This is a journey that's taken us through twists and turns, challenges and triumphs. We are excited to take you behind the scenes of a project that's been close to our hearts and has ignited conversations in the tech world. We're diving into the journey of GitGuardian Honeytoken, a story of innovation, security, and a touch of digital intrigue.
Let's start with what Honeytoken is all about. At its core, it's a decoy hardcoded secret that can trigger alerts when used, reducing your mean time to detect any potential intrusions. In a keynote titled "The State of Cybersecurity – Year in Review," Mandiant/Google Cloud CEO Kevin Mandia underscored the significance of honeytokens as an indispensable tool for detecting intruders, particularly in scenarios where other security products might fall short. This sentiment resonates deeply with us. Our journey with Honeytoken began three months ago when we launched it in beta. This phase has been instrumental in refining our creation and gathering valuable feedback from our users. And now, with pride, we announce that Honeytoken has emerged from its cocoon, ready to make an impact on all our customers.
We have showcased Honeytoken's potential at conferences like DEFCON, Bsides, and RSA. We guided numerous individuals through a blue team capture the flag exercise that showcased the power of using honeytokens in detecting potential leaks. This simple yet powerful concept sparked thought-provoking discussions and was fueled by genuine curiosity and excitement. These interactions reinforced the importance of what we were building.
So, why did we venture into the realm of Honeytoken?
The answer lies in the increasingly intricate supply chain of modern software. In a world where safeguarding applications and cloud security is paramount, the reality is that achieving zero risk remains a challenging goal, even if you do everything by the (security) book. Hackers today have mastered the art of exploiting secrets, seeking that one flaw in the armor that grants them access to scores – even millions – of potential target companies.
We witnessed this rise in ecosystem-style supply chain attacks that exploit secrets. A notable example is the CircleCI incident, where attackers accessed a CircleCI engineer's endpoints. From there, they used the secrets they found in the source code to gain higher privileges and move around within the organization. They accessed production databases, GitHub OAuth tokens of CircleCI customers, and other sensitive build information.
Interestingly, one savvy CircleCI customer had set up an AWS honeytoken alongside their actual build secrets. This acted as a decoy, and when the attacker tried to scan for secrets, they triggered this honeytoken. This alerted the user to the potential compromise, and they promptly informed CircleCI about the issue. This customer was among the first to know about the breach, even before it was officially disclosed.
Sometimes, it's not just your own account that's compromised due to leaked credentials or brute force attacks. Remember that providers can also be breached, and attackers will attempt to access their customers' secrets.
It struck us deeply how companies often took too long – sometimes months – to realize when their dev and build environments had been breached. This is why we believe that an additional layer of intrusion detection is critical for organizations that want to stay ahead of attackers.

The solution was clear. Instead of passively defending, we decided to outsmart potential attackers by deliberately exposing decoy secrets in users’ supply chains, tempting attackers to exploit them for further lateral movement. And thus, GitGuardian Honeytoken was born. Our honeytokens safeguard not only your code but also the vendors in your software supply chain. Defenders’ can now use secrets to their advantage to detect once attackers have breached their systems and contain the breach early before they can inflict any significant damage.
With the Honeytoken dashboard or API, users can effortlessly create and manage hundreds, or possibly thousands, of honeytokens. This flexibility allows for wide coverage across all systems, ensuring comprehensive security. They are agnostic and can be strategically scattered anywhere across the software delivery pipeline to trick and trap attackers. Whether it's Source Control Management, Continuous Integration & Continuous Deployment, software artifact registries, productivity tools, or even developer laptops, these decoy AWS access keys beckon malicious actors. Even beyond the software realm, our honeytokens extend their protective reach into the cloud infrastructure. Placing honeytokens in cloud assets such as S3 buckets or databases ensures that attackers attempting to infiltrate your cloud infrastructure without access to the code are promptly detected and trapped.
Little do attackers know, these traps never grant access to actual customer data or systems. Instead, these decoy access keys serve as early breach detection triggers, generating high-fidelity alerts that not only notify security teams but also provide valuable information about the intrusion's source.
In most cases, attackers follow predictable patterns. Instead of manually searching for secrets, they often rely on open-source secrets scanning tools like TruffleHog and GitLeaks. This means the file names or how the decoy secrets are placed don't have to be overly convincing. We designed our honeytokens to be triggered by all types of tools that scan for secrets, effectively fooling attackers into exposing themselves.
