In the realm of software development, Continuous Integration and Continuous Deployment (CI/CD) pipelines have become integral. They streamline the development process, automate repetitive tasks, and enable teams to release software quickly and reliably. But while CI/CD pipelines are a marvel of modern development practices, they also present potential security vulnerabilities.
With the integration of various tools, systems, and environments, CI/CD pipelines often deal with sensitive information, making them a potential target for cyber attacks. Consequently, it's crucial to weave in robust security measures to protect these pipelines and maintain the integrity of your development process.
One such proactive measure is the deployment of honeytokens. Created within GitGuardian's Honeytoken module, honeytokens are essentially digital baits designed to attract and detect unauthorized access or activity within your systems. By adding honeytokens to your pipelines, you can add an extra layer of defense against potential intruders.
In the following sections, we will delve into what honeytokens are, how they work to detect intrusions, and how you can effectively implement them in your CI/CD pipelines to enhance security. Stay tuned to uncover how you can leverage the power of Honeytokens to protect your digital assets better.
Decoding Honeytokens: An Extra Layer of Defense
A honeytoken is a deceptive instrument, a digital decoy strategically positioned to attract potential intruders.
These tokens have no legitimate operational value. Their sole purpose is to serve as bait and alert you if someone tries to use them. When an unauthorized user attempts to use a honeytoken, it triggers an alert, letting you know of the intrusion. It's like having a silent alarm in your house that triggers when a burglar tries to unlock the safe.
Not only does a honeytoken alert you of the intrusion, but it also provides crucial information about the attacker. You get details like the IP address and the user agent of the intruder, helping you in further securing your system and even tracking down the threat.
Introducing honeytokens to your CI/CD pipelines, especially within your platform's environment variables, echoes the essence of a diligent watchman, standing guard around the clock. This ever-alert sentinel stands its ground, much like during the infamous CircleCI security incident in early 2023 (the detailed account can be read here).
Imagine if an intruder had an audacious scheme to exploit these 'secret' variables, say your AWS Keys. The very moment they attempted, your trusty honeytoken watchman would sound the alarm. The alert would reach you in a flash, giving you ample opportunity to intervene, halt the dubious activity, and glean crucial lessons to fortify your digital infrastructure.
In the upcoming sections, we will guide you on how to implement honeytokens in various CI/CD pipelines, including Jenkins, CircleCI, Travis CI, GitLab CI/CD, Azure DevOps Pipelines, and AWS CodePipeline.
Boosting Travis CI Security using Honeytokens
If you're involved in software development, you're likely familiar with Travis CI. As a popular Continuous Integration (CI) service, Travis CI is used to build and test software projects hosted on GitHub and Bitbucket. While Travis CI already has its own measures to ensure the security of your software projects, honeytokens can provide an extra layer of defense to help identify and respond to potential threats.
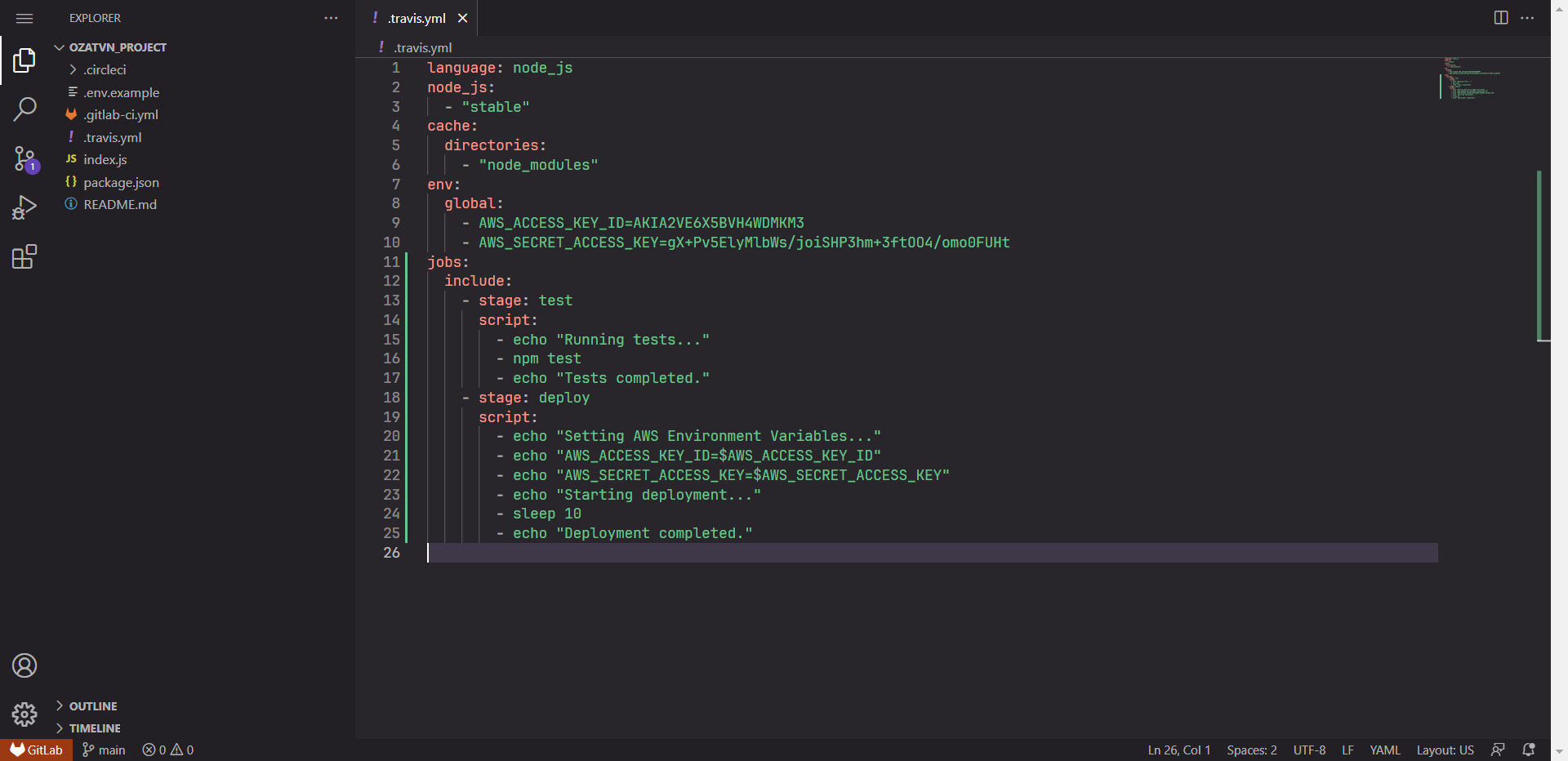
To enhance your Travis CI security, you can strategically place different honeytokens in your build scripts or configuration files. Files like .travis.yml, environment variables, or even in your test scripts are some of the places you can consider. Remember, a honeytoken's value lies in its ability to track down the resource that has been compromised, so using a different honeytoken for each place is important.
Here's how you can start boosting your Travis CI security with honeytokens:
- Begin by creating a honeytoken using GitGuardian's Honeytoken module. Keep it handy for the upcoming steps.
- Navigate to your Travis CI configuration file (.travis.yml or similar) or any script files where you wish to place your honeytoken.
- Place the honeytoken in the selected location, treating it as you would any sensitive data.
