
OIDC for Developers: Reasons Your Auth Integration Could Be Broken
Why outsourcing auth doesn't mean outsourcing risk.

Why outsourcing auth doesn't mean outsourcing risk.

Secrets don’t belong in plaintext. GitGuardian's Push-to-Vault automates vaulting exposed secrets, helping security teams scale governance and reduce incident fatigue.

mTLS, or mutual Transport Layer Security, is a mechanism that establishes two-way authentication between two parties, ensuring they are who they claim to be.

Data security is non-negotiable. Transport Layer Security (TLS) authentication stands as the cornerstone for the protection of data in transit. When it comes to protecting enterprise APIs, systems, and identities, the importance of TLS auth cannot be overstated.
Discover what’s changed in the OWASP 2025 Top 10 and how GitGuardian helps you mitigate risks like broken access control and software supply chain failures.

Securely managing secrets within the CI/CD environment is super important. Mishandling secrets can expose sensitive information, potentially leading to unauthorized access, data breaches, and compromised systems.

Learn how to automate Helm deployments with GitOps, using Argo CD for continuous delivery. Seamlessly handle secrets, pod auto-restart, and version propagation in Kubernetes with this production-ready integration.

I'm going to show you how to build a Lambda Runtime API extension that automatically scans and redacts sensitive information from your function responses, without touching a single line of your existing function code.
Discover EKS Pod Identity Association—the modern, secure way to grant AWS permissions without the operational overhead of OIDC providers. No more duplicated IAM roles across clusters, no more trust policy updates every time you scale.
Using multiple cloud service providers isn't all benefits, it has its challenges. Today, let's have a look at multicloud: What it is, what are the challenges, especially security challenges, and what are the best practices towards a secure multicloud architecture.
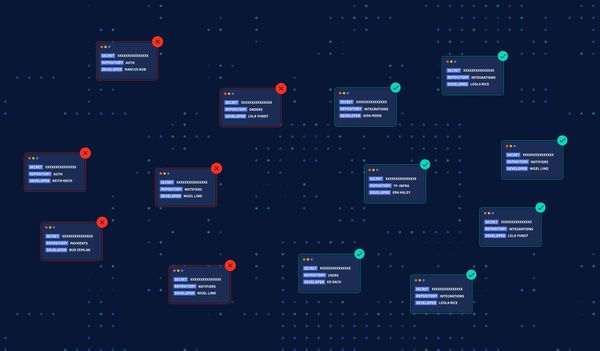
This article aims to provide application security teams with a guide to effectively prioritize, investigate and remediate hardcoded secrets incidents at scale.

Developers don’t want to become experts at security, and slowing down for anything is a tough proposition. Security isn’t a problem that will just go away, though.