What are Honeytokens?
GitGuardian Honeytoken creates decoy credentials called honeytokens that do not grant access to customer resources or data. Instead, they act as tripwires that reveal information about the attacker, such as IP Address, User Agent, and Location.
Our honeytokens are indistinguishable from real secrets to attackers. They are designed to be triggered by secret scanners like TruffleHog or Gitleaks, which are often misused by hackers. If a hacker uses a secret scanner to search for developer secrets, they will trigger the honeytoken and alert the security team of a potential security incident.
Why Should You Use Honeytokens?
There are several reasons why you should use honeytokens in the software development life cycle (SDLC) and software supply chain:
- Early breach detection: Honeytokens act as an alarm system, allowing you to detect security breaches early on and prevent damage.
- Strengthened supply chain security: Honeytokens help identify if a vendor in the supply chain has been compromised, allowing you to strengthen security and prevent further damage.
- Clear visibility of monitored codebase: Honeytokens provide a clear view of where they have been deployed, ensuring they were deployed correctly and not duplicated.
- Easy deployment at scale: Honeytokens can be created, deployed, and managed on a large scale, securing multiple code repositories simultaneously.
- Code leakage detection: Honeytokens help detect if code has been leaked on public platforms, saving time and resources and preventing data loss.
You can read more in this blog post:

How to Create GitGuardian Honeytokens
Step 1: Go to your GitGuardian dashboard > Honeytoken
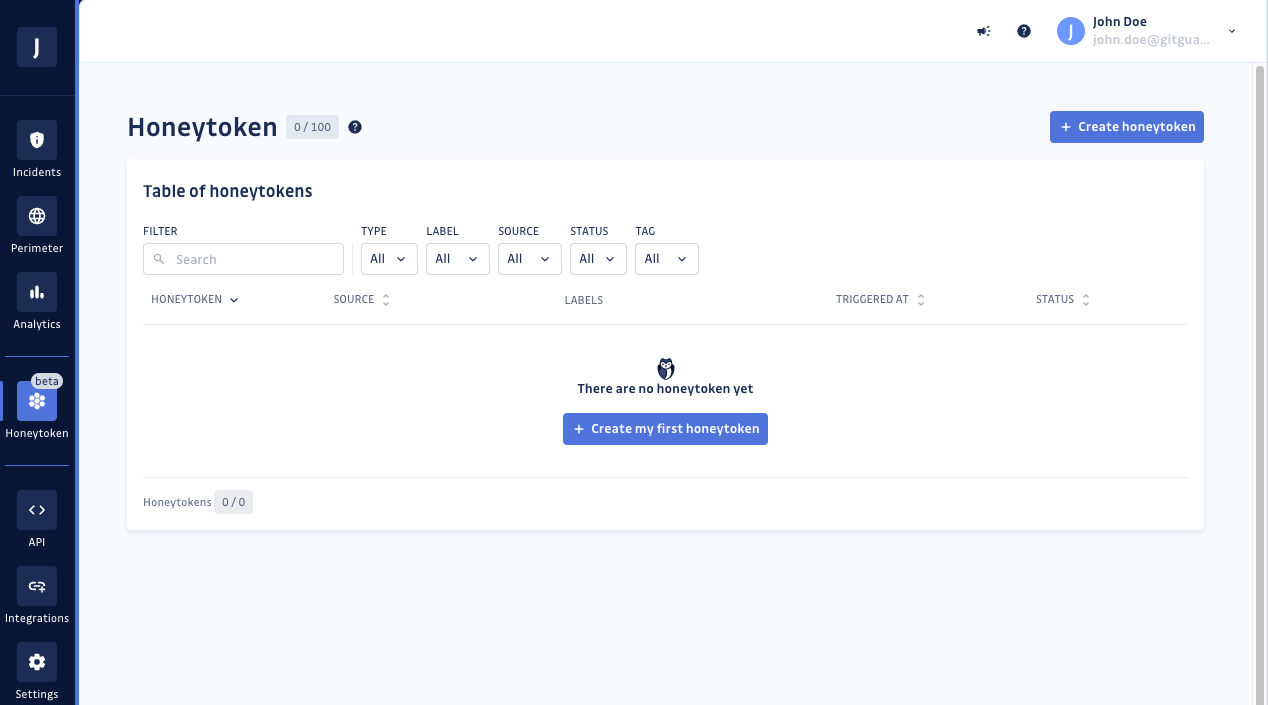
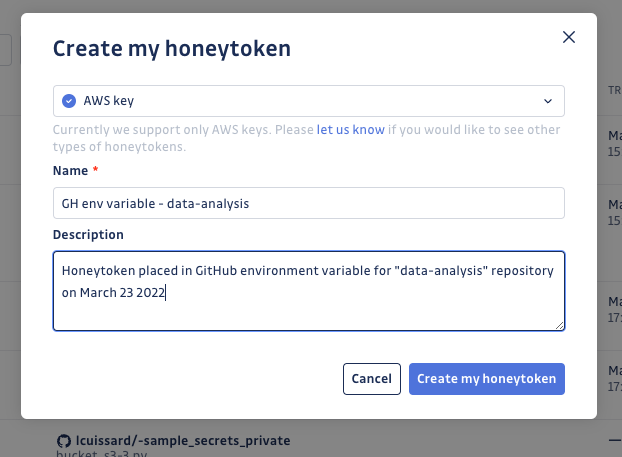
Step 2: Create your honeytoken — click on "Create my first honeytoken" and provide a name and optional description. The description can include specific details about where and how the honeytoken will be placed. Additionally, you can use labels to categorize your honeytoken in a structured manner. Then click "Create my honeytoken."