- Save the changes and ensure the updated files are pushed to your SCM repository.
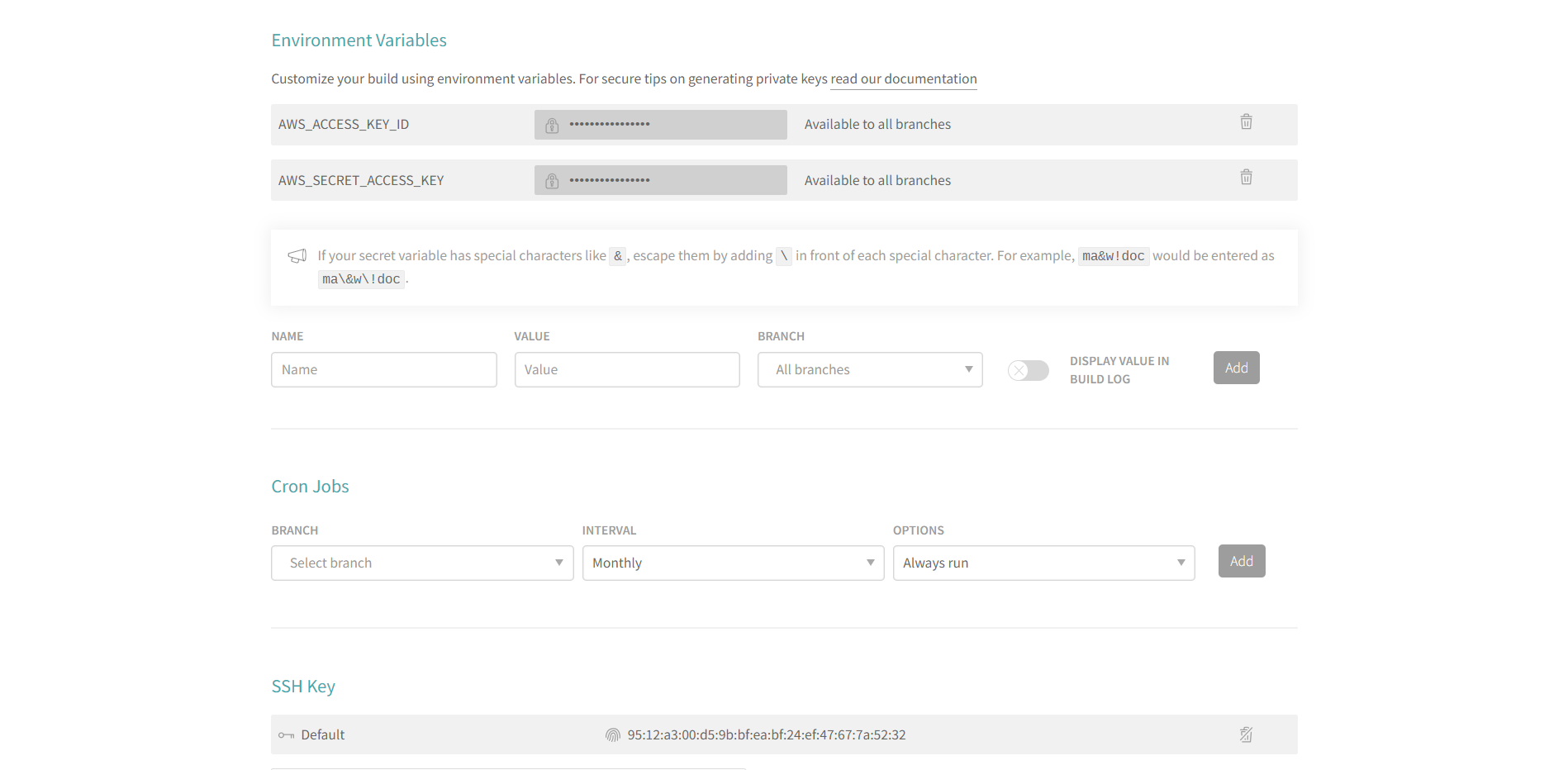
Travis CI also uses environment variables to store secrets. You can repeat the process and add a new honeytoken to your repository settings under the "Environment Variables" section. If someone tries to misuse these variables, the honeytoken will serve as an alarm bell.
Securing CircleCI Pipelines with Honeytokens
CircleCI is a widely adopted Continuous Integration and Delivery (CI/CD) platform. It simplifies the automation of your software development process, from building and testing to deploying your applications. Despite CircleCI's built-in security measures, enhancing it with honeytokens can further protect your CI/CD pipeline from malicious intrusions.
Honeytokens can be strategically added to several parts of your CircleCI pipeline. Some common locations include configuration files like config.yml, shell scripts, or even within environment variables. Similar to a secret key, an attacker accessing and using a honeytoken will trigger an alert, providing you with an early warning of a potential security breach.
Here's how you can integrate honeytokens into your CircleCI pipeline:
- First, create a honeytoken in the GitGuardian Honeytoken module. Remember to note down the generated token for later use.
- Go to your project repository and find the CircleCI configuration file, typically named config.yml and located in the .circleci directory.
- Embed the honeytoken in this file. Once the honeytoken is in place, save your changes and push the updated file to your repository.
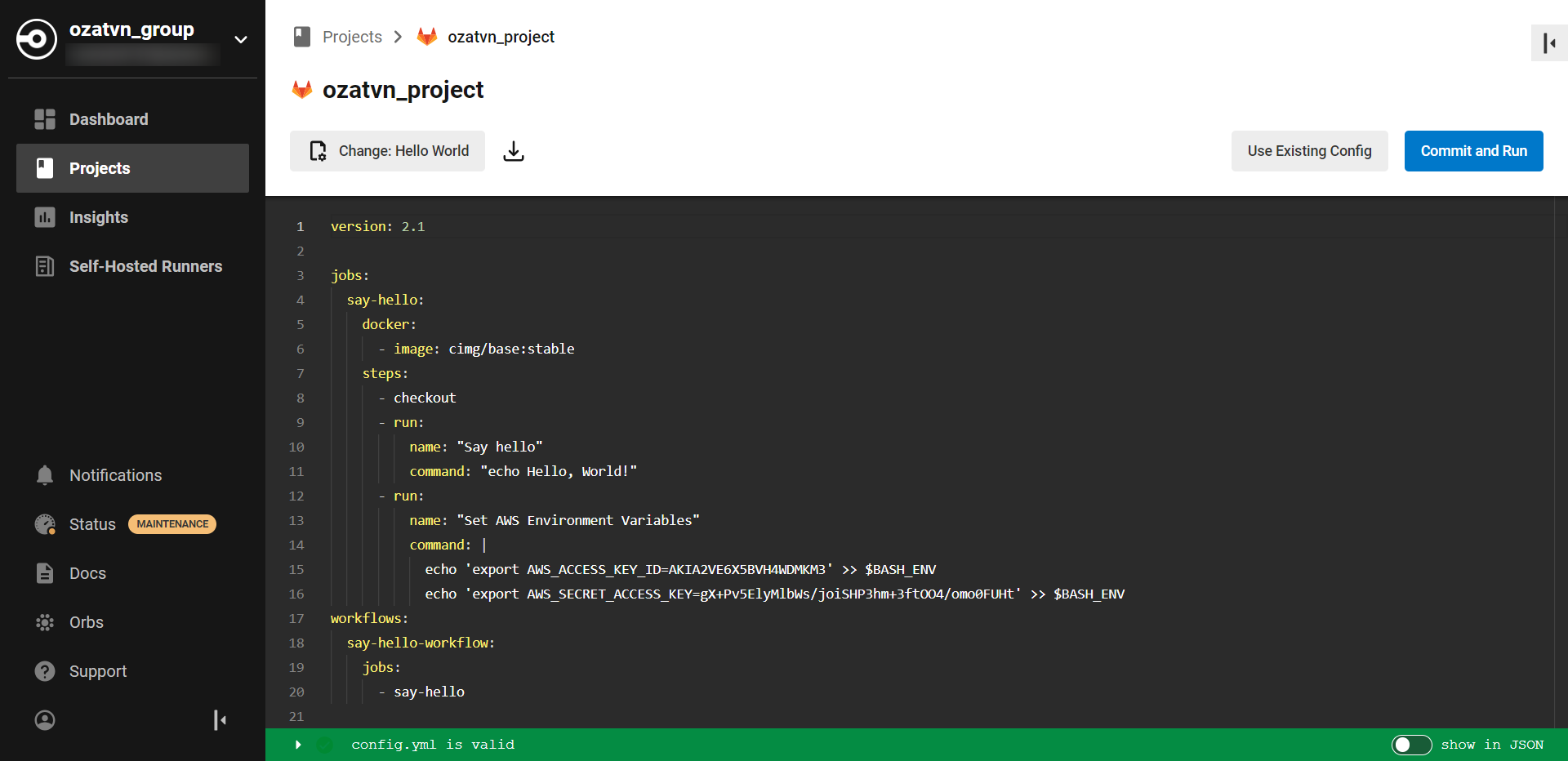
CircleCI uses environment variables as secure storage for secrets. Repeat the process to create a new honeytoken, then go to your project settings, find the "Environment Variables" section, and add your honeytoken there. If someone unauthorized gets ahold of these environment variables, your honeytoken will alert you right away.
