As a company with a large number of developers, it's highly likely that some of your company secrets (API keys, tokens, etc.) are publicly exposed on GitHub without your knowledge.
Here are 5 reasons why you should request your complimentary audit of secrets leaks on GitHub.com from GitGuardian.

1. Many developers = many leaked secrets
If your company has a significant number of developers, chances are high that some of your confidential information, such as API keys and tokens, may be publicly available on GitHub. This implies that anyone on the Internet can access them, posing a significant security threat.
Our annual report, the State of Secrets Sprawl, aims to increase awareness about the extent of the threat posed by secrets sprawl. In 2022, we detected 10 million instances of leaked secrets, which represents a 67% increase from the previous year. Shockingly, one in ten code authors exposed a secret, resulting in an average of 5.5 commits out of every 1000 that revealed at least one secret.
It’s important to acknowledge that even if your company doesn't do open source, chances are your developers do. And a corporate secrets or source code leak on a personal GitHub repo probably has happened in the past – multiple times! None is immune to mistakes, and even experienced developers are often leaking without realizing it. Our audit can help you identify any potential vulnerabilities.
2. Put a number on the problem
Obtaining a complimentary audit can help you evaluate with your company's own data the size of the problem and decide on its priority.
To drive decisions, data is primordial. Cybersecurity is a busy domain, and we know that choices have to be made.
Having visibility is essential for prioritizing, gaining peer approval, and effectively addressing a particular issue. This is precisely why we offer a free audit - to provide you with quick insights that will give you a comprehensive understanding of the problem's actual scope. Your report will resemble the following:
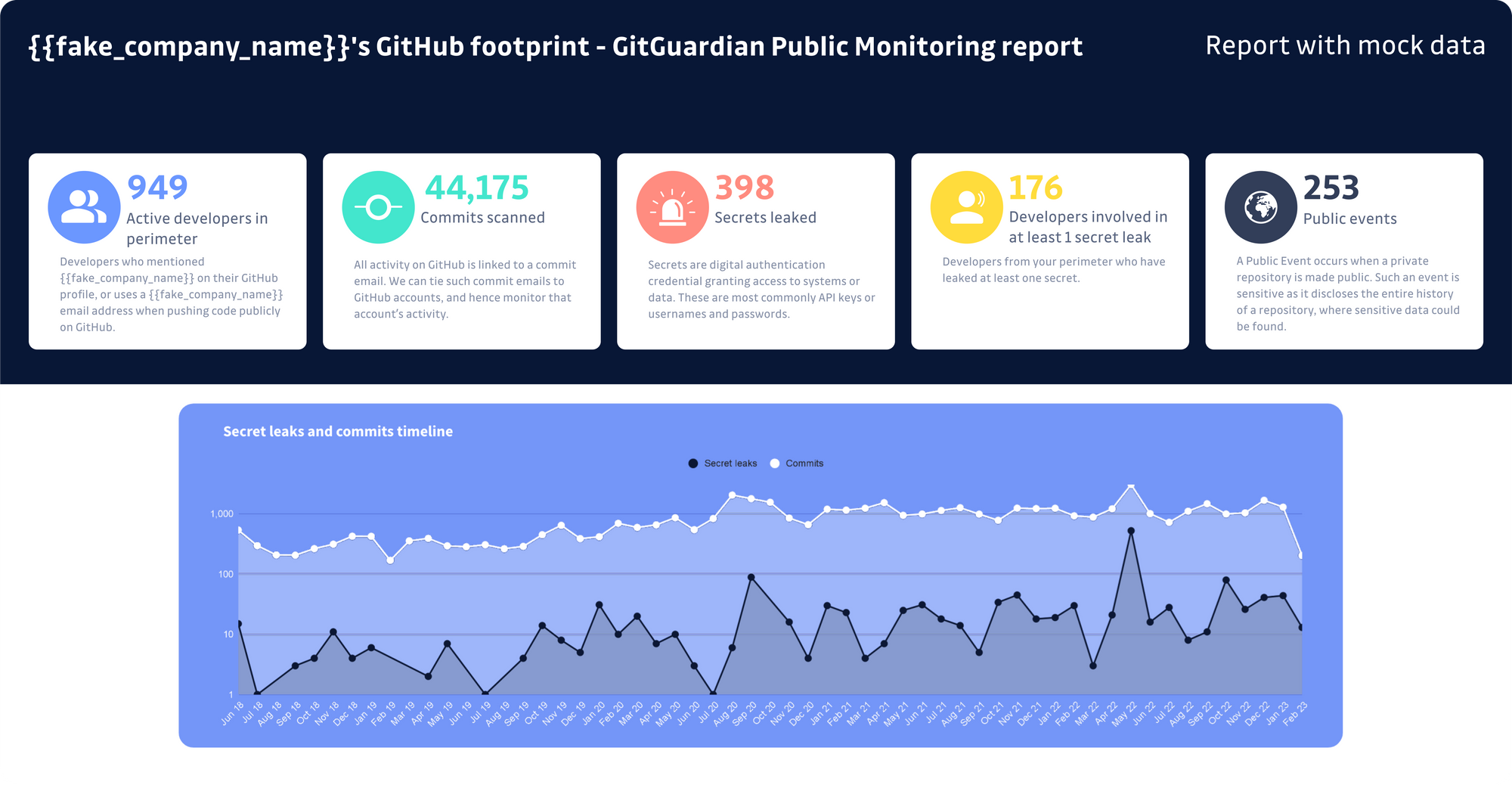
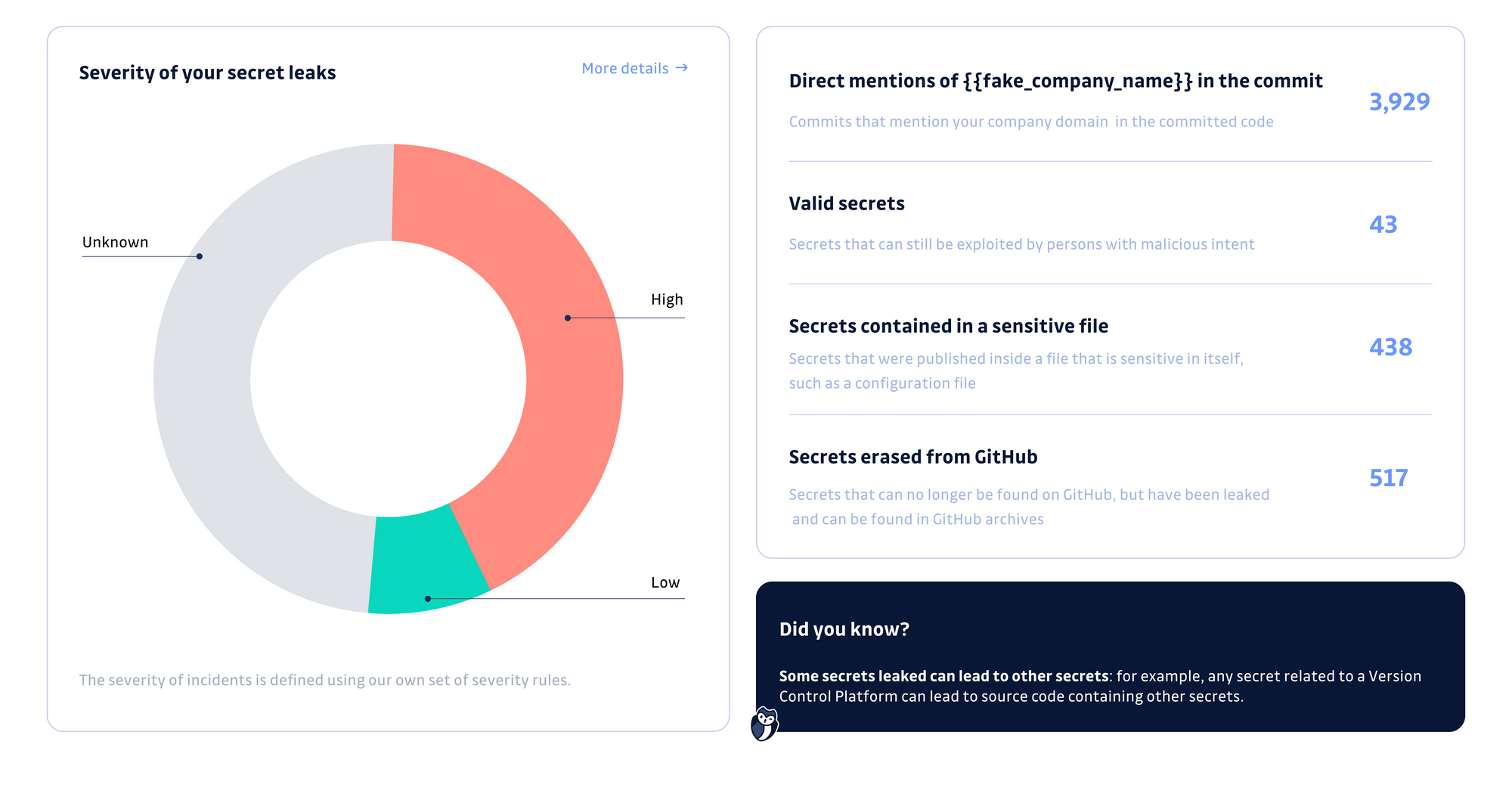
Key metrics are highlighted, such as:
- Active developers in your perimeter: Developers who mentioned your company name on their GitHub profile or use their company email address when pushing code publicly on GitHub.
