
Protecting Developers Means Protecting Their Secrets
Secrets don’t just leak from Git. They accumulate in filesystems, env vars, and agent memory. See how to find them, stop the bleed, and protect your whole supply chain

Secrets don’t just leak from Git. They accumulate in filesystems, env vars, and agent memory. See how to find them, stop the bleed, and protect your whole supply chain

Vault sprawl means duplicated secrets, fragmented access, and unclear ownership. Learn how GitGuardian's NHI Governance restores control across the enterprise.

In such a fast-developing world, it becomes more and more important to make sure the source code and its metadata are backed up in case of an emergency. Learn everything you need to know about how to backup a GitHub repository.

GitHub is hardening npm publishing rules but the underlying lessons can be applied by all developers: WebAuthn for writes, OIDC, and short-lived least-privilege credentials.

DevOps engineers must handle secrets with care. In this series, we summarize best practices for leveraging secrets with your everyday tools.

From entering passwords with getpass to using secret managers like AWS Secrets Manager, this guide covers best practices for protecting sensitive information in your notebooks.

DevOps engineers must handle secrets with care. In this series, we summarize best practices for leveraging secrets with your everyday tools.

AI adoption accelerates secret sprawl as organizations connect to multiple providers. Our investigation of a leaked xAI API key, which granted access to unreleased Grok models, reveals critical flaws in their disclosure process, highlighting necessary improvements in this domain.
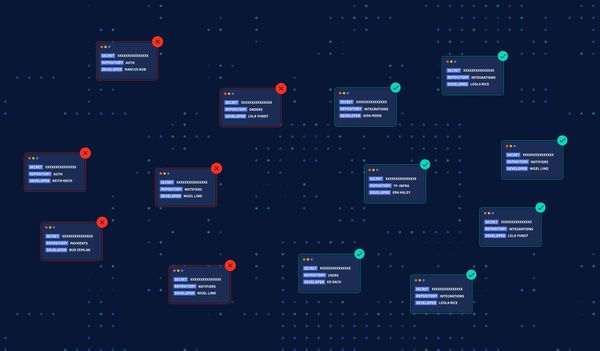
This article aims to provide application security teams with a guide to effectively prioritize, investigate and remediate hardcoded secrets incidents at scale.

We have compiled a list of some of the best practices to prevent API key leakage and keep secrets and credentials safe. Secrets management doesn’t have a one-size-fits-all approach, so this list considers multiple perspectives so you can be informed in deciding to or not to implement strategies.

Not only API authentication and authorization are the crucial aspects of API security when crafting secure software, but they also impact scalability and user experience.

Building positive relationships, sharing knowledge effectively, and making security "cool" are some of the most worthwhile security pursuits.