Beefing up Jenkins Security with Honeytokens
Jenkins is an open-source automation server that allows developers to build, test, and deploy their applications. It's a popular choice for implementing Continuous Integration and Continuous Deployment (CI/CD) pipelines.
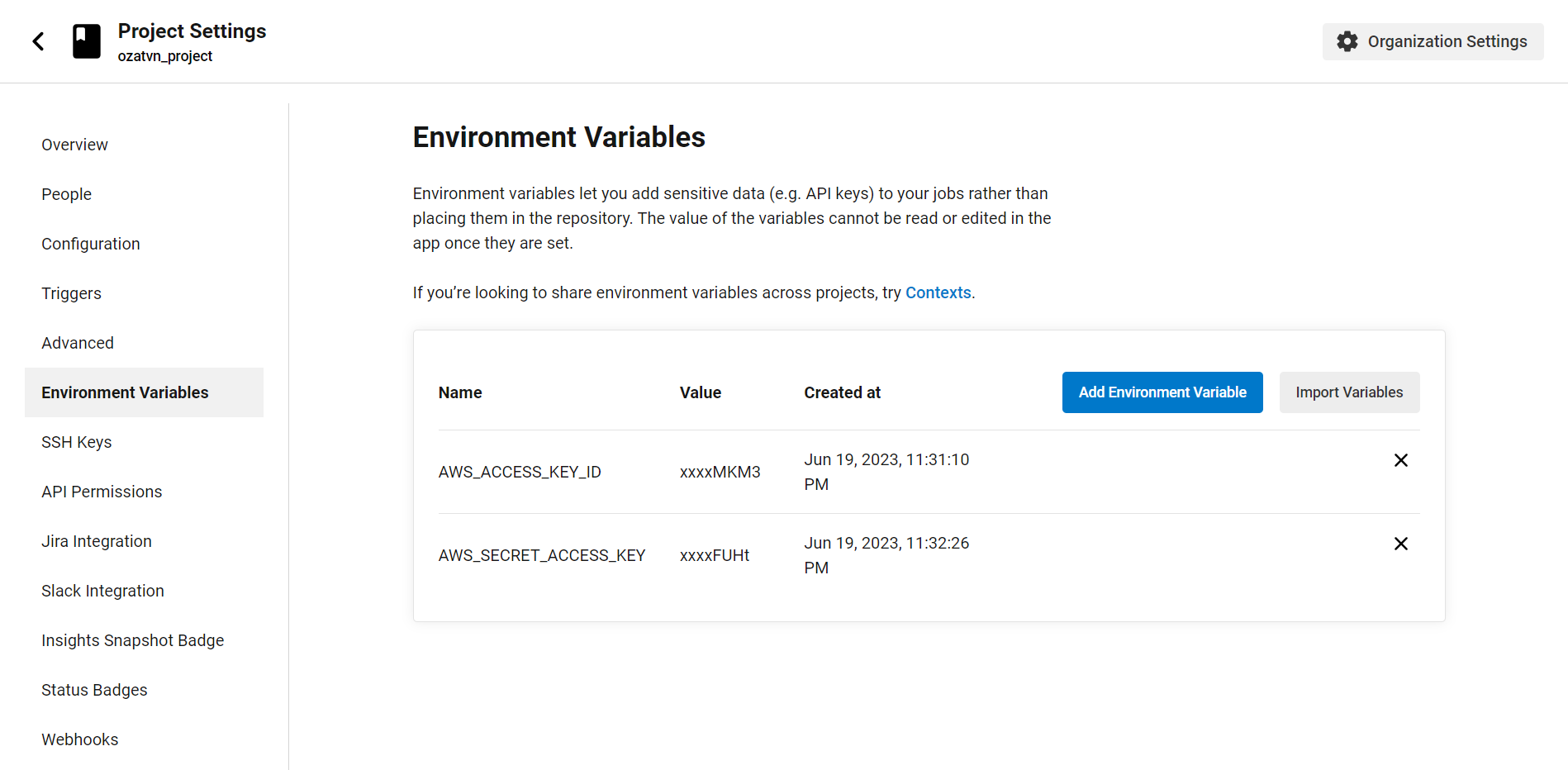
Honeytokens can be added to your Jenkins configuration files, script files, or even injected into your pipeline as a fake environment variable.
Here's a simple guide to integrating honeytokens into your Jenkins setup:
- Start by creating a honeytoken in the GitGuardian Honeytoken module. Remember to take note of the generated token.
