
AI Is Making Security More Agile: Highlights from ChiBrrCon 2026
ChiBrrCon 2026 tackled AI, resilience, and operational agility in enterprise security. Learn what top speakers shared on SOC modernization and architectural risk.

ChiBrrCon 2026 tackled AI, resilience, and operational agility in enterprise security. Learn what top speakers shared on SOC modernization and architectural risk.

Continuing our series about potential attack scenarios, learn how a very easy configuration mistake on GitHub can lead to a major security breach.

Cybersecurity in Australia has moved well and truly into the focus of the mainstream media and the everyday public. This year we saw two catastrophic security breaches with Optus, an Australian telecom provider, and Medibank, one of the largest health insurance providers in Australia.
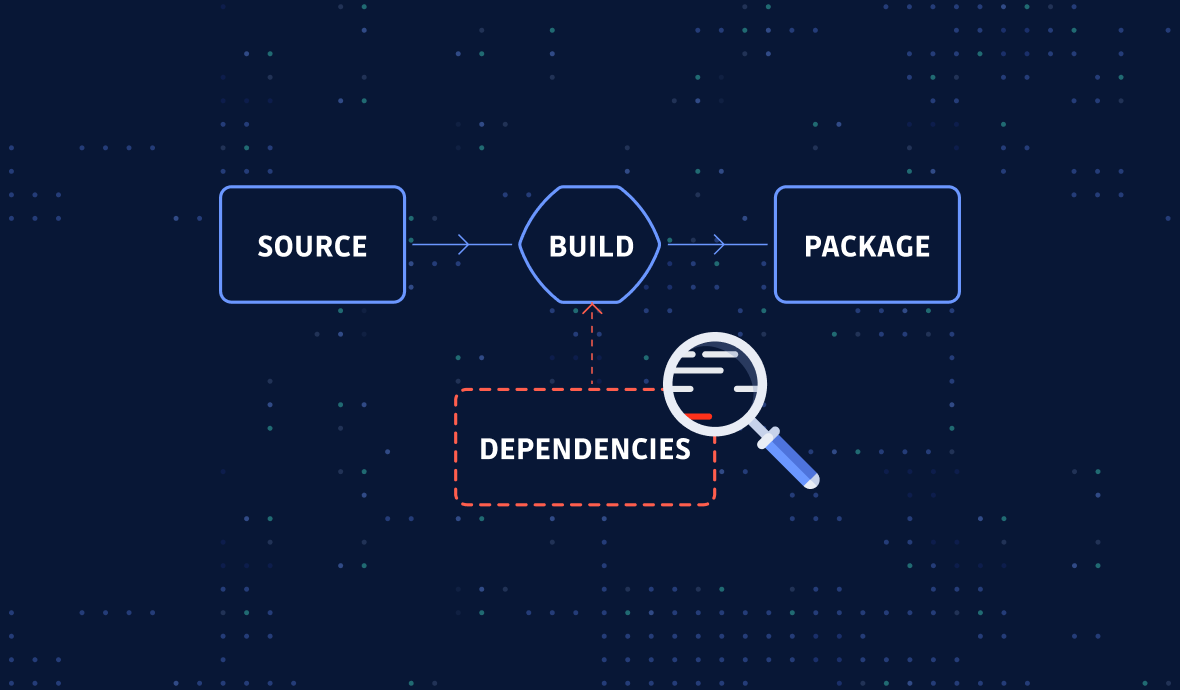
Software composition analysis is an essential part of application security. Here are the important factors to consider when selecting an SCA scanner to be sure it is well-suited to your needs.
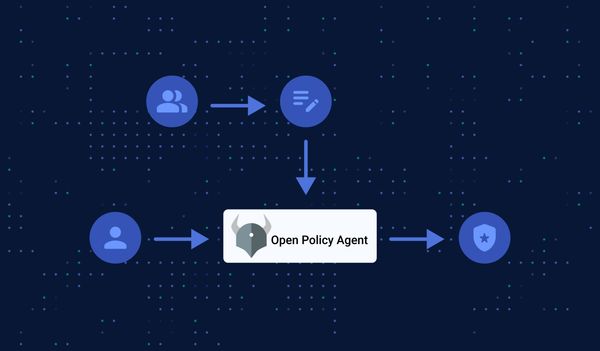
Learn the benefits of policy as code and start testing your policies for cloud-native environments.

GitGuardian joined dozens of security companies in New York City to share knowledge about the ever-shifting enterprise landscape. Here are just a few of the highlights from CyberTech NYC 2022.

You might already be using a Cloud IDE for certain projects. This exciting evolution of the local dev environment has a lot of advantages but also brings some new risks. This article will help you stay safe as you embrace the cloud for your coding needs.

Eugène, Staff Engineer at GitGuardian, explains the thinking and the technical choices behind one of the most anticipated features of this year: Teams.

We're happy to present you our Secrets Management Maturity Model, a model to help your organization make sense of its actual posture and how to improve it.

New research by CyberNews has revealed that there are millions of private git repositories that are, in fact, not all that private.

Learn more about GitGuardian’s no-code workflows and how they can help you enjoy some respite from the manual and grunt work no security engineer ever enjoys.

Securing your apps can feel overwhelming and isolating. Fortunately, there is a community making free security tools and resources, that would welcome you at their events: OWASP

Dropbox has confirmed they suffered a data breach involving a bad actor gaining access to credentials, data, and other secrets inside their internal GitHub code repositories.