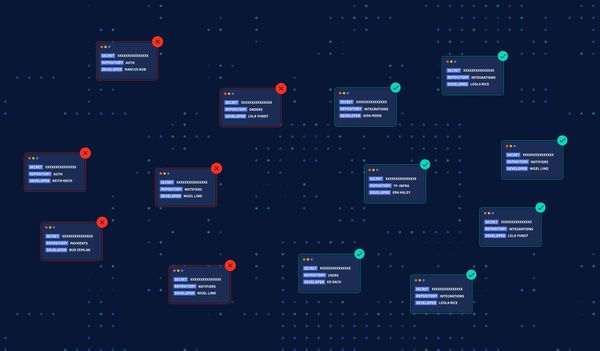
Investigating, prioritizing, and remediating thousands of hardcoded secrets incidents
This article aims to provide application security teams with a guide to effectively prioritize, investigate and remediate hardcoded secrets incidents at scale.

This article aims to provide application security teams with a guide to effectively prioritize, investigate and remediate hardcoded secrets incidents at scale.

We're unlocking new use cases with CyberArk. Explore the first-ever integration between our secrets management and secrets detection solutions and how they can help you keep your secrets protected at all times.

Unlock the latest secrets detectors, automate severity scoring, and dive into GitGuardian's unique dev & sec collaboration features!

GitGuardian can now help you check if your (already) hardcoded secrets have not also leaked publicly in code, issues and gists of projects located outside your GitHub organizations.

Discover insights from Gartner's Security and Risk Management 2023 Summit in London. Learn how CNAPP enhances protection in a complex cloud environment.

Today, we’re unveiling HasMySecretLeaked, a free toolset to help security and DevOps engineers verify if their organization’s secrets have leaked on GitHub.com.

Detect real secrets, automate severity scoring, focus on your critical incidents, fix faster with developers, and get the support you deserve from our team of experts!

Learn more about the various sources of exposed secrets beyond source code repositories. From CI/CD systems to container images, runtime environments to project management tools, uncover the risks associated with storing secrets in these sources.

Tweak our default severity rules or create new ones and align GitGuardian’s automated severity scoring engine with your organization’s security priorities!
The new partnership enables Snyk and GitGuardian to build, integrate, and grow together to help development and security teams scale their security programs and significantly reduce their applications' attack surface at every stage of the code-to-cloud lifecycle.

Kondukto and GitGuardian have teamed up to provide an integration that brings together their knowledge in AppSec orchestration and automated secrets detection.

With GitGuardian available on AWS Marketplace, we’re making it easier for all organizations using AWS to protect their software supply chain from exposed secrets and credentials.