Honeytoken is a tailored solution designed to thwart DevOps intrusions. While the concept isn't new, having a way to detect real-time intrusions in the supply chain was missing. We saw that traditional methods like honeypots had their limitations, so we set out to create a simpler and more cost-effective solution. Honeytokens are much easier to implement, maintain, and manage than honeypots since there's no additional cloud infrastructure to handle on your end. Plus, with the automated dissemination of honeytokens, you will need fewer resources.
During the beta phase, we introduced several key features of Honeytoken that received overwhelmingly positive feedback from our users. Here's a closer look at these features and why they garnered acclaim.
Key Honeytoken features
Centralized management dashboard for honeytokens
The intuitive user interface provides a centralized view of all honeytokens associated with your workspace. This feature allows for easy oversight, ensuring that honeytokens are effectively placed and monitored.
Honeytokens are, by default, listed by most recently created first. Each honeytoken is characterized by its name, type, and optional description, providing contextual clarity. The source field indicates the repository location where the honeytoken is detected upon deployment in your private repos.
The labels you create offer flexibility for easy categorization and organization, ensuring precise placement of honeytokens. For effective tracking, statuses include Active, Triggered, and Revoked, with triggered honeytokens displaying the trigger date. The filtering options facilitate quick access and prioritization of your events.

Instant alerts for triggered and publicly exposed honeytokens
The platform promptly sends email alerts with crucial details whenever a honeytoken is triggered. This ensures you're at the forefront of any potential threat, enabling swift action when needed.
Your security operations or SOC teams are instantly notified, integrating the incident into your workflow, be it your security information and event management (SIEM), IT service management (ITSM), or ChatOps systems. Based on threat indicators, you can determine whether additional action or an incident response plan is warranted.
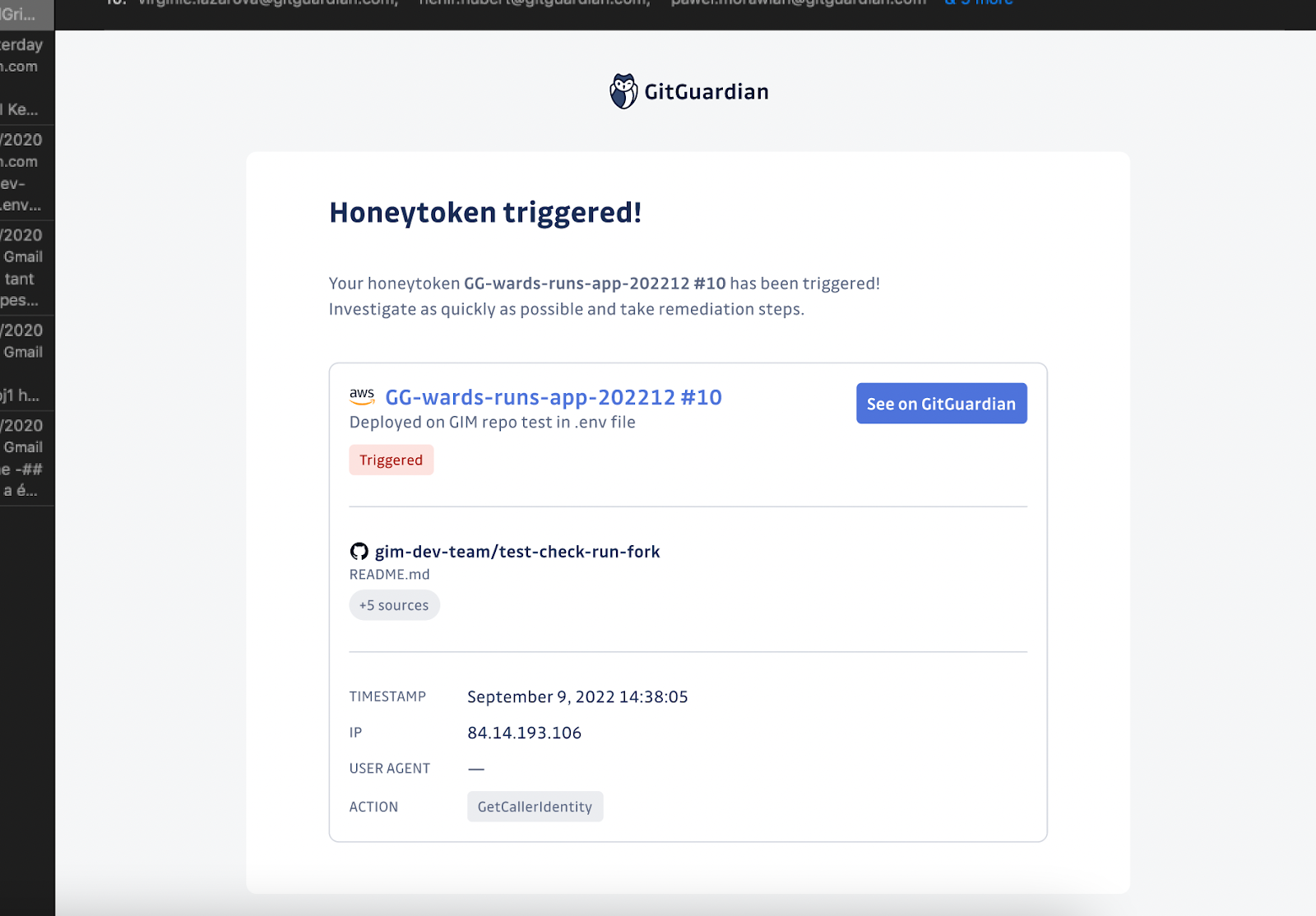
Source detection
The GitGuardian platform recognizes the location (including the repository and file name) of a deployed honeytoken within your perimeter. This ensures accurate tracking and monitoring of honeytokens in private repositories.
