For the third year running, GitGuardian is proud to announce the release of our State of Secrets Sprawl report, the most extensive analysis of secrets exposed on GitHub and beyond.
Our team of experts scanned and analyzed 1.027B new commits in 2022 (+20% compared to 2021) to uncover the latest trends and identify the most pressing challenges facing developers today.
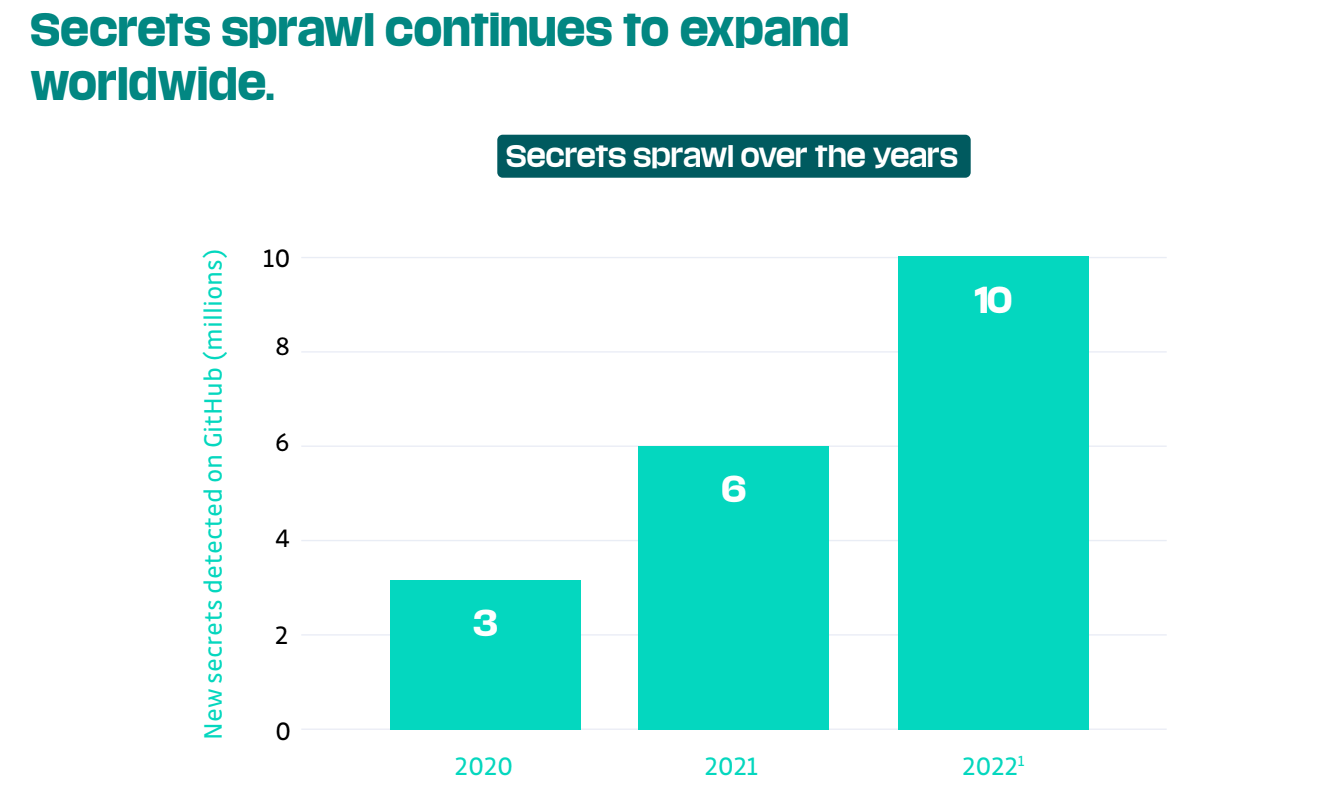
The main question we seek to answer each year is, "How many new secrets were exposed on GitHub in the preceding year?" The answer is staggering: our analysis reveals 10 million new secrets occurrences were exposed on GitHub in 2022. That's a 67% increase compared to 2021.
GitGuardian also discovered that 1 GitHub code author out of 10 exposed a secret in 2022. This number is a serious blow to the common belief that hard-coded secrets are primarily the result of inexperienced developers. The reality is that this can happen to any developer, regardless of their experience or seniority.
But the risks associated with exposed secrets go far beyond just GitHub. In fact, secrets were found in one way or another in most of the security incidents that happened in 2022.
For example, last September, an attacker pulled a full account takeover on Uber's internal tools and productivity applications by leveraging hard-coded admin credentials. Numerous breaches have resulted in the theft of source code from companies such as LastPass, Okta, Toyota, Microsoft, Samsung, and more, exposing secrets that should never have been there.
Secrets are not just any kind of credentials; they securely hold together the components of the modern software supply chain, from code to the cloud. Indeed, infrastructure as code is one of the focuses of this edition. The report details that IaC-related contributions increased by 28% in 2022, with HCL (Hashicorp Configuration Language, used in Terraform) being the fastest-growing language on GitHub.
This sudden popularity is, of course, not without its shortcomings: we found that Terraform files had an average of 5.57 occurrences of secrets (2.11 unique secrets) per 1,000 patches, which is 3x the average for all file extensions. Beyond hard-coded secrets, GitGuardian estimates that 21.52% of all Terraform repositories have one or more security policy vulnerabilities.
But far from stopping there, the report explores much more:
- Which types of credentials were most frequently found last year?
- What were the biggest trends on public GitHub?
- How secret sprawl threatens supply-chain security?
- How much time elapses between the exposure of a secret on GitHub and its compromise?
- Are there credentials for sale on the darknet?
- How to tame secrets sprawl in the SDLC?
To find out the answers,
Download the State of Secrets Sprawl 2023 report here.
"Our mission is to secure code and the SDLC. We want to do it with a transparent, simple, and pragmatic approach starting first with one of the most important issues in appsec: secrets in code." Eric Fourrier, CEO & Co-Founder
This report will serve as a valuable resource for developers, security professionals, and decision-makers committed to ensuring the security and integrity of their applications and data.
Stay tuned for more updates from GitGuardian as we continue to monitor the ever-changing threat landscape and provide the latest insights and recommendations to help you stay ahead of the curve.