- Secrets leaked publicly on GitHub: Secrets are digital authentication credentials granting access to systems or data. These are most commonly API keys or usernames and passwords.
- Valid secrets present on GitHub: Secrets that can be exploited by persons with malicious intent.
- Commits scanned: All activity on GitHub is linked to a commit email. We can tie such commit emails to GitHub accounts and hence monitor that account activity.
- Secrets breakdown by category: Percentage of secrets leaks per category: Private key, Version control platform, Cloud provider, Messaging system, Data storage, etc.
- Public events: A public event occurs when a private repository is made public. Such an event is sensitive as it discloses the entire history of a repository where sensitive data could be found.
We are confident that security teams are increasingly aware of the severity of sprawled and exposed credentials, but to back up claims, nothing beats data.
Remember that, unlike other application security vulnerabilities, hardcoded credentials accumulate in time. The faster you can take action and stop the bleeding, the less costly for the organization (you can also try our simulator to estimate the cost of doing nothing over time).
Requesting a complimentary audit allows you to evaluate if this is a real priority for your company with your company's data.
3. Benefit from the detection capability of the #1 security app on the GitHub marketplace
Our solution goes beyond just detecting incidents; it is a comprehensive platform for monitoring and resolving incidents.
Based on our experience, most AppSec and Threat intel teams prefer to start tackling secrets sprawl by using their own detection tool, often built on open-source technology. While these DIY solutions can be helpful at first, they often become difficult to maintain at scale, rely on a specific SCM provider, are hard for developers to use, and have siloed remediation processes.
By requesting a complimentary report, you can quickly compare your previous findings with GitGuardian's and make an informed decision. This service is completely free and non-committal, allowing you to compare our solution to any open-source alternatives you may have implemented.
4. Revamp your Vulnerability Disclosure Program with a leaked secrets report that can supercharge your efforts
While scanning repositories for vulnerabilities, you may come across numerous hard-coded secrets that require efficient triaging. However, a vulnerability disclosure program (VDP) may not be the most effective tool in this scenario.
VDPs can only recover a few leaks of secrets at a time and at a high cost. To remediate hard-coded secrets, you need a single platform that can quickly identify the issues and resolve them.
Our audit can save you valuable time and money by providing you with a comprehensive report in just a few hours.
We can automatically identify valid secrets and triage them accordingly, giving you the full picture in one go.
5. The best way to establish your GitHub security perimeter
To begin securing your GitHub attack surface, the first step is to get an audit. This report will give you a quick overview of your current security status on GitHub.com. Once you receive the report, which typically takes 1-2 business days, the next step is to set up your customized GitGuardian Public Monitoring Dashboard. Check out our demo video for more information:
Our team of code security experts can guide you through this process and provide a tailored analysis to help you focus on the most relevant security incidents affecting your company.
With the GitGuardian platform, you can prioritize and remediate incidents at your own pace. To get started, sign up for a complimentary audit and start securing your most critical secrets or managing those not reported by your existing solutions.
