The OWASP Top 10 has always been an extremely valuable snapshot of the most pressing, real web application security risks. The 2025 updates keep that role, but shift the spotlight in a few important ways. Two new categories make the cut, one legacy bucket is expanded into a broader supply chain story, and a few things have been renamed to better reflect how people are actually attacking software today. The 2025 list sees OWASP leaning harder into root causes and the messy reality of modern software delivery.
If you work with code, CI pipelines, or cloud infrastructure, it is good to know how these shifts map to problems.
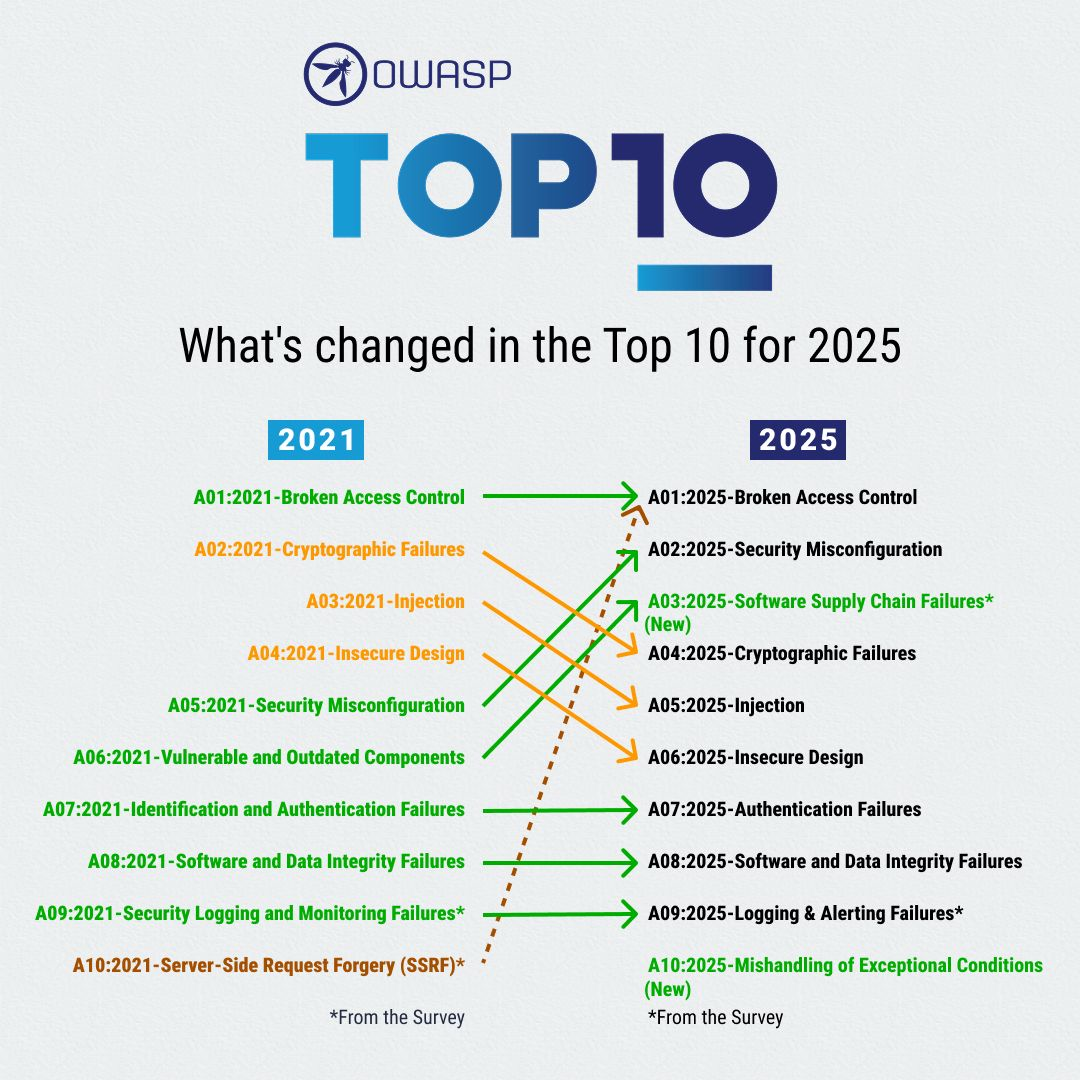
What Really Changed In The 2025 Top 10
A01:2025 - Broken Access Control Stays On Top
Start with the headlines. Broken Access Control (BAC) stays at number one, which will surprise nobody who has chased “who or what can access what” through modern systems during an incident. Also of note, Server-Side Request Forgery (SSRF) is now folded into BAC. When an attacker can convince your app to talk to things it shouldn't and access data it would not have otherwise, you have an access-control problem, not an edge case.
