At GitGuardian, we believe that staying ahead in cybersecurity means more than introducing new features—it's about continuously refining and expanding the capabilities that organizations rely on every day. In 2024, we:
- Updated 43 times our platform;
- Released 25 new versions of our secrets detector engine;
- Integrated with 15 new sources and destinations;
- Released 12 self-hosted monthly updates of our platform;
- Delivered 13 new versions of ggshield, our open-source CLI.
We worked relentlessly to enhance our platform, making it smarter, more robust, and better equipped to tackle the evolving challenges of modern infrastructure.
From advancing secrets detection to strengthening remediation workflows, through empowering developers and securing the sprawling digital identities of NHIs, every innovation reflects our commitment to helping teams secure their systems and scale their security practices. GitGuardian's mission is not just to protect but to enable organizations to build confidently in an increasingly complex digital landscape.
Revolutionizing NHI Security
In 2024, GitGuardian reinforced its commitment to securing Non-Human Identities. NHIs are rapidly becoming more prevalent and often depend on secrets scattered across fragmented systems, lacking the stringent management customary for human credentials under traditional IAM frameworks.
GitGuardian's transformative approach to NHI Security centers on two core pillars: Secrets Security and NHI Governance. Together, they deliver scalable solutions that cater to the needs of application security and IAM teams, while effectively addressing the complexities of modern infrastructures. By centralizing secrets management and automating essential workflows, GitGuardian enables teams to respond more quickly to incidents while minimizing risk.
The Next Frontier: NHI Governance Module
The NHI Governance Module represents the next evolution in GitGuardian's approach to NHI security. Scheduled for release in early 2025, this module has been fine-tuned through beta user feedback to meet the demands of securing and managing NHI at scale.
Key benefits of the NHI Governance Module include:
- Centralized Secrets Inventory: Visibility over organizations' secrets and their context (consumers, last rotation date, associated permissions, etc.)
- Lifecycle Management: Full control over secrets, from onboarding to automated rotation and revocation.
- Advanced Analytics: Insights to optimize permissions, identify overprivileged NHIs, and refine security policies.
- Seamless Integration: Deep compatibility with existing systems, ensuring enhanced security without disrupting workflows.
This upcoming release marks a significant milestone in GitGuardian's mission to provide comprehensive NHI security solutions.
Tackling Vault Sprawl with Multi-Vault Integrations
While secrets managers like HashiCorp Vault and AWS Secrets Manager are essential for secure operations, organizations often struggle with vault sprawl—the fragmentation of secrets across multiple tools. This leads to silos, making it harder to maintain visibility, enforce policies, and remediate incidents.
Moreover, these vaults only partially solve the problem. Most lack visibility into several vital areas:
- Secrets usage: Understanding where secrets are used and their associated identities.
- Permissions: Knowing what access each secret grants across different systems.
- Secrets outside vaults: Identifying hardcoded credentials or those inadvertently pushed to public repositories.
To tackle these challenges, GitGuardian introduced integrations with the main Secrets Managers in 2024: HashiCorp Vault, CyberArk Conjur, AWS Secrets Manager, Google Cloud Secrets Manager, and Azure Key Vault. These new capabilities unify secrets management across various platforms, simplifying workflows and enhancing security.