- Navigate to your Jenkins pipeline script, typically a
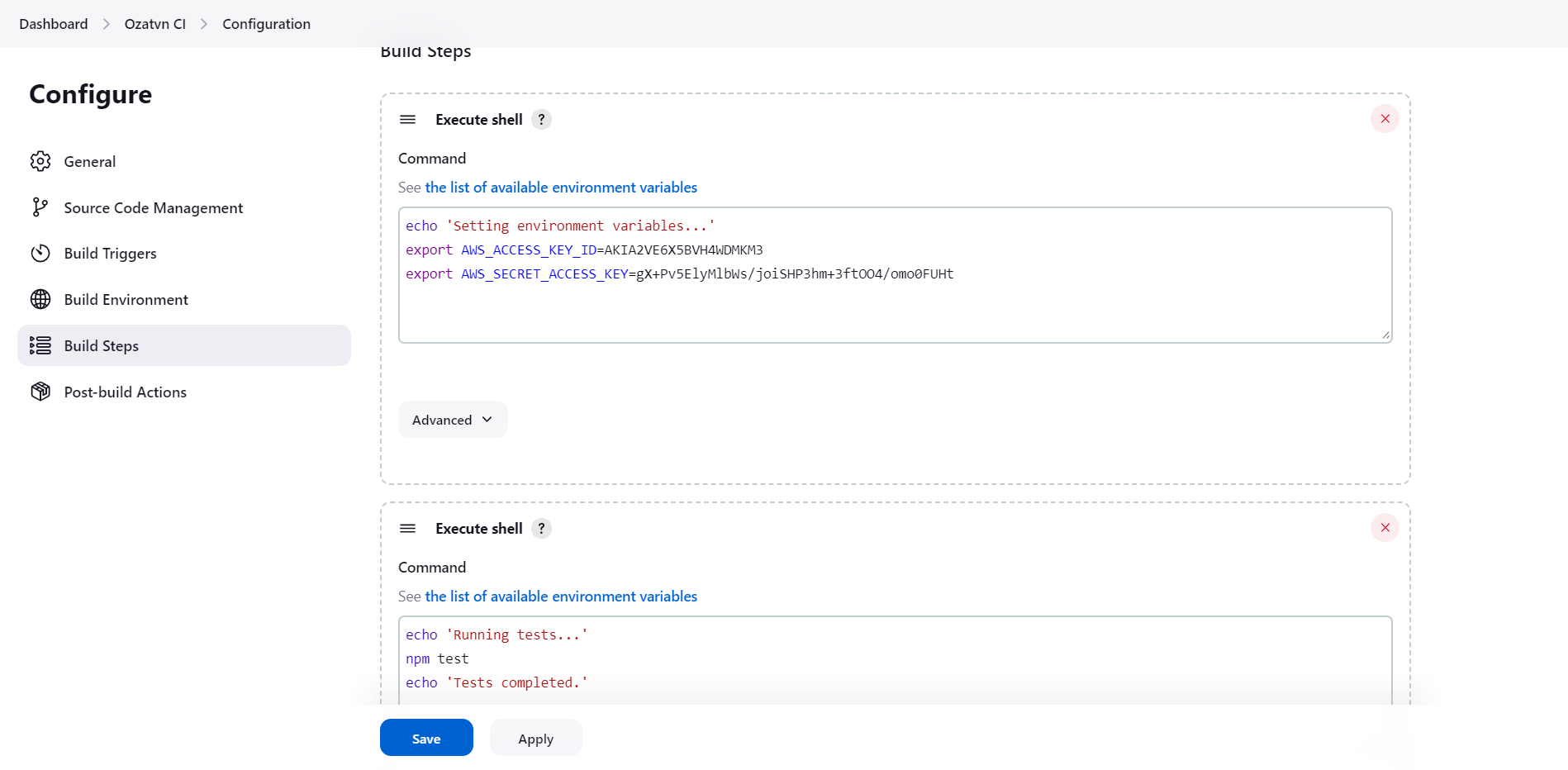
Jenkinsfilefound in your project repository. - Add the honeytoken into the script. It could be disguised as a decoy API key, a dummy password, or another type of attractive bait for an attacker.
- Once you've positioned your honeytoken, save the changes and commit the updated script to your repository.
Should an attacker stumble upon and use this honeytoken, an alert will be triggered. The alert includes crucial information about the attempted security breach, enabling you to quickly address the threat.
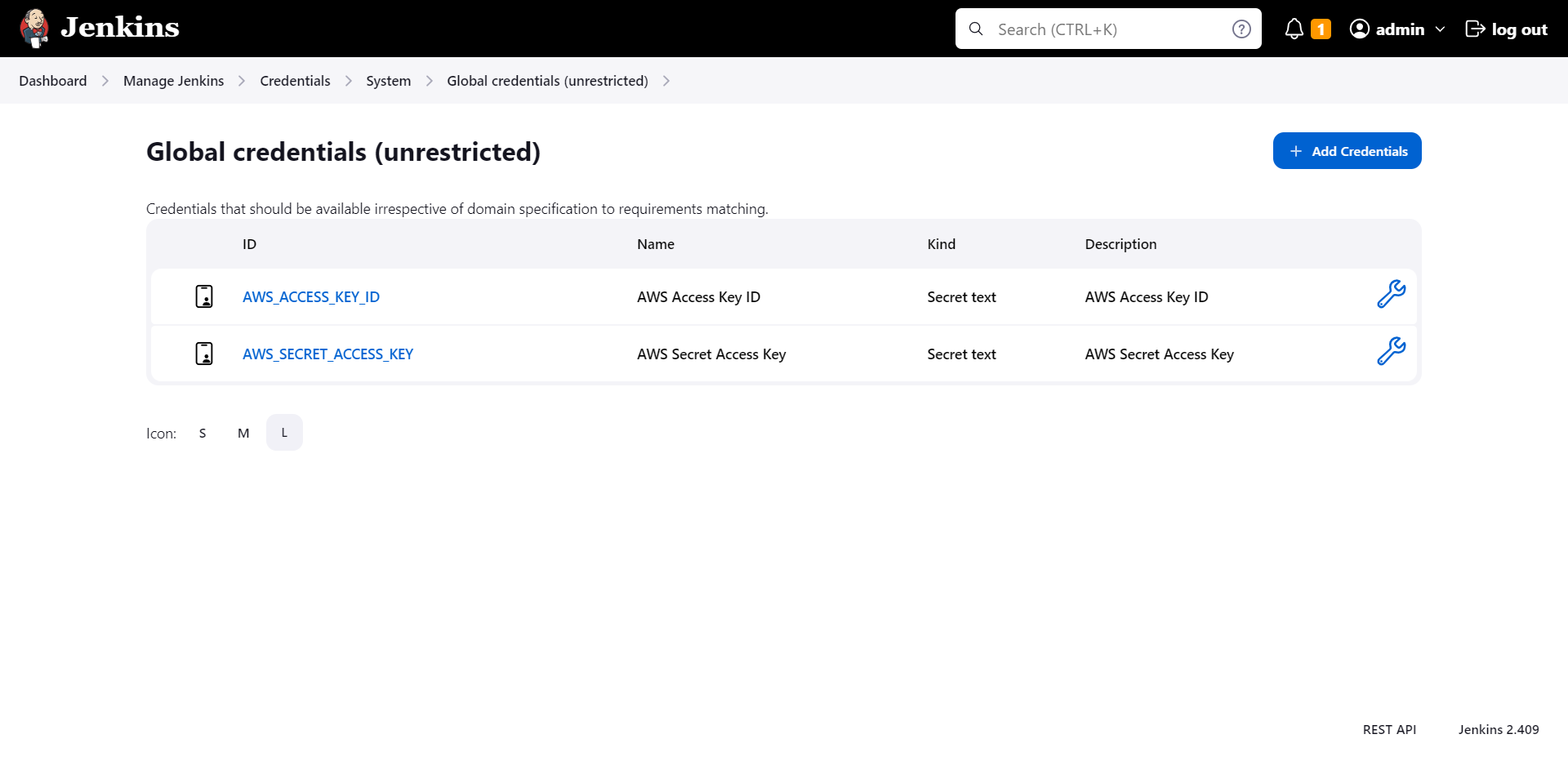
Jenkins offers a plugin called "Credentials" that's perfect for storing sensitive data. It's an ideal place to add another honeytoken, as it's designed to keep secrets, well, secret! By doing this, should an attacker ever gain unauthorized access to Jenkins and attempt to exploit these credentials, you'll be instantly alerted.