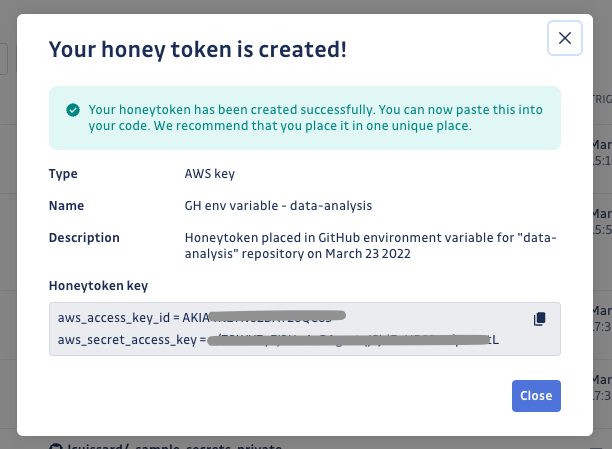
Congratulations! Your honeytoken creation has been confirmed, and you have received your honeytoken key.
Step 3: Test your honeytoken — copy the aws sts get-caller-identity command displayed in the information box and paste it into your terminal to trigger the honeytoken:
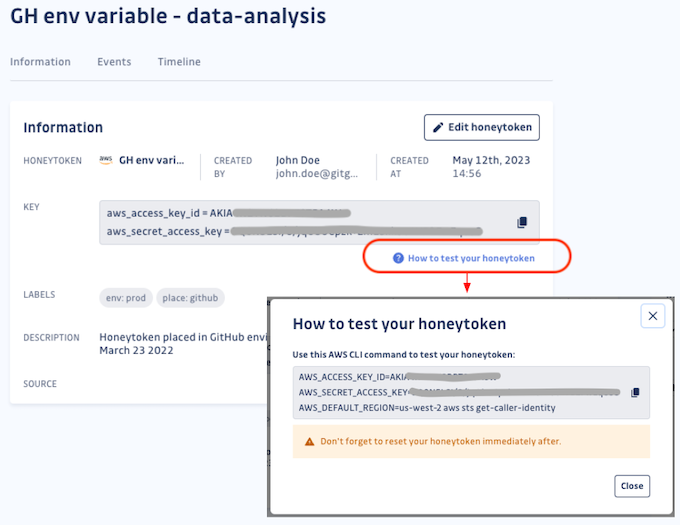
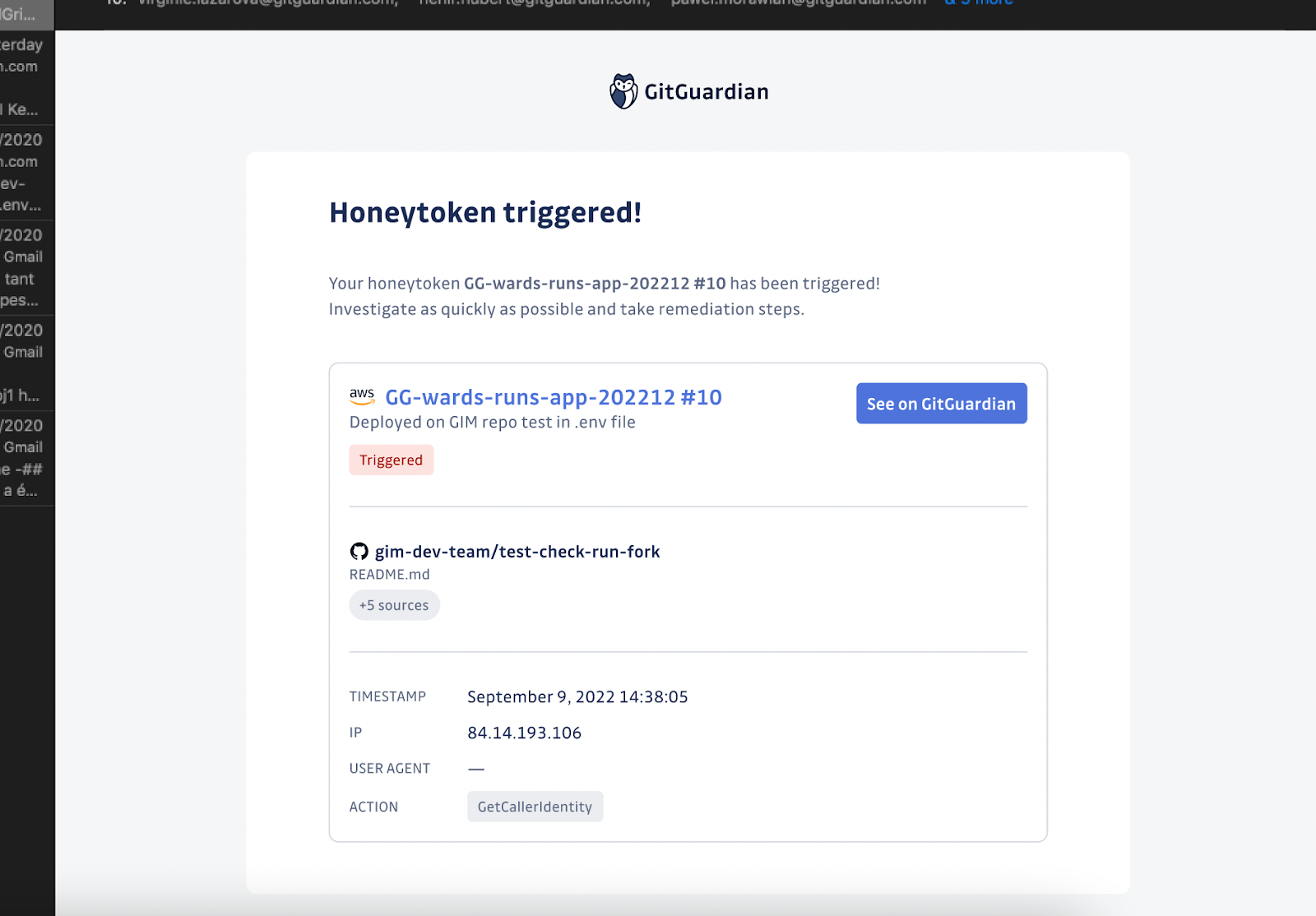
Step 4: Verify your honeytoken data — you can check by verifying the status on the dashboard, along with Events data (Timestamp, IP address, User-agent, and Action performed). Additionally, you should have received an email.
Step 5: Reset your honeytoken — resetting the honeytoken changes its status back to Active, allowing it to be triggered again on future attempts. After resetting, your honeytoken is as good as new!
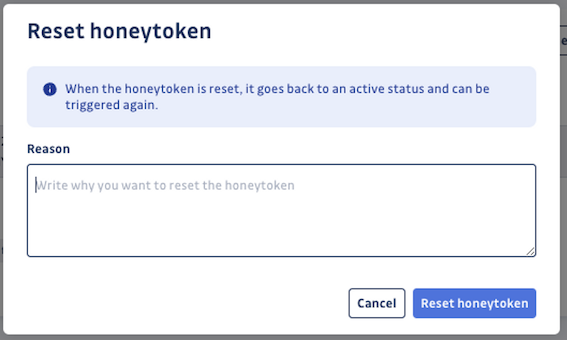
In a real-life scenario, if you confirm that a triggered honeytoken corresponds to a security incident, you should rather revoke the honeytoken after investigating and taking the necessary measures to protect your environment.
Step 6: Place your honeytoken — you are now ready to start using the honeytoken to protect any system. You can also further configure your alerts to receive instant notifications through custom webhooks, allowing you to customize your alerting workflow.
If an attacker encounters these AWS credentials, they will likely try to use them. In consequence, you would be immediately notified of the unauthorized access attempt.
With just a few lines of code, you can now effectively deceive attackers!
Where Should You Place Honeytokens?
Here are some examples of where you can place honeytokens:
- Source control systems (git repositories): Commit them in your repositories to detect compromised codebases. Check our guide for more information:
- CI/CD pipelines: Hide them in your CI/CD tools to detect compromised pipelines:
- Container registries: Expose them in Docker images or other internal packages.
- Other productivity tools: Plant them in project management tools like Jira, Linear, Asana, Confluence, or messaging tools like Slack.
See upcoming sessions