
Your Secrets Need a VDP, Not Just a Bug Bounty
Bug bounty programs are valuable—until they replace disclosure policies. Learn how unreasonable PoC demands or scope exclusions create security blind spots when it comes to leaked secrets.

Bug bounty programs are valuable—until they replace disclosure policies. Learn how unreasonable PoC demands or scope exclusions create security blind spots when it comes to leaked secrets.
![Shai-Hulud 2.0 Exposes Over 33,000 Unique Secrets [Updated Nov, 27]](/content/images/size/w600/2025/11/shai-hulud--2--1.png)
On November 24, a new wave of the Shai-Hulud supply chain attack emerged. The threat actors exfiltrate stolen credentials directly to GitHub repositories created with compromised tokens.

We found a path traversal vulnerability in Smithery.ai that compromised over 3,000 MCP servers and exposed thousands of API keys. Here's how a single Docker build bug nearly triggered one of the largest AI supply chain attacks to date.

The threat GitGuardian has long-anticipated is now a reality: criminal groups are executing systematic attacks targeting hardcoded credentials and over-permissive IAM configurations. The situation escalated when Shiny Hunters and Crimson Collective formed an alliance to coordinate efforts.

On September 15, a new supply chain attack was identified that targeted the @ctrl/tinycolor and 150 other NPM packages. The attack scenario was similar to the one used in the s1ngularity and GhostActions campaigns. The threat actors combined a local environment secrets extraction

On September 5, 2025, GitGuardian discovered GhostAction, a massive supply chain attack affecting 327 GitHub users across 817 repositories. Attackers injected malicious workflows that exfiltrated 3,325 secrets, including PyPI, npm, and DockerHub tokens via HTTP POST requests to a remote endpoint.

Symmetric cryptography powers everything from HTTPS to JWT tokens, but key management remains a significant challenge. This developer guide covers three critical use cases—session keys, self-use keys, and pre-shared keys—with practical strategies for secure generation, rotation, and storage.

AI adoption accelerates secret sprawl as organizations connect to multiple providers. Our investigation of a leaked xAI API key, which granted access to unreleased Grok models, reveals critical flaws in their disclosure process, highlighting necessary improvements in this domain.
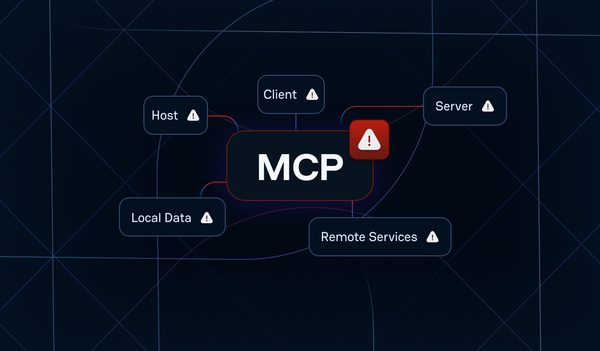
MCP rapidly enhances AI capabilities but introduces security challenges through its distributed architecture. Especially, the distributed nature of MCP requires a lot of NHIs and their secrets. Our research shows that MCP is a new source of leaks that already discloses real-world secrets.

Responsible disclosure is an often overlooked but critical component of cybersecurity alerting processes. Explore key best practices that can enhance communication and collaboration with researchers, turning potential security threats into opportunities for stronger defense.

At JSSI 2025, French IT security experts discussed the cloud's impact on security. Presentations covered strategy and technical analysis. GitGuardian’s researchers shared insights on detecting secrets in the cloud and responsibly disclosing them to companies.

On March 14, 2025, the popular GitHub action tj-actions/changed-files was compromised, exposing secrets in CI logs. GitGuardian's analysis identified leaked secrets like GitHub tokens, AWS keys, and more.