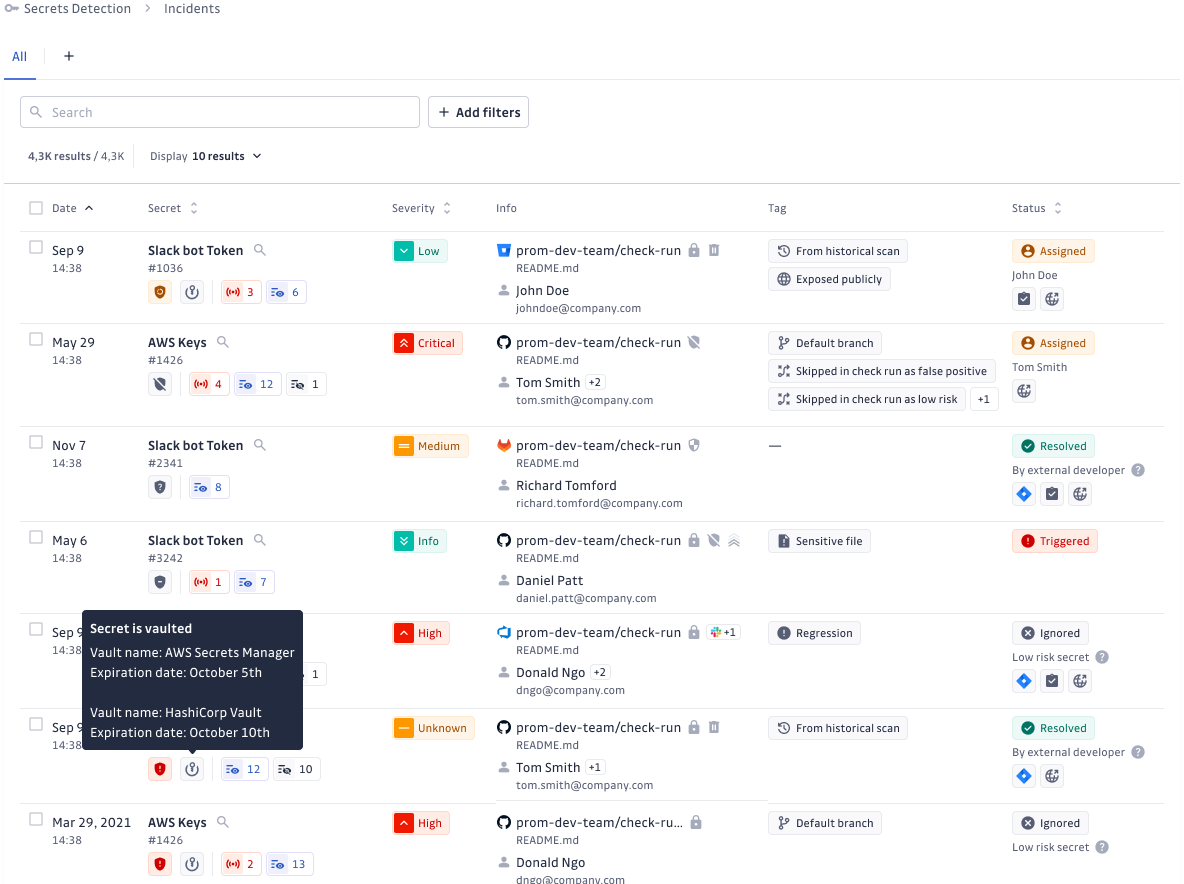
Main capabilities include:
- Unified Secrets Inventory: A centralized view of all secrets across multiple tools.
- Cross-Vault Incident Resolution: Linking incidents directly to the vault for faster remediation.
- Consistent Policy Enforcement: Uniform application of security policies across all vaults.
By addressing both NHI Governance and vault sprawl, GitGuardian empowers organizations to secure their modern infrastructures with confidence and efficiency.
Smarter Secrets Detection: Building a Stronger Security Foundation
Effective secrets detection is the foundation of any security solution focused on protecting sensitive information. A missed secret or a false positive can lead to serious consequences, ranging from wasted resources to significant breaches. In 2024, GitGuardian made it a priority to enhance its detection capabilities by ensuring accuracy, broadening coverage to new sources, and equipping developers to prevent secrets from being incorporated into codebases.
Detection That Leaves No Secret Behind
In 2024, we enhanced and expanded our library of specific and generic detectors, allowing us to identify a wider range of secrets across various platforms and services. These updates provide robust security coverage by detecting both well-known secrets and obscure credentials that could otherwise go unnoticed.