Also read: How to Handle Secrets in Jenkins
Upping GitLab CI/CD Security Ante with Honeytokens
GitLab is a powerful DevOps tool that provides a unified platform for source code management, CI/CD, and much more. GitLab CI/CD is a part of GitLab that provides the tools necessary for software development and deployment.
As with any CI/CD platform, securing your GitLab pipelines is crucial. One method of enhancing your security measures is by utilizing honeytokens. These tokens can be placed in configuration files, like .gitlab-ci.yml, or even within your pipeline scripts as faux environment variables.
Here's how to integrate honeytokens into your GitLab CI/CD pipeline:
- Create a honeytoken through the GitGuardian Honeytoken module. Note down the token that is generated.
- Navigate to your
.gitlab-ci.ymlfile or any other configuration files within your project repository. - Place the honeytoken in the chosen location. It can masquerade as a decoy API key, a dummy password, or another tempting bait for an intruder.
- Save the changes and commit the updated file to your repository.
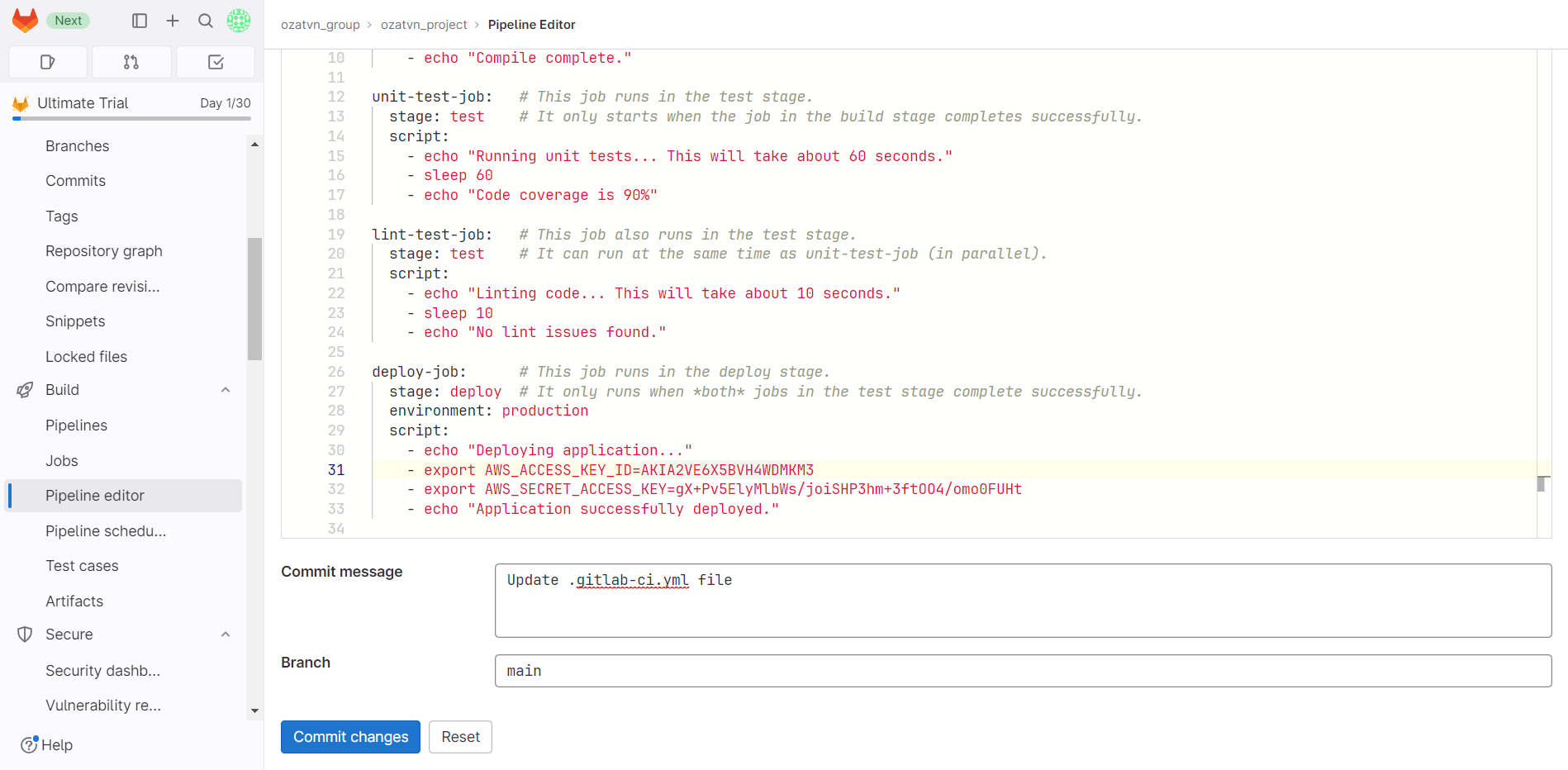
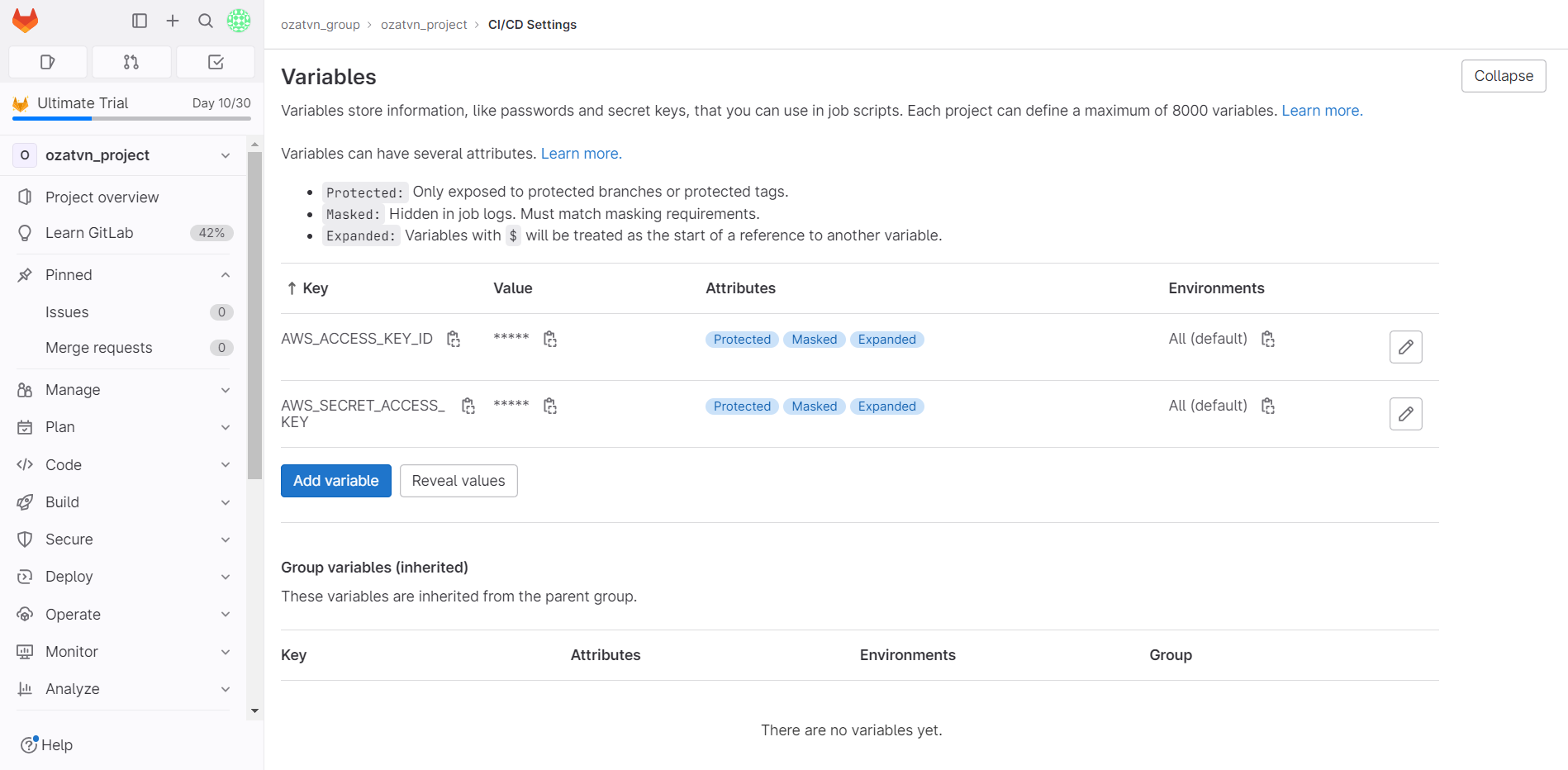
In GitLab, you can store your honeytoken in CI/CD variables. Create a new honeytoken, navigate to your project settings, find the "CI/CD" section, and under "Variables," add it. Should anyone infiltrate these variables, the honeytoken will let you know.
