
When Infostealer Frontiers Meet Identity-Centric Defense: Lessons from BSides SATX 2025
From malware markets to IAM frameworks, BSides SATX 2025 showed why modern security must evolve from static protection to identity-centric, adaptive defense.

From malware markets to IAM frameworks, BSides SATX 2025 showed why modern security must evolve from static protection to identity-centric, adaptive defense.

From malware markets to IAM frameworks, BSides SATX 2025 showed why modern security must evolve from static protection to identity-centric, adaptive defense.

Align your AI pipelines with OWASP AI Testing principles using GitGuardian’s identity-based insights to monitor, enforce, and audit secrets and token usage.

Based on the talk “The Explosion of Machine Identities: Are You Aware of This Silent Threat?” at SecDays France 2025.

The speakers at ShowMeCon 2025 explored why policy isn't protection without validation. AI, identity, and threat detection must align to reduce operational risk.

GitGuardian and GuidePoint Security have partnered to deliver enhanced secrets detection and non-human identity security solutions to North American customers, offering tools to combat secrets sprawl and mismanaged identities.
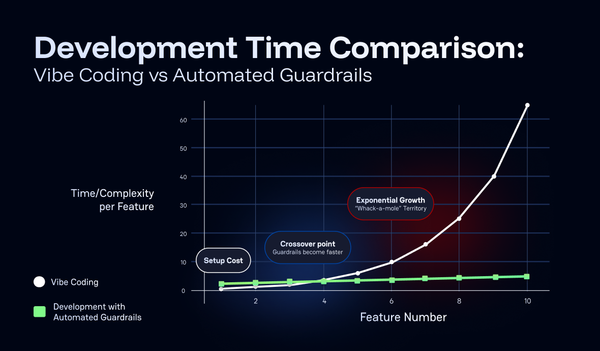
Vibe coding might sound like a trendy term, but it's really just developing software without automated checks and quality gates. Traditional engineering disciplines have always relied on safety measures and quality controls, so vibe coding should be no different in my honest opinion.

Identiverse 2025 exposed the urgent need for NHI governance. From AI agents to orphaned credentials, NHIs and their sprawling secrets are today’s most overlooked risks.

See how GitGuardian's deep discovery, combined with Akeyless's automation, delivers full secrets lifecycle control.

Our latest State of Secrets Sprawl 2025 research reveals a troubling reality: the majority of leaked corporate secrets found in public code repositories continue to provide access to systems for years after their discovery.

At BSides312 in Chicago, experts showed that defending systems requires defending people, with trust, inclusion, and communication as key controls. Defense is deeply human.

PHP TEK 2025 revealed how empowering developers through clear, embedded security practices strengthens defenses without adding operational friction.

How I wrapped large-language-model power in a safety blanket of secrets-detection, chunking, and serverless scale.