
AI Is Making Security More Agile: Highlights from ChiBrrCon 2026
ChiBrrCon 2026 tackled AI, resilience, and operational agility in enterprise security. Learn what top speakers shared on SOC modernization and architectural risk.

ChiBrrCon 2026 tackled AI, resilience, and operational agility in enterprise security. Learn what top speakers shared on SOC modernization and architectural risk.

Learn more about the DMCA law and how it applies to digital artifacts like source code.
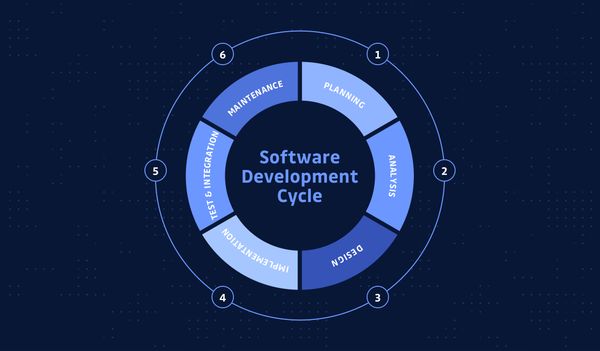
In this post, we are going to break down the SDLC and look at how we can add security at each stage with helpful resources.

With more than 170k GitHub users and 4.3M (!) repositories under our shield, GitGuardian is proud to help the developers’ community code safer. Here is what you’ve been telling us lately.

GitGuardian is moving! We are happy to share with you some pictures of our great new offices in Paris city center.

GitGuardian is now a verified CircleCI technological partner. Use the ggshield orb to run automated secrets detection and remediation in your CircleCI workflows.

Keep secrets out of your source code. GitGuardian's automated secrets detection now supports Stripe webhook signing secrets.
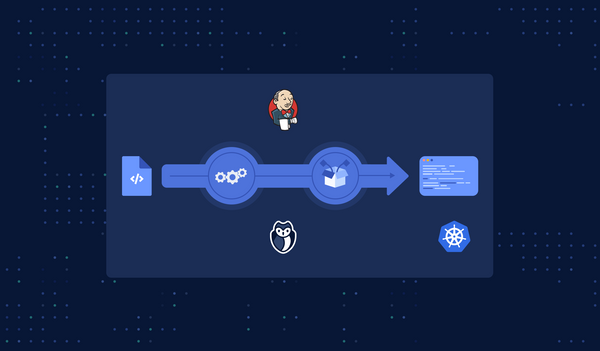
In this tutorial, we will show how to integrate GitGuardian Shield to run on one of the most famous CI tools: Jenkins (with a cool bonus!).

Attackers have used stolen OAuth tokens issued to Travis CI and Heroku to gain access to private git repositories on GitHub. Here we take a look at exactly what happened, why it's significant, and how to mitigate the issue.

Edouard, GitGuardian's VP Product, is a seasoned cybersecurity specialist who joined GitGuardian to push our DevSecOps solutions to new heights. Find out more about his background and what excited him to become a Guardian.
![Compromising CI/CD Pipelines with Leaked Credentials [Security Zines]](/content/images/size/w600/2022/04/22W15-blog-SecurityZines-Compromising_CICD_pipelinesnal.jpg)
He struck again! New Security Zine, this time focusing on how leaked Jenkins credentials can lead to a complete supply chain takeover...
This tutorial will guide you through the setup of a GitHub Action generating a Seccomp filter for your application, a cutting-edge security feature for hardening containerized workloads.

Keep secrets out of your source code. GitGuardian's automated secrets detection supports Redis database credentials.