Protecting sensitive data is a crucial responsibility for modern businesses. To ensure the security of critical information, organizations utilize various tools and strategies.
One such tool is a secrets manager, which securely stores and manages sensitive data like passwords, API keys, and encryption keys. Secrets managers offer a centralized and encrypted repository, providing a secure alternative to storing secrets in configuration files or source code. Popular secrets managers include CyberArk (GitGuardian and CyberArk have developed a joint solution for comprehensive secret security), AWS Secrets Manager, Doppler, Hashicorp Vault and Akeyless.
In this blog, we will explore how GitGuardian Honeytoken can enhance the security of secrets managers by enabling easy and scalable breach detection.
Understanding Honeytokens
Honeytokens are digital baits designed to lure attackers into a trap. They have no permissions attached and serve as alerts when unauthorized users attempt to use them.
When a honeytoken is triggered, it alerts you of the intrusion and provides crucial information about the attacker, such as their IP address and user agent. By storing honeytokens in a secure environment like a secrets manager, you can effectively detect and respond to unauthorized access attempts.
In the upcoming section, we will guide you on how to place a honeytoken in your Hashicorp Vault instance, but these guidelines are applicable to any other secrets manager.
Enhancing Secrets Manager Security with Honeytokens
Hashicorp Vault is a popular secrets manager that securely stores and controls access to sensitive elements in a DevOps environment. While Vault provides advanced security features, the possibility of an instance compromise cannot be completely eliminated.
Attackers understand the value of compromising a secrets manager, as it can provide them with access to sensitive information and facilitate lateral movement within your system. Integrating GitGuardian Honeytoken with Vault adds an additional layer of security, alerting you to any unauthorized attempts to access your secrets.
Integrating GitGuardian Honeytoken with Vault (or any Secrets Manager)