On the honeytoken detail page, you'll find the number of open secrets incidents detected in that repository, along with a direct link to the repo and file. If that honeytoken is triggered, you need to tackle those secrets first.

This way, Honeytoken works in tandem with the platform's Secrets Detection capabilities.
Integrated into the GitGuardian platform, honeytokens are automatically identified, preventing unnecessary alerts in the dashboard. This means you won't be inundated with false alarms about secrets incidents, saving your security team valuable time in investigation and response efforts. We know this is something important for defenders, and this precision in alerting greatly enhances security operations.
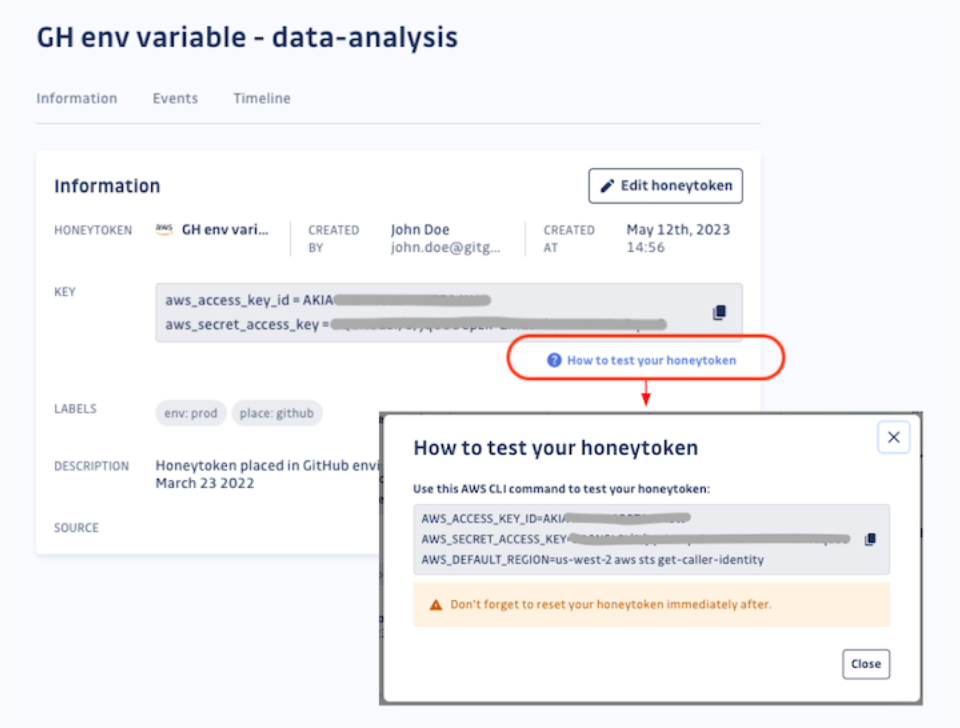
Simple and easy way to test honeytokens
Testing honeytokens is made convenient through a modal with terminal commands. This feature allows you to verify the effectiveness of your honeytokens in triggering alerts.
By clicking the "How to test your honeytoken" link, you can access this modal.