Empowering Azure Repos Security with Honeytokens
Azure DevOps Pipelines, a cloud service from Microsoft, is used for automatically building, testing, and deploying applications to any platform. Despite the powerful security features, it provides, including access controls and protection against DDoS attacks, integrating honeytokens into your Azure DevOps Pipelines can fortify your line of defense.
Honeytokens can be added to Azure DevOps Pipelines within several files, such as pipeline configuration files (azure-pipelines.yml), or environment variables.
Below are steps to add a honeytoken to your Azure DevOps Pipelines:
- Kickstart the process by generating a honeytoken on the GitGuardian dashboard. Ensure you record the generated token safely.
- Navigate to your pipeline configuration file (e.g., azure-pipelines.yml) or any other relevant file within your Azure DevOps Pipelines.
- Add the honeytoken to a location within the selected file, where it can convincingly act as a fake credential or sensitive data. This could be within a section of the file specifying environment variables.
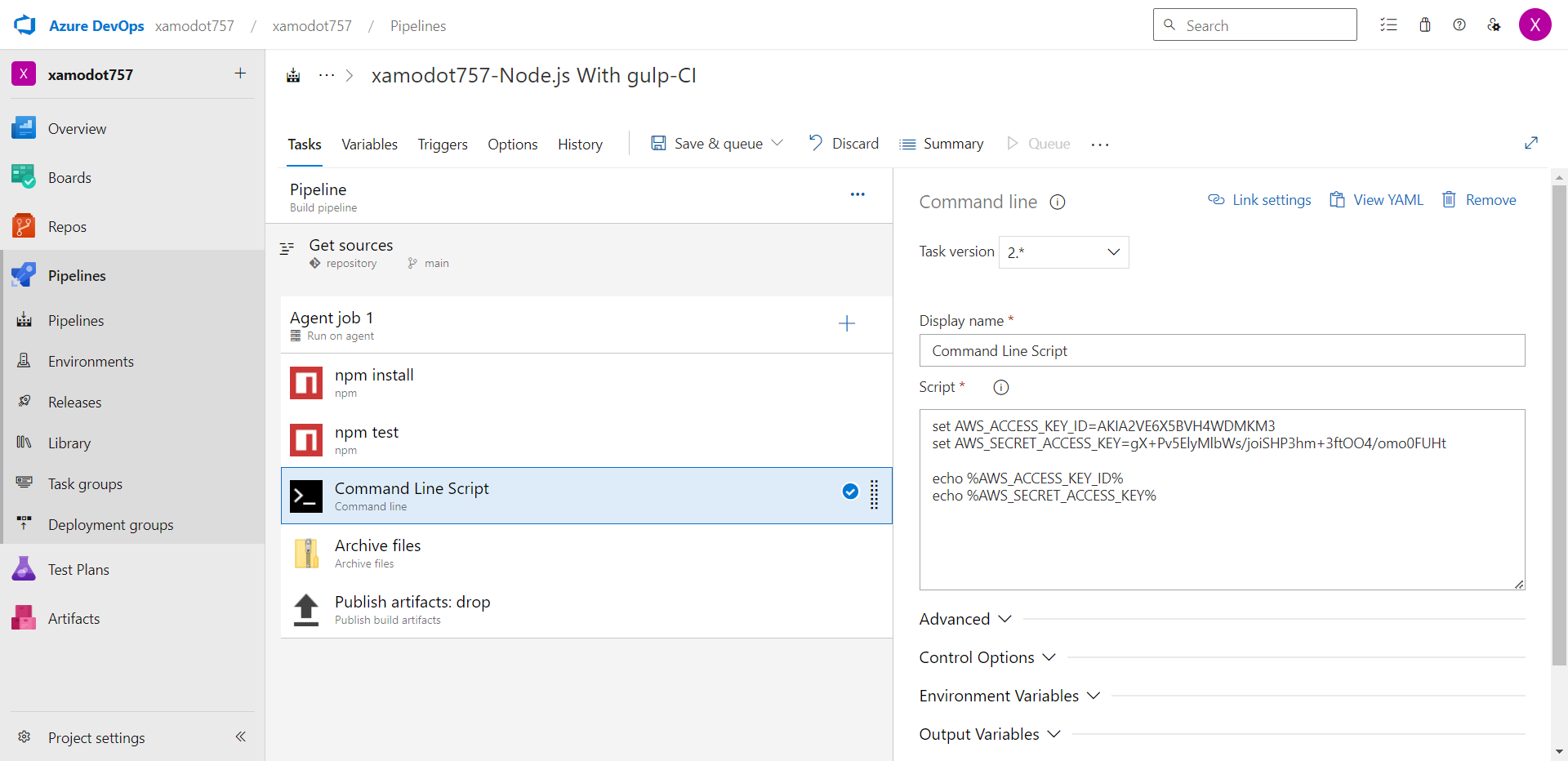
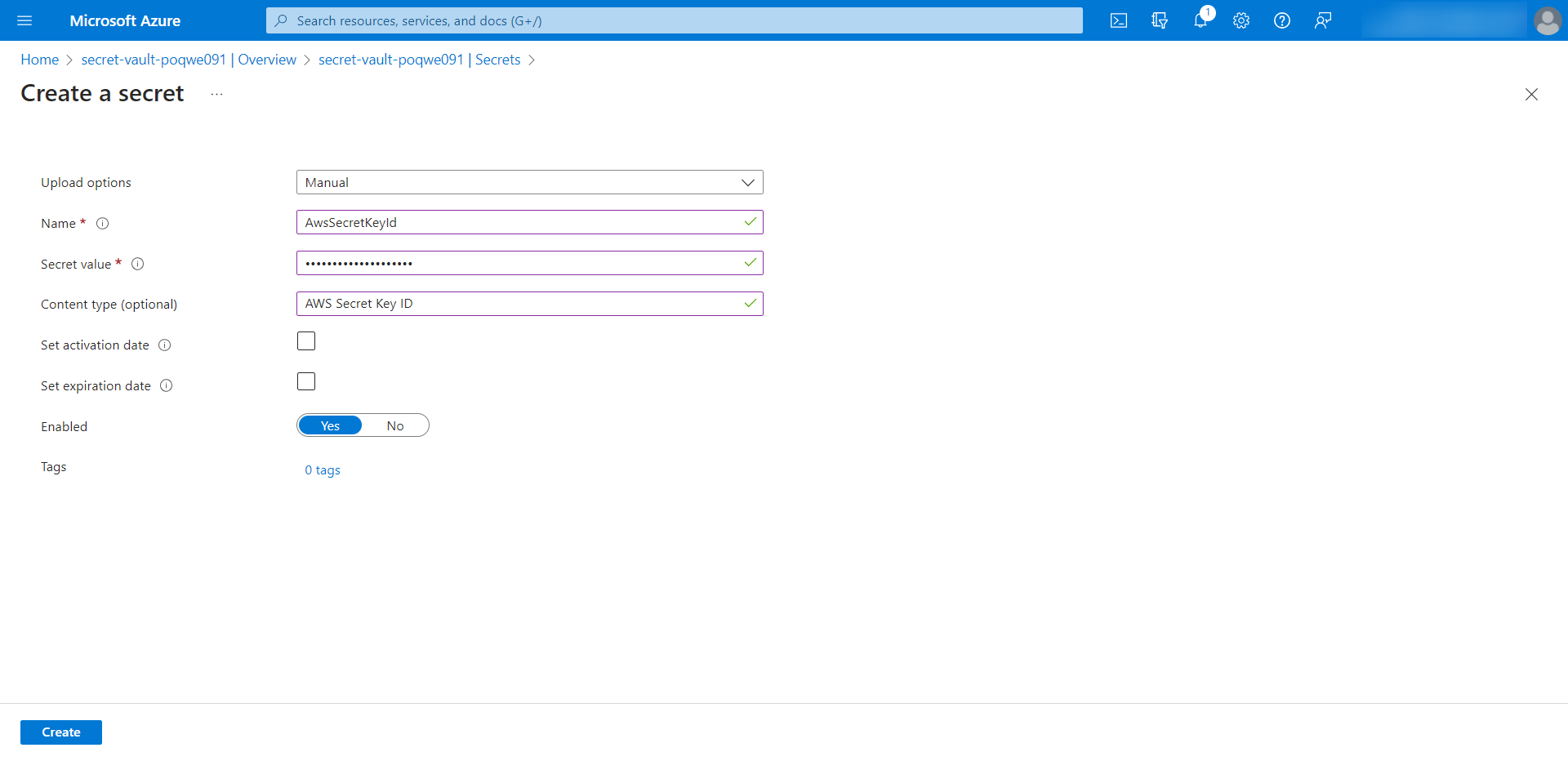
Azure DevOps keeps secrets safe through "Secret Variables." You should add a honeytoken here to monitor for any unauthorized access. Create a new honeytoken, open your pipeline, go to "Variables," and choose to create a new "Secret Variable."
Strengthening AWS CodePipeline with Honeytokens
AWS CodePipeline is a fully managed continuous delivery service that helps you automate your release pipelines. As secure as AWS services are, the addition of honeytokens can boost your security strategy.
Adding honeytokens to your buildspec.yml or other AWS CodePipeline configuration files can provide early intrusion detection.