Before integrating GitGuardian Honeytoken, ensure that Vault is installed and running in your environment.
Installing Vault:
- Download the latest version of Vault from the official website.
- Extract the downloaded file in a directory of your choice.
- Add the Vault binary to your system
PATHfor easy access.
Configuring Vault:
- Initiate the Vault server with the appropriate configurations for your organization.
- Initialize Vault to create initial tokens and unseal keys that are critical for Vault's operations.
Using GitGuardian Honeytoken:
- Sign in to your GitGuardian account and navigate to the Honeytoken section.
- Create new honeytokens with a descriptive name and description
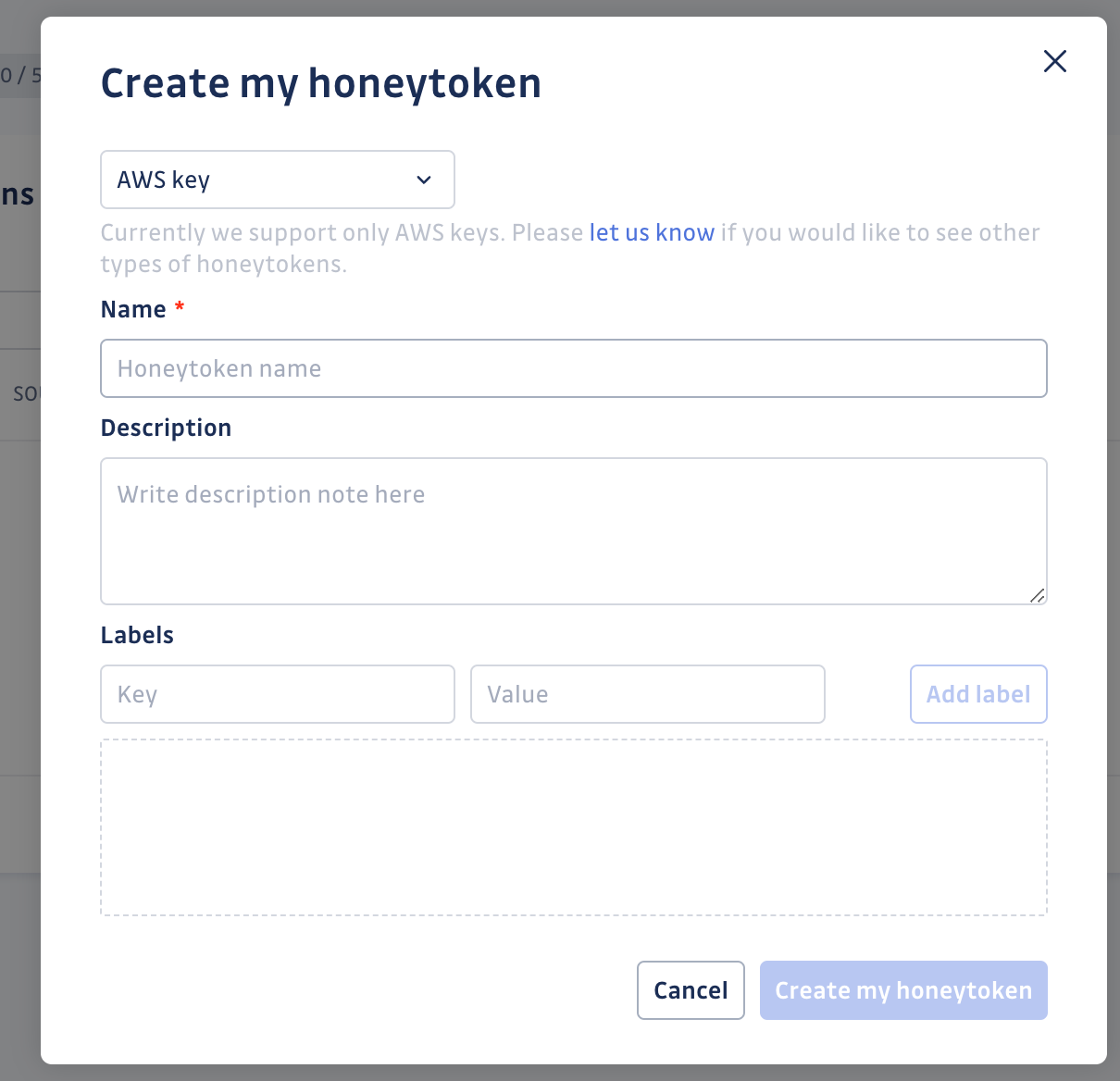
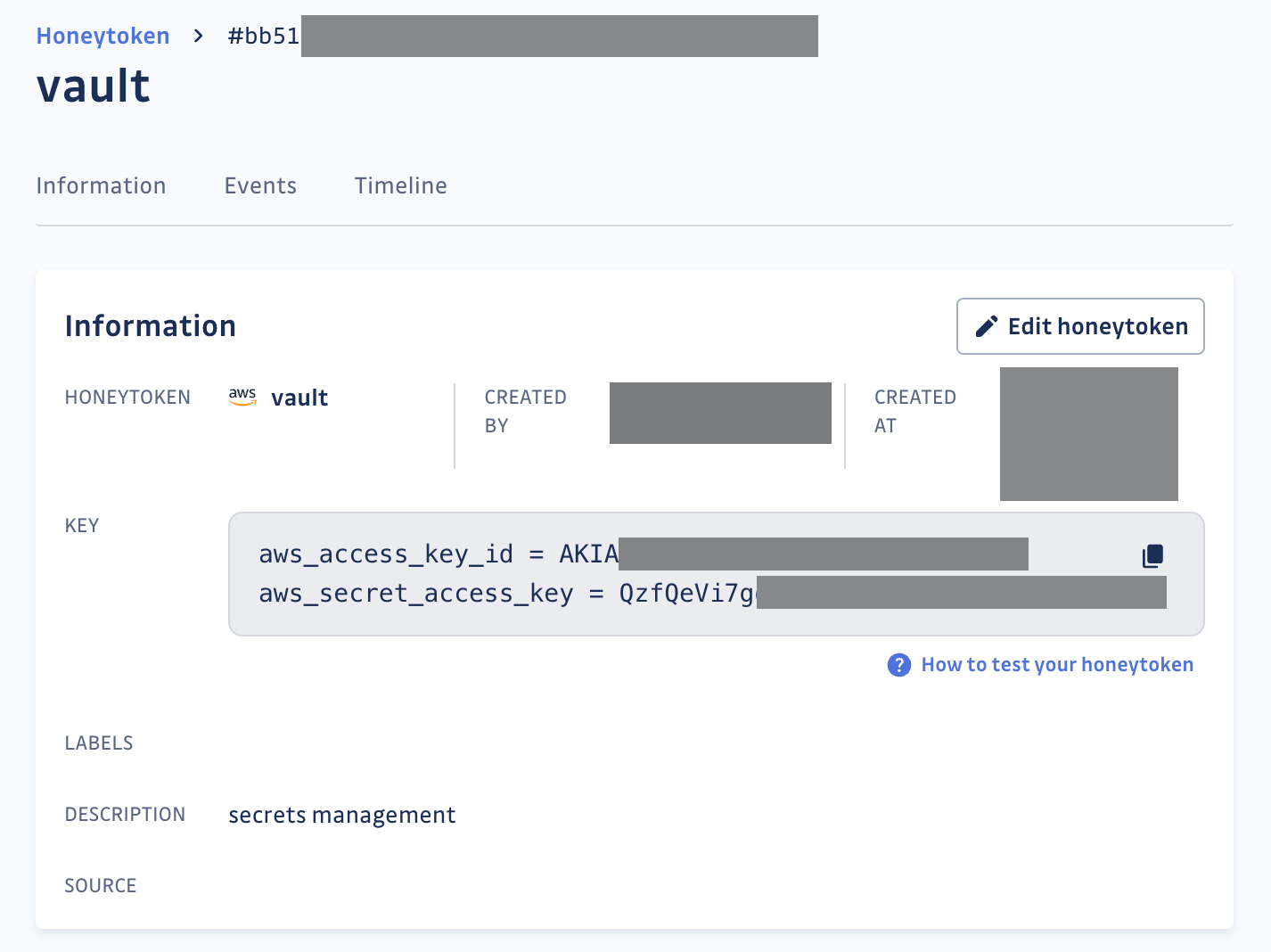
- Note down the keys (AWS Access and Secret Keys), as these will be used later in Vault.
Integration Procedure: Step-by-Step Guide
Vault supports multiple secret engines, and for simplicity, we will consider the key value (KV) secret engine. This engine is a generic Key-Value store used to store arbitrary secrets within Vault.
First, ensure that your Vault cluster is reachable by running the command:
vault statusIf you get an error message, follow Vault's Lab Setup instructions here.
Next, verify that the KV secrets engine is enabled and set to version 2 at the secret/ path. This should be the default configuration if you started a dev server.
vault secrets list -detailed
Path Type Accessor ... Options Description
---- ---- -------- ------- -----------
cubbyhole/ cubbyhole cubbyhole_9d52aeac ... map[] per-token private secret storage
identity/ identity identity_acea5ba9 ... map[] identity store
secret/ kv kv_2226b7d3 ... map[version:2] key/value secret storage
...Finally, write the previously generated AWS secret values at the path of your choice:
vault kv put secret/aws aws_access_key_id ="AKIA..." \
aws_secret_access_key = "QzfQeV..."
If everything went well, you should see this output:
====== Secret Path ======
secret/aws
======= Metadata =======
Key Value
--- -----
created_time <CREATION_TIME>
custom_metadata <nil>
deletion_time n/a
destroyed false
