
AI Is Making Security More Agile: Highlights from ChiBrrCon 2026
ChiBrrCon 2026 tackled AI, resilience, and operational agility in enterprise security. Learn what top speakers shared on SOC modernization and architectural risk.

ChiBrrCon 2026 tackled AI, resilience, and operational agility in enterprise security. Learn what top speakers shared on SOC modernization and architectural risk.

DevSecOps expert and GitHub Star Sonya Moisset shared with us her tips to improve your open-source repository's security in a few simple steps.

On the occasion of the launch of the GitGuardian Labs innovation platform, we had the pleasure to discuss this initiative with Eric Fourrier, GitGuardian's CTO & co-founder.

In this tutorial, you will learn how to add GitGuardian real-time monitoring to a CircleCI workflow to scan every new commit for secrets.

Missed out on Black Hat 2022 briefings or got stuck in the business hall? We have you covered.

How can an attacker exploit leaked credentials? In this new series, we try to answer this question by imagining plausible attack scenarios. Second case: an AWS secret is found in a private repository.
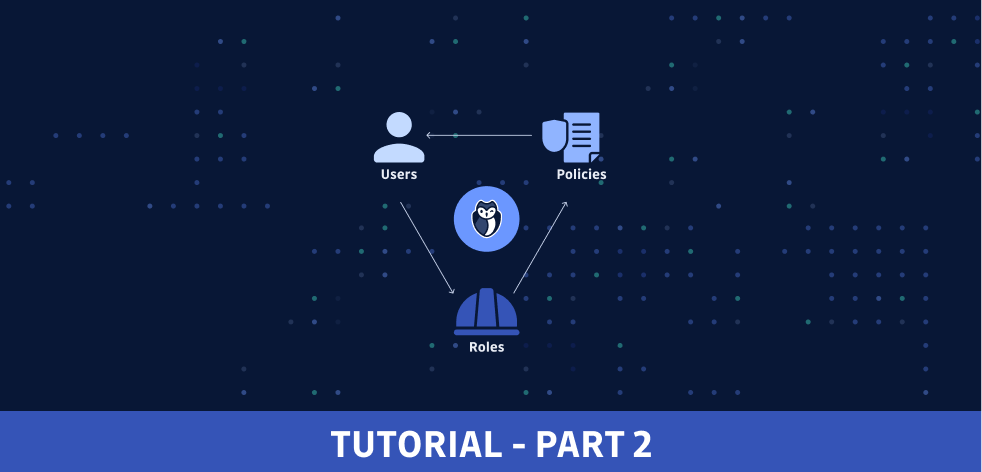
In this second part, you will learn how to centralize IAM for multiple AWS accounts, create and use EC2 instance profiles, and implement just-in-time access with Vault.

This month we had the opportunity to chat with Mehdi about his background, what he and his team are cooking at GitGuardian, and the benefits of martial arts applied to software engineering
![Canary Tokens [Security Zines]](/content/images/size/w600/2022/08/blog-SecurityZines-CanaryTokens.jpg)
Security Zines are back, this time to illustrate the concept and usage behind canary tokens, a powerful intrusion detection trick. Check it out, we've got something for you!

Gartner has acknowledged GitGuardian as a Sample Vendor in two reports this summer, the Gartner Hype Cycle™ for Application Security 2022 and the Gartner Hype Cycle™ for Agile and DevOps 2022.

We are happy to announce the release of our latest open-source project, ggcanary, the GitGuardian Canary Tokens, to help organizations detect intrusion in their developer and DevOps environments.

How can an attacker exploit leaked credentials? In this new series, we try to answer this question by imagining plausible attack scenarios. First case: an RSA private key is found in a Docker image.

As announced in January when we became SOC 2 Type I compliant, we worked to complete the process and get the SOC 2 Type II compliance. This is now effective!