Understanding GitHub's Secret Security Architecture
GitHub secrets are designed with multiple layers of protection, but their safety depends heavily on proper implementation and understanding of the platform's security model. GitHub's secret management system encrypts secrets at rest using AES-256 encryption and restricts access through role-based permissions. However, the security effectiveness varies significantly between public and private repositories.
In public repositories, secrets are never exposed directly to external contributors or visible in workflow logs when properly configured. GitHub automatically redacts secret values from logs and prevents them from being accidentally printed. However, the real vulnerability lies in workflow configuration errors, particularly when using pull_request_target triggers that can expose secrets to malicious pull requests from forks.
Private repositories offer additional security layers, including restricted access controls and enhanced audit logging. The key distinction is that secrets in private repos are only accessible to authorized team members, while public repository secrets require more careful workflow design to prevent exposure through malicious contributions or compromised third-party actions.
The Hidden Risks of Git History and Repository Transitions
One critical aspect often overlooked when evaluating GitHub secrets safety is the permanent nature of Git history and the risks associated with repository visibility changes. Even when secrets are properly managed in the current codebase, historical commits can contain exposed credentials that remain accessible indefinitely.
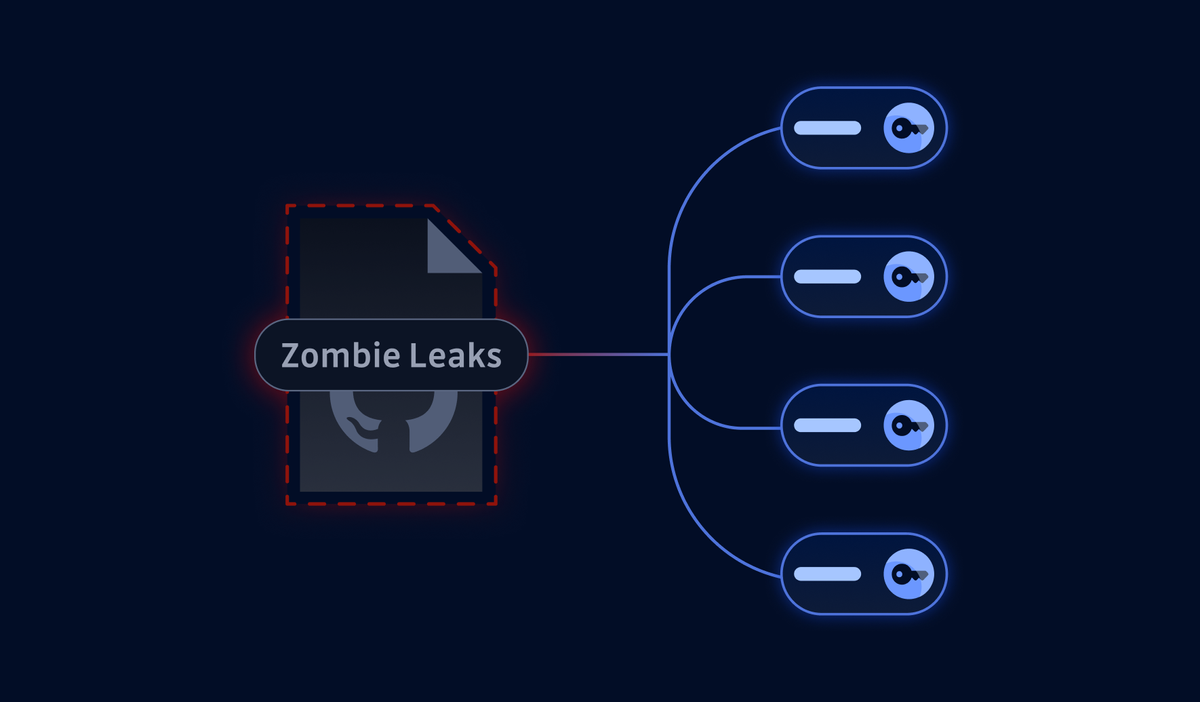
When private repositories are made public—what GitGuardian terms "public events"—the entire commit history becomes visible, potentially exposing secrets that were committed months or years earlier. This creates a significant attack surface that traditional security reviews miss, as they typically focus on current code rather than historical data.