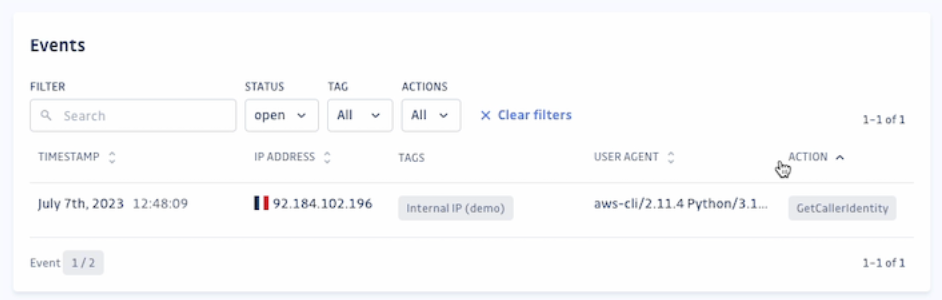
Comprehensive event logs for thorough analysis
The Honeytoken detail page provides a log of every event where the honeytoken was triggered. This data is invaluable for in-depth analysis and understanding of each event. It includes:
- Timestamp of the trigger event.
- The IP address of the person or entity that activated the honeytoken.
- Tags associated with the event.
- User-agent details describing the operating system, device type, and browser/software used for the request.
- Specific action attempted when the honeytoken was in use.

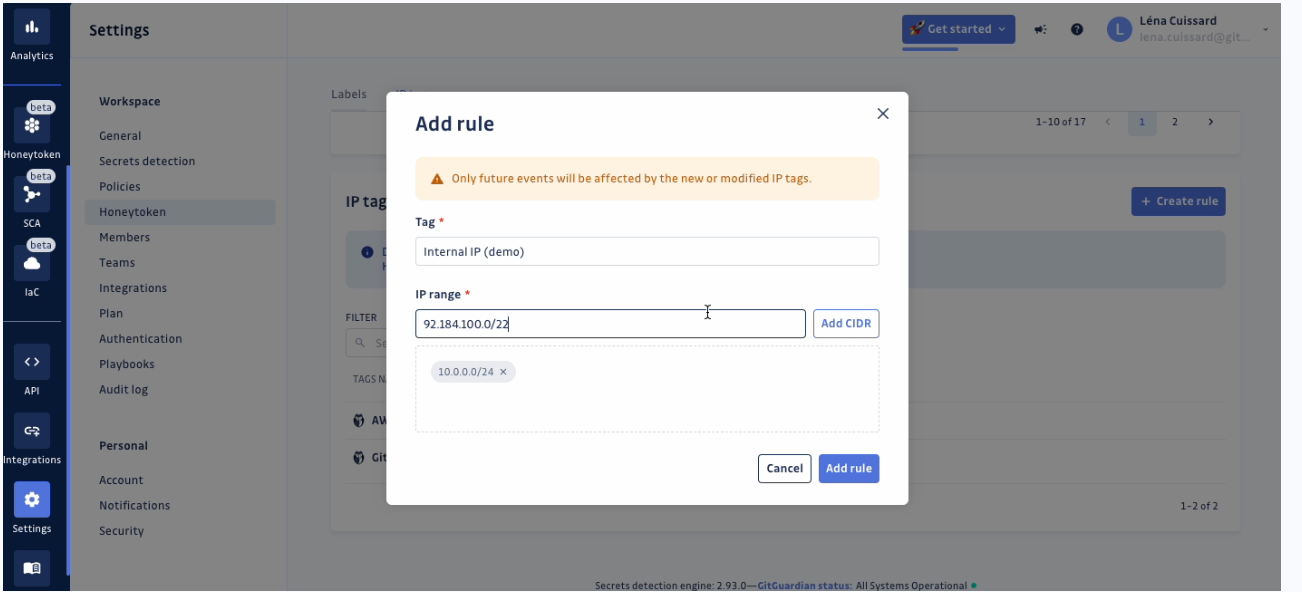
IP Tagging for event origin analysis
Custom rules can be set up to assign tags based on IP addresses, allowing for differentiation of events based on their origin, like internal IPs. This feature enhances precision in threat analysis.
Managing this feature is simple through the Settings > Honeytoken > IP tags section.
GitGuardian also automatically tags events originating from GitGuardian Public Monitoring IPs (used for monitoring public GitHub) and AWS internal IPs for events within AWS. These tags are applied when a honeytoken is publicly leaked on GitHub. You can efficiently manage events by filtering based on these tags.
