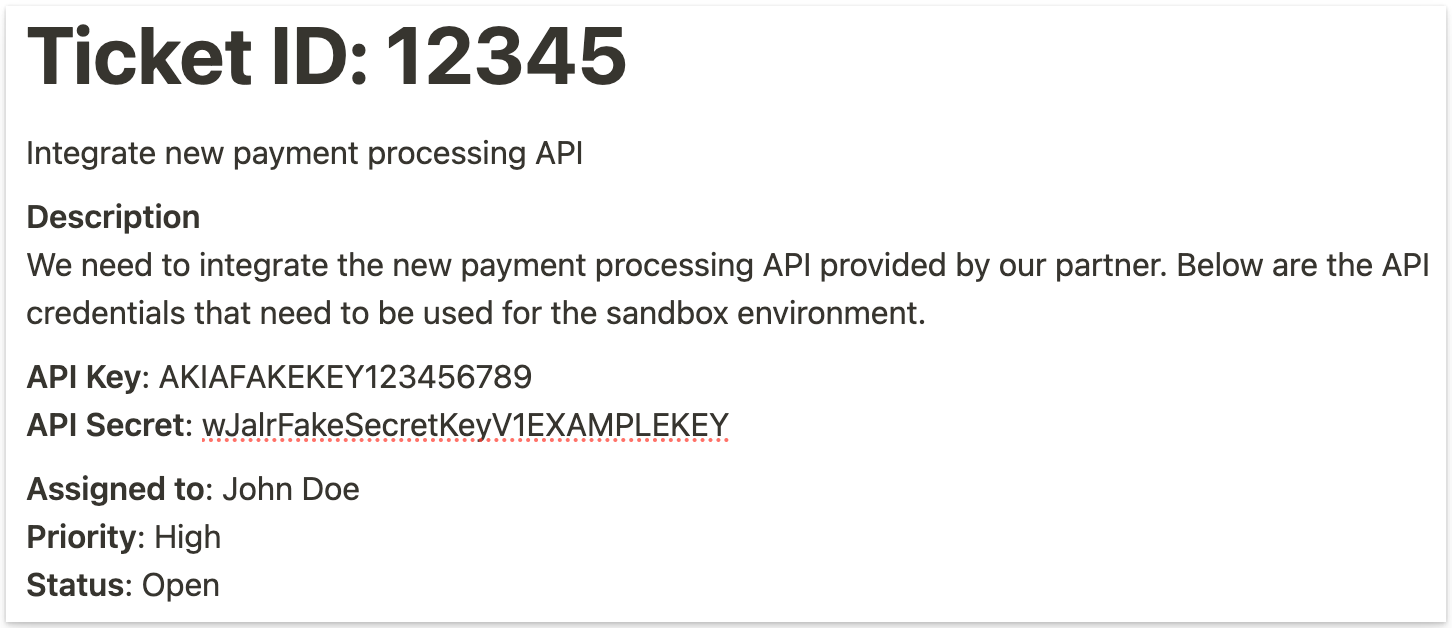
In the example provided, the fake ticket within the project management system is designed to resemble a high-priority task that would naturally draw the attention of someone with malicious intent looking for sensitive access points. The details of the ticket include AWS API credentials which are intentionally fabricated and serve as honeytokens.
You would also need to include the endpoint that the API tokens are supposed to be used on as well so that the attacker knows where to try to make the authentication attempt.
P.S - If you’re looking for a comprehensive resource on how to generate AWS API honeytokens with GitGuardian, you can check out this documentation which will help you get started.
Adopting A Zero Trust Mindset
The honeytoken techniques described above support a zero-trust security approach in the SDLC. Unauthorized users attempting to interact with honeytokens alert security teams, allowing them to deny access which aligns with zero trust.
Honeytokens also increase visibility into attacker dwell time and lateral movement across repositories, pipelines, databases, and management tools. This aligns with limiting access and permissions.
Implementing honeytokens and zero trust principles across the SDLC strengthens security through deception-based defense and identity-first access policies.
Next Steps With GitGuardian
GitGuardian is actively working on an automated honeytoken deployment system. This upcoming feature will empower organizations to integrate honeytokens into their security strategies, strengthening their defenses without added complexity or manual effort. If you’re interested in hearing more about this honeytoken technology, click here to schedule a demo.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.