Specific Detectors
In 2024, GitGuardian introduced and upgraded its detectors for specific services and tools, such as:
- AI/ML and Data: OpenAI, Hugging Face, Mistral AI, Langchain
- Developer tools: JetBrains, Sourcegraph, Sentry, Influx DB
- Cloud and Hosting Service Keys: Azure, Cloudflare, Grafana, Kubernetes, Vercel
These additions address critical areas of exposure, ensuring that no credential tied to major services or platforms slips through the cracks.
Generic Detectors
For more flexible patterns, GitGuardian broadened its generic detection capabilities to include new detectors, such as:
- chpasswd Username Password: Detecting plaintext credential pairs.
- X-Api-Key: Identifying exposed API keys in non-standard formats.
These detectors capture secrets that might not conform to specific formats but still represent security risks.
Reducing False Positives with FP Remover
In 2024, GitGuardian tackled the ongoing issue of false positives in secrets detection by launching FP Remover, followed by its advanced version 2, a cutting-edge machine learning model. False positives—incorrectly flagged benign elements—have long caused inefficiencies, resulting in alert fatigue and wasted resources for security teams.
FP Remover utilizes an LLM-based architecture trained on extensive code datasets and fine-tuned specifically for detecting secrets. This in-house solution operates securely within GitGuardian's infrastructure, ensuring data privacy while providing exceptional accuracy.
The result is a staggering 80% reduction in false positives, allowing security and engineering teams to concentrate on actual threats without distraction. This advancement enhances operational efficiency, minimizes alert fatigue, and ensures that critical incidents are prioritized effectively.
Additionally, the GitGuardian Platform features an auto-ignore playbook that streamlines workflows by automatically dismissing incidents identified as false positives by our machine-learning model.
Custom Hosts for Validity Checks: Prioritizing Active Threats
In 2024, GitGuardian introduced Custom Host Validity Checks to tackle the challenge of verifying secrets issued by self-hosted solutions. When organizations utilize self-hosted versions of platforms like GitLab or Jira, SaaS-based validity checks often overlook the secrets generated by these systems. As a result, teams struggle to determine whether a token is still active or has been revoked.
Custom Validity Checks address this issue by allowing security teams to configure checks tailored to their self-hosted environments. This feature provides real-time insights into the status of detected secrets, ensuring active threats are prioritized while minimizing noise from inactive or revoked credentials.
By reducing false alerts and focusing on genuine risks, GitGuardian empowers organizations to maintain robust security practices across diverse environments.
Expanding Secrets Detection to the Right Sources
Improving the precision of detection is just as crucial as searching for secrets in the right sources. Secrets don't only exist in repositories or within the software development lifecycle (SDLC); they often infiltrate collaboration and workflow tools where teams communicate and share information.
To address this, GitGuardian has expanded its detection capabilities to include widely used tools such as Slack, Microsoft Teams, Jira, and Confluence, covering both SaaS and self-hosted versions. These platforms, essential to daily operations but outside the traditional SDLC, can unintentionally expose sensitive data. For instance, API keys may be shared in a Slack channel for troubleshooting purposes, or credentials might be included in Jira tickets that describe a bug.
Additionally, we're about to release support for ServiceNow, a leading IT service management platform. ServiceNow is commonly used to track incidents and manage IT workflows, where sensitive information—such as API keys or passwords—may be included in ticket descriptions or attachments.
By extending detection to these tools, GitGuardian ensures that sensitive data shared outside the SDLC is identified and protected in real time. This expansion reduces the attack surface and enhances security practices across all channels where secrets may be disclosed.
Shifting left to Prevent Secrets from Entering the Codebase
The most effective way to reduce security incidents is to prevent hardcoded secrets from being introduced into the codebase in the first place. By catching vulnerabilities before they make it into the repository, teams can avoid costly breaches and ensure their development process remains secure from the start.
To achieve this, GitGuardian has launched an extension for Visual Studio Code. This tool provides real-time secrets detection directly within the IDE, enabling developers to identify and address security issues as they write code. Secrets are flagged immediately, and actionable remediation guidance is provided, allowing developers to resolve issues before committing them to the codebase.