A02:2025 - Security Misconfiguration
Next up, Security Misconfiguration has climbed from fifth place in 2021 to second in 2025. This aligns with how we have been hastily building systems. More behavior is controlled by config files, cloud permissions, and infrastructure templates than by business logic in the code. Every mis-set flag, overly broad role, cleartext storage of secrets, or insecure default permission becomes a potential security threat. OWASP is treating those as a first-class risk rather than background noise.
A03:2025 Software Supply Chain Failures
The most visible structural change is A03:2025 Software Supply Chain Failures. In 2021, OWASP called this space “Vulnerable and Outdated Components.” In 2025, the scope is much wider as this new category covers breakdowns across the whole build and distribution ecosystem. This takes into account compromised dependencies, tampered build systems, and malicious packages. Even though this category has only five CWEs and limited coverage in testing data, it was overwhelmingly voted up in the community survey and shows some of the highest average exploit and impact scores in CVE data, meaning that it might not show up often, but when it does, it hurts, and the blast radius is huge.
A10:2025 Mishandling of Exceptional Conditions
At the bottom of the list, Mishandling of Exceptional Conditions is completely new in 2025. It pulls together twenty-four CWEs related to error handling, failing open, and other logical failures that only show up when something goes wrong at runtime. These are the “everything was fine until the network glitched” style bugs that turn boring edge cases into security incidents when error handling is either missing or misguided.
A07:2025 - Authentication Failures Decouple From Identification
Several categories have also been renamed or nudged rather than reinvented. Authentication Failures keeps its spot at number seven but drops “Identification” from the old title, so it lines up better with the thirty-six CWEs it really covers. Logging & Alerting Failures, still at number nine, now calls out alerting explicitly to underline a painful truth: logs that no one sees in time are a forensic tool, not a control. OWASP also quietly expanded the backbone of the whole project. This edition analyzes 589 CWEs across the dataset, with 248 of them mapped into the ten categories, which gives the ranking more granularity and shows up as a stronger bias toward root causes instead of symptoms.
From List To Levers: Where GitGuardian Fits
So, where does GitGuardian actually help when you look at the 2025 list through a practical lens, rather than as an abstract ranking?
GitGuardian Helps Defend Against Broken Access Control
Attackers are increasingly exploiting weak enforcement of “who can access what” through overlooked non-human identities (NHIs) like CI/CD tokens, service accounts, and embedded secrets in code. These identities often operate with broad, persistent permissions and minimal oversight, making them prime entry points for lateral movement and privilege escalation. If an adversary gets their hands on an NHI's secret, they no longer have to break in; they can simply log in.
GitGuardian addresses this risk head-on with NHI Governance, which brings visibility, control, and accountability to a traditionally opaque layer of the infrastructure:
Visibility Into Exposed And Orphaned NHIs
GitGuardian continuously scans codebases, CI pipelines, and other vital systems to discover credentials. This included tokens, API keys, cloud access keys, and more. No matter who or what they belong to, they need to be inventoried and accounted for. By building an inventory of active, stale, and orphaned NHIs, teams can begin to answer the core access control question: what entities exist, and what can they access?
Contextual Risk Prioritization
Not all secrets carry the same access scope. GitGuardian provides context on privilege level, environment exposure, and usage, enabling teams to prioritize remediation based on blast radius. The platform gives teams a direct way to reduce the potential for broken access control via misused or overprivileged identities.
Lifecycle Governance and Rotation
Persistent secrets are a common root cause behind long-lived access violations. GitGuardian supports policies for secret expiration, rotation tracking, and incident response workflows, bringing identity lifecycle hygiene to non-human actors in much the same way IAM tools do for humans.
