
Protecting Developers Means Protecting Their Secrets
Secrets don’t just leak from Git. They accumulate in filesystems, env vars, and agent memory. See how to find them, stop the bleed, and protect your whole supply chain

Secrets don’t just leak from Git. They accumulate in filesystems, env vars, and agent memory. See how to find them, stop the bleed, and protect your whole supply chain

Tackle secrets sprawl no matter where you are on your security journey. GitGuardian has a plan for everyone to take on secrets detection and remediation at scale.

As AI continues to reshape how code is written and managed, the emphasis on vigilant, security-conscious development practices becomes increasingly crucial. SAST stands as a critical tool in ensuring that the efficiencies gained through AI do not come at the cost of security and reliability.

Explore security findings from Datadog's research into recent attacks, highlighting two sophisticated attack methods and vital lessons in secrets security.

Discover how honeytokens enhance security by detecting breaches in real-time across the software development lifecycle. Learn how to deploy these decoy credentials and traps effectively, bolstering defenses against cyber threats.

The healthcare industry, holding a treasure trove of valuable data, finds itself at a pivotal point in its fight against cyber threats. This sector, harassed by cybercriminals, has endured the highest average costs due to breaches for over a decade.

Let's walk through nine of the top secrets management solutions for 2024.

ChiBrrCon IV brought together the Chicago security community to learn about cybersecurity and risk management and heard from some of the folks CISOs report to.

We're unlocking new use cases with CyberArk. Explore the first-ever integration between our secrets management and secrets detection solutions and how they can help you keep your secrets protected at all times.

Tiexin Guo Senior DevOps Consultant, Amazon Web Services Author | 4th Coffee In the cloud-native era, Infrastructure as Code (IaC; read more about it in this blog here) has become the de-facto standard for managing cloud infrastructure, and more. While Terraform has been around for
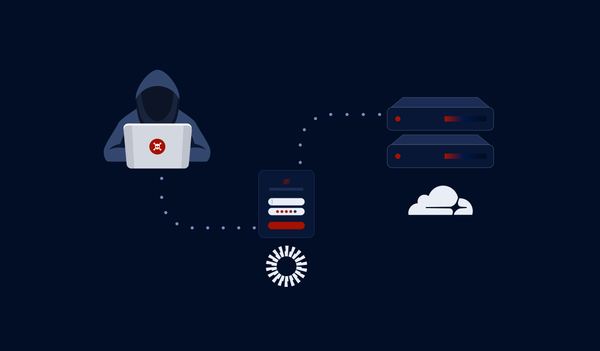
Cloudflare experienced a security breach when its internal systems were compromised, leading to unauthorized access to sensitive data. Another incident highlights the importance of maintaining strict secrets security across the supply chain.

It's time for our monthly comic. This month: "Guarding your secrets -- For Kids!"
Discover GitGuardian's efficient POC-based approach to evaluating a secrets detection and remediation platform, simplifying the complex buying process for enterprises.