This proactive approach shifts security measures to the earliest stages of development, empowering developers to take the lead in preventing security risks and making every line of code safer and more resilient.
Remediation Reimagined: Moving from Detection to Resolution
Detection alone isn't enough—without effective remediation, alerts are just noise. The real value of a security solution lies in its ability to not only identify threats but also empower teams to resolve them efficiently. In 2024, GitGuardian elevated its remediation capabilities with a focus on actionable guidance, fostering collaboration between developers and security teams, and streamlining workflows to enable swift and effective incident resolution.
Better Incident Understanding: Secrets Analyzer
Effective remediation begins with clearly understanding an incident's scope and impact. To support this, GitGuardian introduced Secrets Analyzer, a feature designed to provide detailed insights into threat contexts.
Secrets Analyzer enhances secrets detection by offering contextual information for each secret, including roles, permissions, ownership, and perimeter metadata. This shifts the focus from merely identifying 'What is exposed?' to understanding 'What does this exposure mean?'—providing the depth needed to assess and mitigate risks effectively.
With these capabilities, Secrets Analyzer enables security teams to prioritize critical issues and address threats with precision and confidence.
Navigating Issues Faster: AI Filters and Saved Views
Efficient issue tracking and prioritization are essential for managing the high volume of security incidents teams encounter daily. In 2024, GitGuardian launched features aimed at helping teams focus on what truly matters.
AI Filters utilize natural language processing to make filtering incidents intuitive and precise. Instead of relying on rigid search criteria, users can simply describe what they're looking for in natural language. For example, they may request "Show all secrets exposed in public repositories" or "Incidents linked to AWS keys." The AI interprets the query and dynamically applies the relevant filters, saving time and ensuring teams can quickly surface the incidents that matter most.
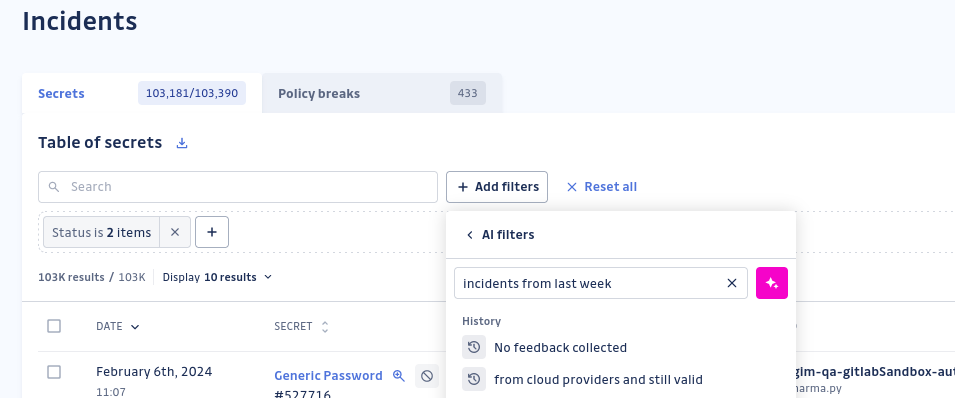
Saved Views complement this functionality by allowing users to store their most frequently used filters for quick access. Whether monitoring a specific perimeter or focusing on unresolved incidents, Saved Views eliminate repetitive filtering steps and improve navigation efficiency.