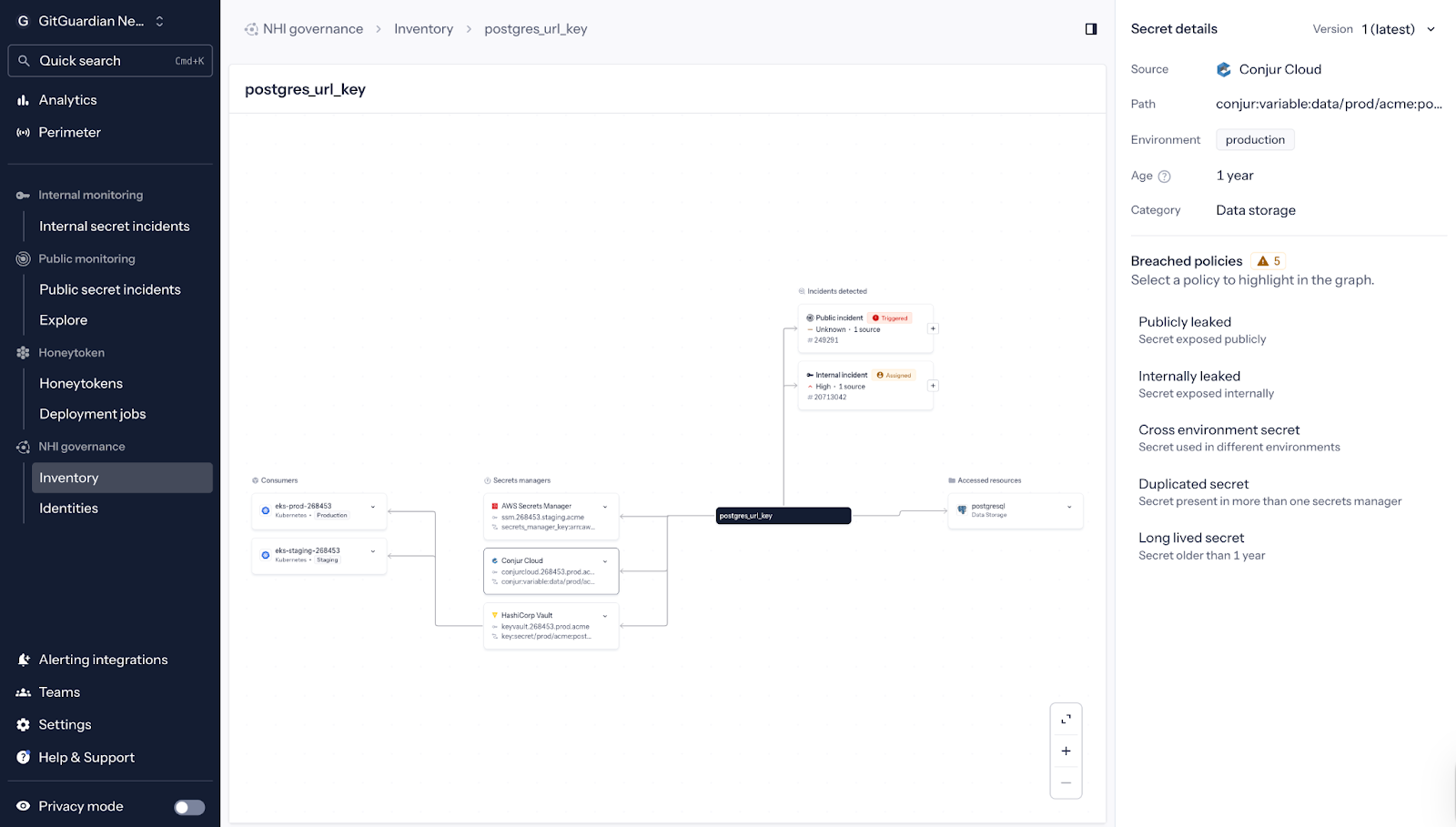
Protecting Your Supply Chain
While you might strongly associate GitGuardian with addressing broken access, as we are secrets-focused, the platform can also help teams dealing with Software Supply Chain Failures. While a big part of modern supply chain risk is vulnerable packages, part of the threat comes from credentials and non-human identities flowing through source control, CI, and deployment systems.
When OWASP talks about compromised build systems or tampered distribution channels, you can read that as “places where a leaked credential, token, or key can quietly convert a code integrity problem into full infrastructure compromise.”
By continuously scanning for hardcoded secrets, detecting leaks in source control, and prioritizing remediation at scale, GitGuardian reduces the blast radius when something in your supply chain goes wrong. You can't make the whole ecosystem safe, but you can remove the most convenient handles an attacker can grab from your link in the chain.
Adding Tripwires For Earlier Signs Of Compromise
GitGuardian’s Honeytokens push this discussion even further into the territory of Supply Chain security. Honeytokens are decoy credentials that never grant access to real resources. Instead, they act as tripwires. When someone uses them, you immediately know that a system in your supply chain has been breached or a code artifact has leaked where it should not be. Those signals are exactly the kind of “needle in a haystack” detection OWASP has in mind when it warns about subtle, high-impact supply chain compromises.
From OWASP Priorities to Practical Defenses With GitGuardian
Once again, OWASP has done the hard work of distilling a fast-moving, complex threat landscape into a practical map of where application security risk is really showing up. The 2025 Top 10 reflects technical trends and the operational realities of building and securing modern software. By focusing more on root causes, such as granting unintended permissions, supply chain complexity, and misconfigurations, OWASP gives security leaders a sharper, more actionable picture of where to invest and what to fix first.
If you’re already using GitGuardian, now is the time to align your secrets management and NHI governance efforts with the new OWASP priorities. And if you're not yet scanning for leaked credentials or signs of supply chain compromise, the 2025 list is a clear signal to start.
OWASP is showing us where the gaps are. GitGuardian gives you the tools to close them, before those gaps turn into incidents.