version 1This confirms that your bait credentials have been set. If you receive an email alert about this honeytoken being triggered, you can assume that your secrets manager is compromised.
You can further configure your alerts to receive instant notifications through custom webhooks, allowing you to customize your alerting workflow.
Benefits of protecting your Secrets Manager with Honeytokens
Taking proactive measures to secure sensitive information is both prudent and essential. There are a number of security benefits of integrating GitGuardian Honeytoken with Vault:
- Proactive Breach Detection: By integrating GitGuardian Honeytoken with Vault, you can proactively detect and respond to potential breaches. Honeytokens act as a silent alarm, alerting you when unauthorized users attempt to use them. This allows you to take immediate action and strengthen your system's security.
- Enhanced Threat Intelligence: Honeytokens provide valuable information about the actions taken by intruders, such as their IP address and user agent. This information helps you analyze and understand the threat, enabling you to further secure your system and track down the attackers.
- Scalable Solution: GitGuardian Honeytoken offers a scalable solution for breach detection. You can create and deploy multiple honeytokens, strategically placing them in your secrets manager to effectively deceive attackers. This scalability ensures comprehensive coverage and protection for your critical assets.
- Customizable Alerting Workflow: GitGuardian Honeytoken allows you to configure custom alerts through webhooks. This flexibility enables you to tailor your alerting workflow according to your specific requirements, ensuring that you receive instant notifications when a breach is detected.
Conclusion
By securing your secrets manager with GitGuardian Honeytoken, you can significantly enhance the security of your sensitive information. The proactive breach detection, enhanced threat intelligence, easy integration, scalability, and customizable alerting workflow provided by honeytokens make them a valuable addition to your security arsenal. Follow the step-by-step instructions in this blog to get started and protect your critical assets effectively.
See upcoming sessions