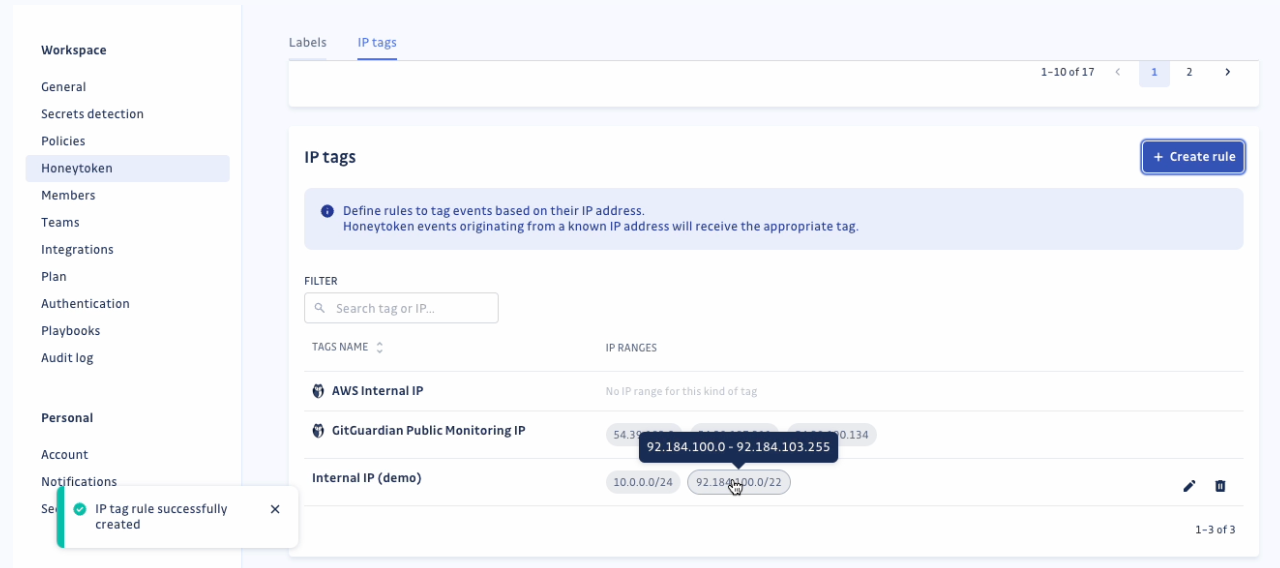
To enhance clarity, we've added country flags next to IP addresses in the Events table. This helps you identify the origin of events more precisely, making it easier to spot potential threats.
Code leakage detection on public GitHub
This one is a favorite among our users! Honeytoken offers a powerful capability - the ability to swiftly identify a code leak.
If a honeytoken ends up in a public GitHub repository, GitGuardian Public Monitoring quickly detects it. You'll receive an immediate alert, and these identified honeytokens are labeled as "Publicly Exposed". With a simple click, you can access a window displaying every public GitHub commit where your honeytoken was found. This way, you can efficiently handle these incidents and concentrate on safeguarding your other secrets.

What's next for Honeytoken?
Our beta program garnered immense interest, with over 700 eager minds joining the waitlist. We are deeply grateful to our beta testing community for their valuable support in shaping Honeytoken's journey. Several accounts created honeytokens as we granted them access to Honeytoken. Our success was anchored in the platform's mature features that resonated with beta testers. We're especially thrilled to share that our first customers emerged from the beta phase – an affirmation of Honeytoken's future potential.
And speaking of the future, as we transition beyond beta, here's a sneak peek at what's in store:
- Expanding to on-prem customers: We understand that one size doesn't fit all. That's why we're working on making Honeytoken compatible with self-hosted installations.
- Automating honeytoken dissemination: Addressing a common request from our beta users, we're currently developing an automated dissemination process for honeytokens. Recognizing that manual insertion can be time-consuming, this enhancement will enable large enterprises to efficiently deploy and manage honeytokens at scale within their code repositories through automated pull requests.
- Diverse honeytoken types: We're not stopping at AWS key pairs. Our team is exploring the implementation of additional honeytoken types.
Honeytoken is now yours to explore, deploy, and embrace wherever your supply chain security journey leads you. As always, keep a watchful eye on our release notes and public roadmap. The journey continues, and with Honeytoken by our side, together, we will step into a future where vigilance meets innovation.
If you're already a GitGuardian customer, access this new capability through the new Honeytoken tab in your dashboard. If you haven't signed up for GitGuardian Secrets Detection yet, you can do so for free. This will not only help you locate hardcoded secrets in your code but also provide you with 5 free honeytokens.
For a seamless setup, you can refer to our step-by-step guide. At GitGuardian, we're dedicated to keeping you safe, and with Honeytoken, we are helping to turn the tables on attackers and fight them back faster!
See upcoming sessions