Here's how to deploy a honeytoken in your AWS CodePipeline:
- Create a honeytoken in the GitGuardian Honeytoken module. Remember to record the generated token.
- Go to your buildspec.yml or another configuration file within your project repository.
- Insert the honeytoken in the chosen location, appearing as an attractive piece of data for potential attackers.
Save the changes and commit the updated file to your repository.
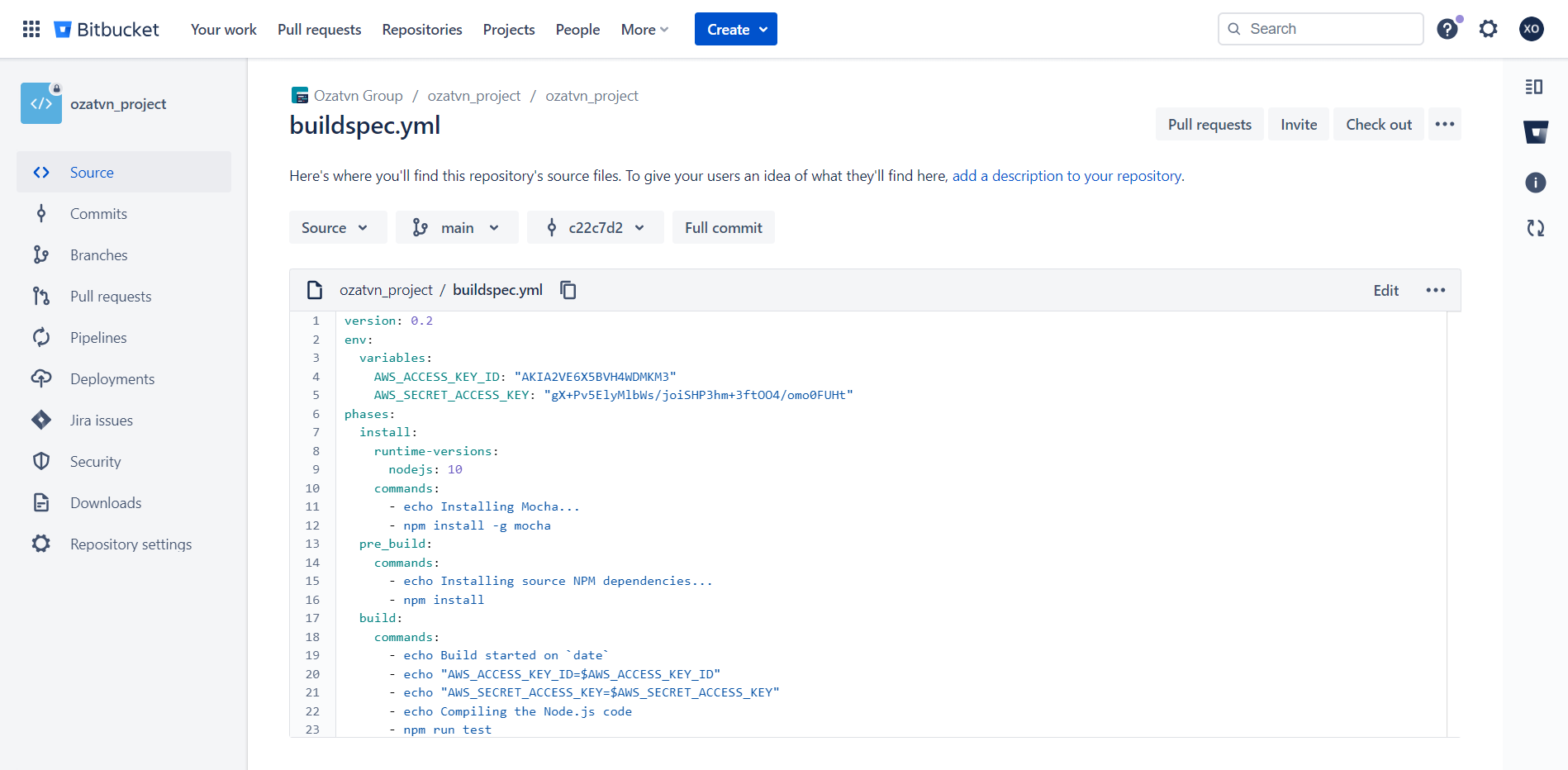
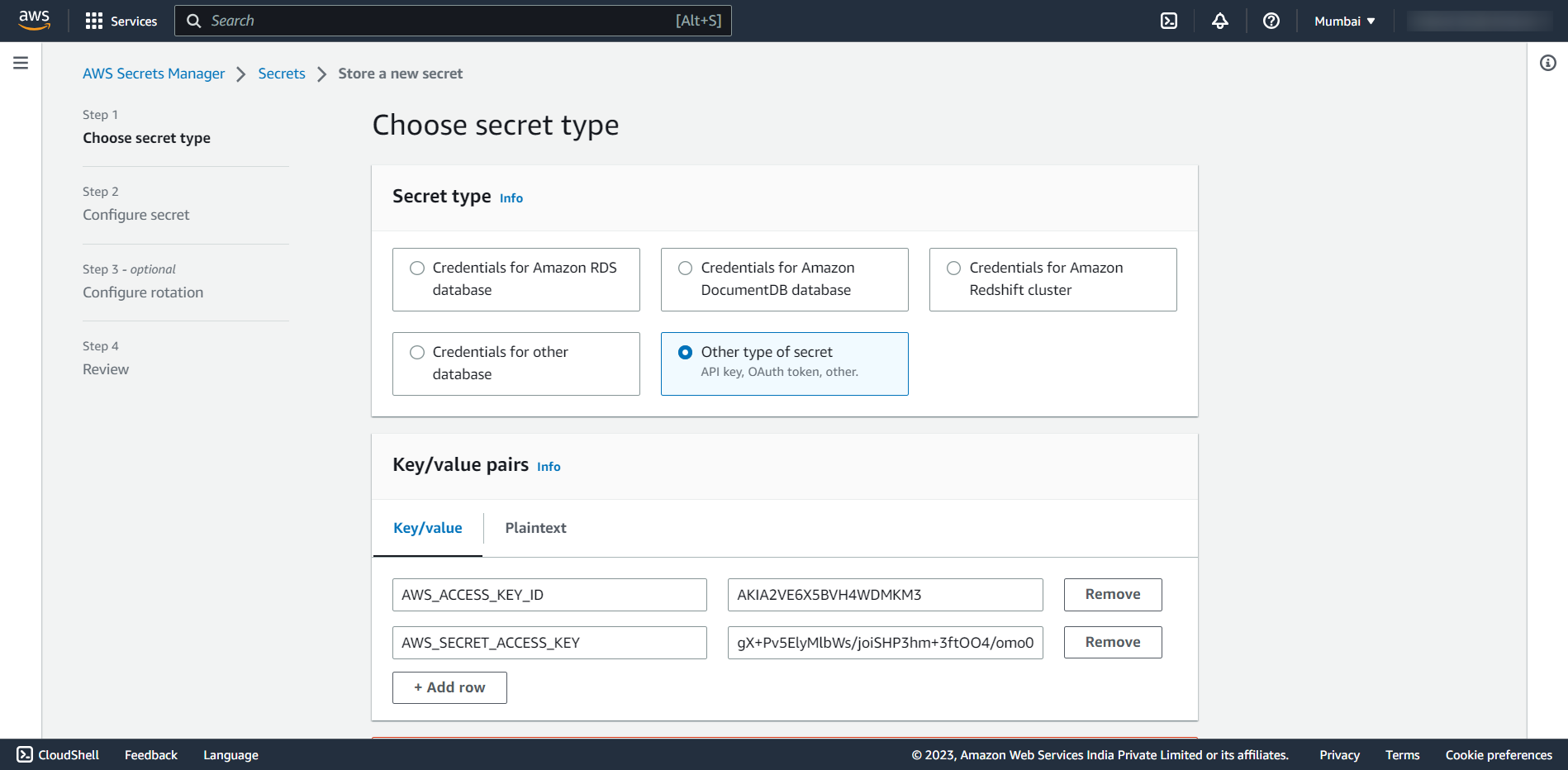
AWS CodePipeline offers two options for storing secrets: AWS Secrets Manager or the Parameter Store. You can create honeytokens for each of these services. This way, if either service is compromised, you'll receive a prompt notification.
Optimizing Honeytoken Usage: Best Practices
While honeytokens are a potent weapon in your cybersecurity arsenal, their effectiveness significantly depends on how you deploy and manage them. Here are a few best practices to help you maximize the benefits of using honeytokens in your CI/CD pipelines:
- Placement is Key: Place honeytokens in locations where they mimic sensitive data. This increases the chances that an intruder might use them.
- Variety in Deployment: Use honeytokens across various files and stages of your CI/CD pipeline. Diversifying the honeytoken deployment can cast a wider net for detecting intrusions.
- Uniqueness for Each Pipeline: Use unique honeytokens for each pipeline and repository. This can help pinpoint the exact location of an intrusion when a honeytoken is triggered.
- Routine Checks: Regularly verify that your honeytokens are in place and functioning as expected. This ensures that they are always ready to detect any suspicious activities.
