2,622 Valid Certificates Exposed: A Google-GitGuardian Study Maps Private Key Leaks to Real-World Risk
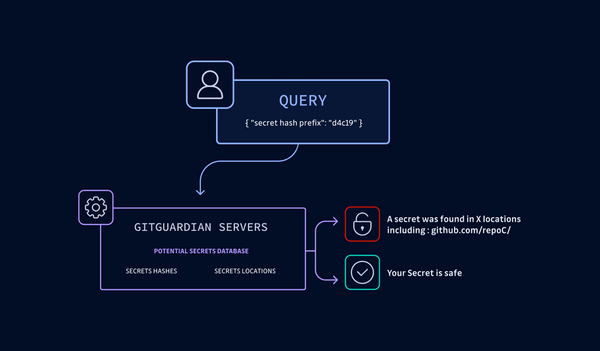
GitGuardian partnered with Google to answer: what happens when private keys leak? Using Certificate Transparency, we mapped about 1M leaked keys to 140k certificates. Result: 2,622 were valid as of September 2025, exposing major organizations. Our disclosure campaign achieved 97% remediation.