Managing AWS IAM with Terraform - Part 2
In this second part, you will learn how to centralize IAM for multiple AWS accounts, create and use EC2 instance profiles, and implement just-in-time access with Vault.

In this second part, you will learn how to centralize IAM for multiple AWS accounts, create and use EC2 instance profiles, and implement just-in-time access with Vault.

How can an attacker exploit leaked credentials? In this new series, we try to answer this question by imagining plausible attack scenarios. First case: an RSA private key is found in a Docker image.

Mark Bichon from Bearer, the SAST solution for mapping sensitive data flows, shares some essential tips to create security policies that don't feel like a development slowdown.
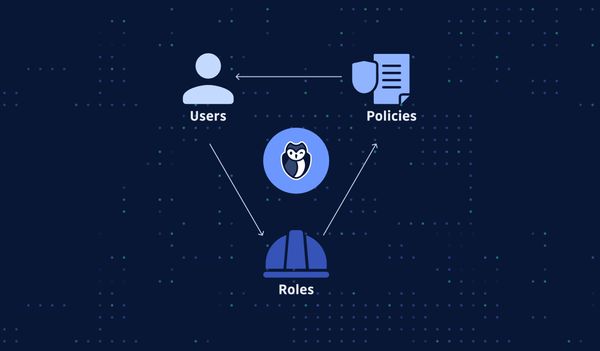
Identity and access management is a pillar of security. With the advent of the cloud, it got a lot more complicated. Here is a recap of the best practices to put in place to secure AWS IAM.

In this article, we’ll be going over the 1.1 revision of The Secure Software Development Framework that was published earlier this year.

Learn more about the DMCA law and how it applies to digital artifacts like source code.
In this tutorial, we will show how to integrate GitGuardian Shield to run on one of the most famous CI tools: Jenkins (with a cool bonus!).
This tutorial will guide you through the setup of a GitHub Action generating a Seccomp filter for your application, a cutting-edge security feature for hardening containerized workloads.

Learn how to set up an AWS EKS cluster with Terraform and leverage best practices to configure roles, service accounts, logging, and auditing with useful tools.

A data breach is one of the worst scenarios in today’s enterprise security. What’s your plan to remediate this kind of situation, minimize the impact, and ensure business continuity? Although there is no such thing as a one-size-fits-all tactic, the following steps are crucial to a positive outcome.
Infrastructure as Code is slowly but surely becoming norm for organizations that seek automation and faster delivery. Learn the big concepts powering it in this article.

More and more parts of the software development process can occur without human intervention. However, this is not without its drawbacks. To keep your code and secrets safe, you should add the following security practices to your CI pipeline.