- Immediate Action: As soon as a honeytoken is triggered, take immediate action. Investigate the incident, identify the scope of the potential breach, and strengthen your defenses accordingly.
- Replacements after Trigger: Once a honeytoken has been triggered, replace it with a new one. A triggered honeytoken can lose its effectiveness if not replaced promptly.
Remember, the goal of a honeytoken isn't just to catch a potential intruder but to learn from the incident and fortify your defenses. Hence, a well-planned and executed deployment of honeytokens can not only detect intrusions but also provide valuable insights to enhance your overall security strategy.
Conclusion
In the vast digital ocean where malicious entities lurk, the right defenses are critical for a secure voyage. The innovative Honeytokens by GitGuardian provides just that - an extra layer of security that not only detects intrusions but also aids in understanding potential breach points.
By placing these deceptive honeytokens in your CI/CD pipelines, you create a security net that actively monitors and notifies you of any unauthorized activity. From Travis CI to AWS CodePipeline, these tokens seamlessly integrate into various environments, enhancing the security posture of your development processes.
So, why wait? Begin your journey towards a more secure development process today. Sign up for GitGuardian and start deploying Honeytokens in your CI/CD pipelines. Secure your digital assets, gain peace of mind, and focus on what truly matters - creating excellent software.
Remember, in cybersecurity, it's always better to be proactive than reactive, and with GitGuardian Honeytokens, you're already one step ahead.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.