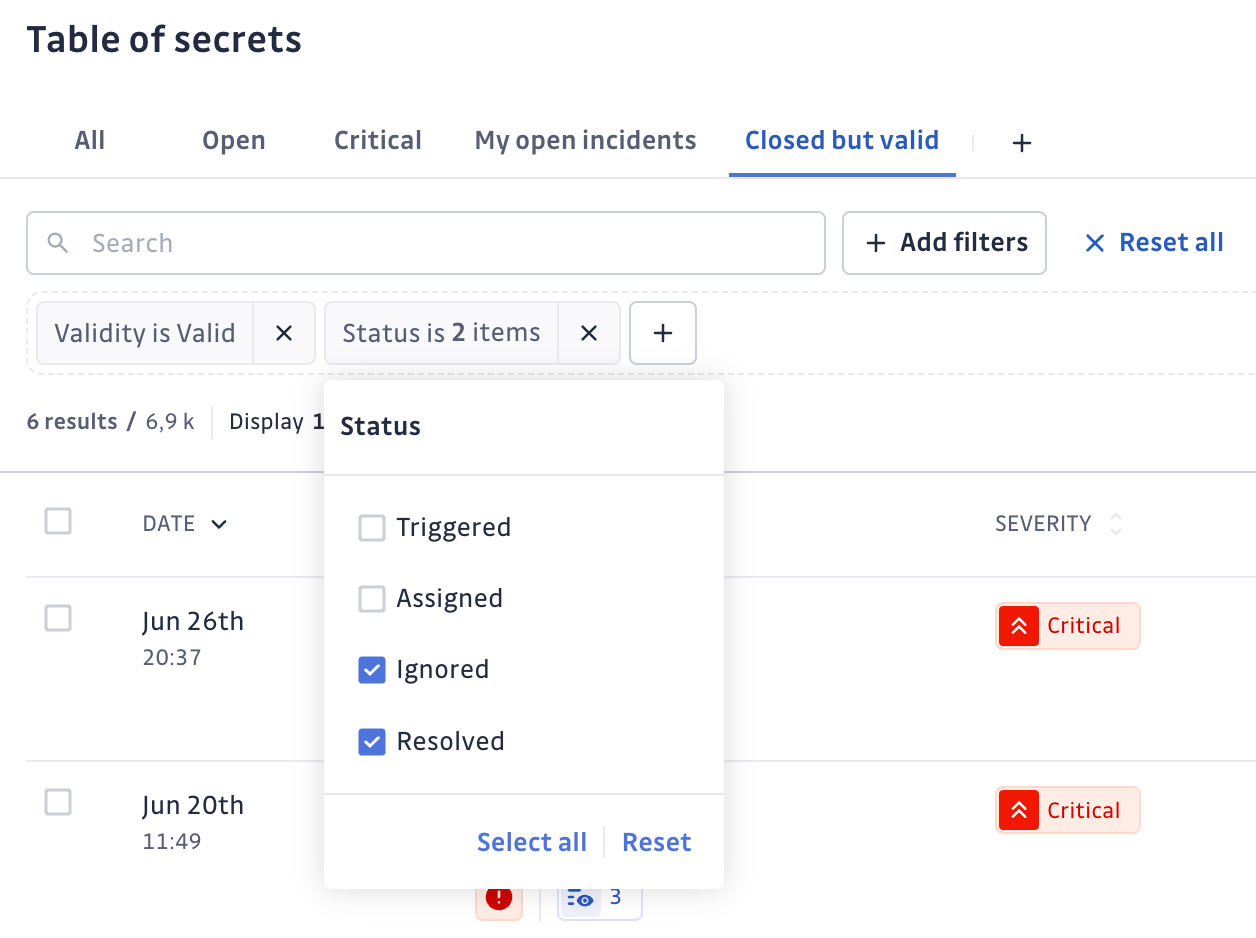
Together, AI Filters and Saved Views simplify the management of large volumes of incidents.
Streamlined Remediation Workflow: Pinpointing Issues and Guiding Fixes
Effective remediation requires precision and collaboration. Throughout our journey, we've recognized that simply listing all occurrences of a secret often leaves AppSec teams and developers overwhelmed, especially in large enterprises. Without clear direction, sifting through extensive codebases can delay fixes and heighten risks. That's why we focused on streamlining the remediation process.
Pinpointing Files Needing Code Fixes and Tracking Progress
Identifying where secrets are exposed is the first step to effective remediation. GitGuardian highlights the specific files and lines of code where secrets are hardcoded. This ensures developers can focus their efforts on the areas of concern.