The challenge intensifies when developers use personal GitHub accounts for both professional and personal projects. Corporate secrets can inadvertently leak into personal repositories through copy-paste errors or shared development environments. Unlike application security vulnerabilities that can be patched, hardcoded credentials accumulate over time in Git history, making early detection and remediation crucial for minimizing organizational risk.
Implementing Comprehensive Secrets Detection Beyond Basic GitHub Features
While GitHub provides native secret scanning capabilities, comprehensive protection requires understanding the limitations of built-in tools and implementing additional detection layers. GitHub's default secret scanning covers common patterns like API keys and tokens, but it cannot detect organization-specific secrets, custom authentication schemes, or generic credentials that don't match predefined patterns.
Advanced secrets detection involves monitoring not just repository commits, but also pull request discussions, issue comments, and workflow artifacts where sensitive information might be inadvertently shared. The detection capability must extend beyond pattern matching to include contextual analysis and validation of discovered secrets to determine if they're still active and exploitable.
Organizations need automated systems that can scan their entire GitHub perimeter—including all repositories associated with company email domains or organizational mentions. This comprehensive approach helps identify the true scope of secrets exposure across an organization's entire development ecosystem, providing the data necessary to prioritize remediation efforts and prevent future incidents through developer education and improved security practices.
Conclusion
Requesting a complimentary audit of your secrets leaks on GitHub from GitGuardian is a smart decision for any company with a large number of developers.
The audit can help you accurately determine your developer perimeter on GitHub, evaluate the extent of the secrets sprawl problem, and prioritize accordingly.
GitGuardian's solution goes beyond just detection and can save time and money by providing a comprehensive overview in a matter of hours.
It is the ideal way to begin the journey towards secrets-free code and take control of the detection, remediation, and prevention cycle at your own pace. To take the first step towards a more secure GitHub environment, request your audit today without delay!
FAQ
Are GitHub secrets safe by default, or do organizations need additional controls?
While GitHub secrets benefit from encryption and access controls, their safety is not guaranteed by default. Security depends on correct workflow configuration, repository visibility, and disciplined developer practices. Organizations should implement additional detection and monitoring solutions to address risks like historical leaks, misconfigurations, and exposure during repository transitions.
What are the main risks associated with secrets exposure on GitHub?
The primary risks include accidental commits of credentials, exposure through public events (such as making a private repo public), and leaks via personal developer accounts. Historical Git history can retain secrets indefinitely, and workflow misconfigurations may inadvertently expose secrets to external contributors or malicious actors.
How does a complimentary GitGuardian audit help organizations assess their GitHub secrets exposure?
A complimentary GitGuardian audit scans public GitHub for leaked secrets tied to your organization, providing actionable metrics such as the number of active developers, leaked and valid secrets, and exposure breakdowns. This data-driven approach enables security teams to quantify risk, prioritize remediation, and benchmark existing controls against industry best practices.
Why is it important to monitor both current and historical GitHub data for secrets leaks?
Secrets can persist in Git history even after removal from the current codebase. When repository visibility changes or forks occur, previously hidden secrets may become accessible. Continuous monitoring of both current and historical data is essential to identify and remediate all potential exposures, not just those in active code.
How do GitHub’s built-in secret scanning features compare to specialized solutions like GitGuardian?
GitHub’s native secret scanning detects common credential patterns but often misses organization-specific secrets, generic credentials, and exposures outside code (e.g., in comments or workflow artifacts). Specialized solutions like GitGuardian provide broader coverage, contextual analysis, and validation to ensure comprehensive detection and prioritization of real risks.
What steps should organizations take after discovering leaked secrets on GitHub?
Upon discovery, organizations should immediately revoke and rotate affected secrets, investigate the scope of exposure, and update security policies to prevent recurrence. Implementing automated detection, developer education, and robust incident response processes are critical for minimizing risk and maintaining compliance.
How does organizational growth or M&A activity impact the safety of GitHub secrets?
Growth and M&A increase the complexity of developer perimeters and secret management, often leading to vault fragmentation and inconsistent controls. This amplifies the risk of secrets sprawl across public and private repositories. Regular audits and unified monitoring are essential to maintain visibility and control as the organization evolves.