Tracking the progress of remediation is just as critical. GitGuardian's remediation tracking capabilities monitor pull requests associated with incidents, providing real-time visibility into the status of fixes. Security teams can:
- Monitor Progress: Track the remediation status across affected repositories.
- Verify Remediation: Confirm whether a pull request effectively removes a secret from the codebase.
- Access Pull Request Details: Link directly to relevant pull requests to review progress and ensure resolution.
These capabilities enhance transparency and accountability, streamlining the process from detection to resolution.
Custom Remediation Messages
To further support developers, GitGuardian enables security teams to provide Custom Remediation Messages. These messages offer tailored guidance, including clear instructions, internal resources, or links to best practices. Delivered at critical moments throughout different stages of the SDLC, these messages foster collaboration between developers and security teams, ensuring that remediation aligns with organizational standards.
GitGuardian's relentless investment in remediation features reflects a deep commitment to empowering teams with the precision, context, and tools they need to not only resolve incidents but also build a stronger, more proactive security culture.
Redefining Honeytoken Deployment for Better Breach Detection
In 2024, GitGuardian elevated its Honeytoken capabilities with more flexible and context-aware deployment options, empowering organizations to detect and respond to threats with greater precision.
Deployment Jobs: Automating Honeytoken Deployment
Deploying honeytokens at scale can be challenging, especially in environments with multiple repositories. GitGuardian's Deployment Jobs simplify this process by automating the creation, insertion, and integration of honeytokens. Users can easily select the target repositories, and the system handles the generation of honeytokens, their placement, and the creation of pull requests.
This streamlined approach allows organizations to strategically deploy decoy credentials throughout their infrastructure. This enhances early detection of unauthorized access attempts and ensures swift, effective responses.
Flexible Context Creation: Customizing Honeytoken Configurations
Recognizing the need for tailored security measures, GitGuardian introduced the ability to customize honeytoken attributes. These flexible configurations enable organizations to deploy decoys that closely mimic real credentials, aligning with specific threat detection scenarios.
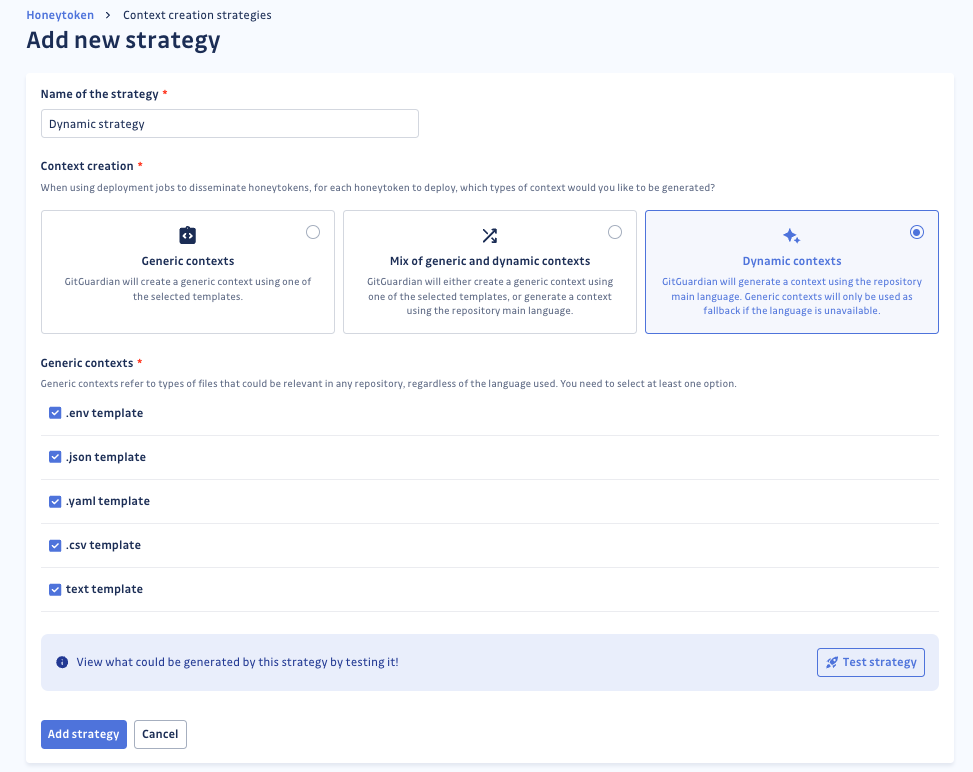
With these enhancements, GitGuardian empowers organizations to strategically plant honeytokens, improving early breach detection and response capabilities across diverse environments.
Public Monitoring: Safeguarding Against Public Secrets Leaks
GitGuardian remains at the forefront of monitoring public repositories for exposed secrets. As the Secrets Sprawl continues to grow, with more than 12M secrets publicly exposed on GitHub, we had to enhance our public monitoring capabilities to help teams identify and address critical exposures more efficiently.
AI-Driven Incident Prioritization: Focus on What Matters Most
Managing a large volume of alerts can be overwhelming for security teams. To tackle this challenge, GitGuardian introduced AI-driven prioritization, automatically identifying high-severity incidents. By analyzing factors such as the type of secret, its validity, and potential impact, our in-house machine learning model assigns priority levels to incidents with high precision and recall. This allows teams to focus on addressing the most critical vulnerabilities first.
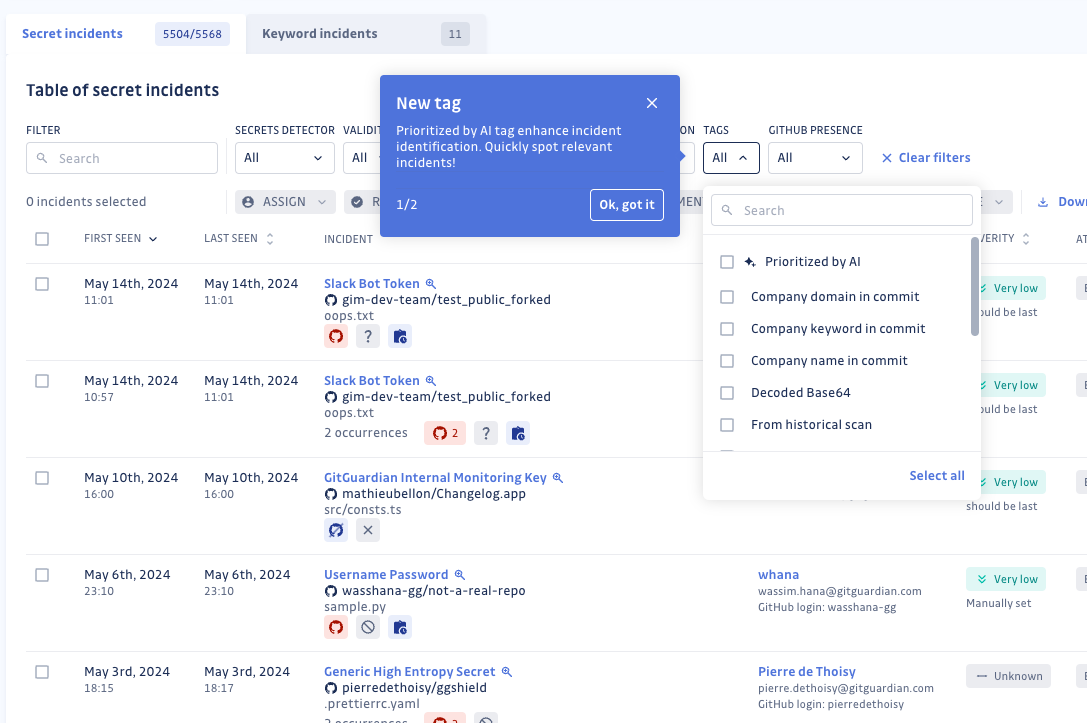
Enhanced Incident Triage: Greater Clarity for Better Decisions
Effective incident management necessitates clear visibility into the severity and context of each alert. We enhanced our incident triage process by providing improved visibility regarding severity rules. Security teams can comprehend the criteria that establish an incident's severity, leading to better decision-making and prioritization.
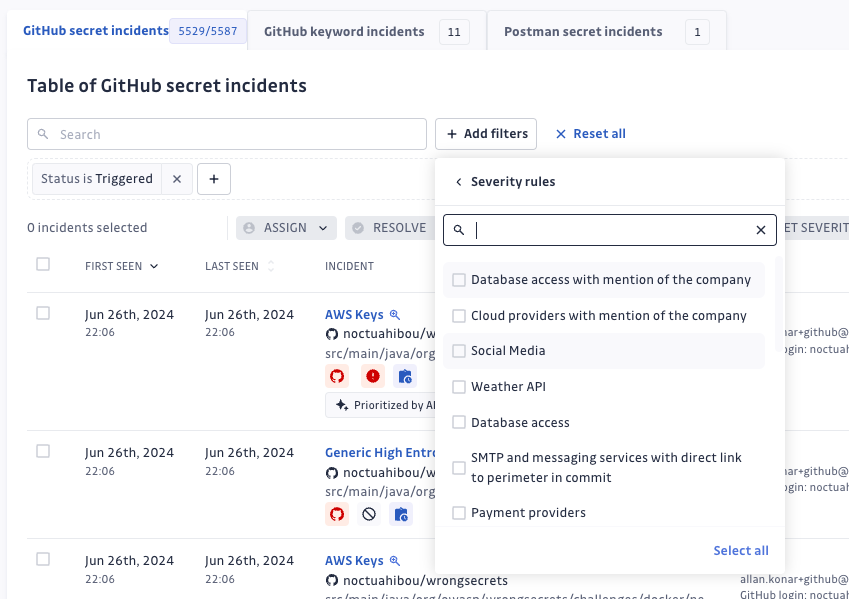
These updates ensure faster identification and resolution of critical public exposure incidents.
Enterprise-Grade Security and Compliance
In 2024, GitGuardian introduced several enhancements to support enterprise scalability and compliance, matching clients' needs.
European Data Hosting
To address GDPR compliance and data sovereignty concerns, GitGuardian now offers data hosting within the EU, specifically in AWS Frankfurt, Germany. This ensures that sensitive data remains within EU borders, helping enterprises meet regulatory requirements and protect user privacy.
Self-Hosted Feature Parity
GitGuardian has achieved full feature parity between its SaaS and self-hosted solutions, ensuring that organizations opting for self-hosted deployments can access the same capabilities as those using the SaaS platform.
Moreover, Guardian now supports Common Access Card (CAC) and Personal Identity Verification (PIV), meeting stringent security requirements for government agencies and contractors.
AWS Marketplace Availability
GitGuardian's platform is available on AWS Marketplace, simplifying procurement and deployment for enterprises.
These updates reflect GitGuardian's dedication to delivering scalable, compliant, and accessible security solutions for enterprises navigating complex regulatory environments.
Conclusion
As we approach 2025, GitGuardian remains committed to empowering organizations with the tools to address evolving security challenges. Our focus on continuous improvement and innovation ensures that our solutions not only provide protection but also adapt to the changing landscape of cybersecurity.
This year, we are doubling down on our NHI Security Strategy, particularly emphasizing the pillars of Secrets Security and the upcoming NHI Governance Module. These initiatives go beyond mere features; they represent a transformative approach to securing modern infrastructures and digital identities at scale.
We are not just creating a product; we are shaping a future where organizations can innovate with confidence, knowing that GitGuardian's continually advancing platform protects their systems and secrets. Here's to a safer, brighter 2025!








