
AI Is Making Security More Agile: Highlights from ChiBrrCon 2026
ChiBrrCon 2026 tackled AI, resilience, and operational agility in enterprise security. Learn what top speakers shared on SOC modernization and architectural risk.

ChiBrrCon 2026 tackled AI, resilience, and operational agility in enterprise security. Learn what top speakers shared on SOC modernization and architectural risk.

Philippe explains how the GitGuardian engineering team cleverly leveraged Postgres triggers to achieve better performance. Until cons outweighed pros.

Mark Bichon from Bearer, the SAST solution for mapping sensitive data flows, shares some essential tips to create security policies that don't feel like a development slowdown.

This article describes the approach followed by one of GitGuardian's enterprise customers to implement a secrets detection program and stop poor secrets management practices at the source.

Curious about how technology is transforming our world? So is Alexandre, who told us about the path that led him to join one of the most interesting French scale-up.

Learn more about the challenges awaiting organizations of thousands of developers when deploying secrets detection and how we're addressing them with our latest feature releases.

Sofien, one of GitGuardian's Tech Leads, describes how pre-commit hooks are used to save time and also secure commits company-wide.
![ggshield, the GitGuardian CLI [Security Zines]](/content/images/size/w600/2022/06/202206-blog-securityzines-final.jpg)
In his latest stroke of genius, Rohit shows us how gghsield fits into the development cycle to shield your code from leaking secrets.

Developer experience or DX is a security issue. Find out how we're solving it at GitGuardian with ggshield, the secrets detection CLI built for developers.
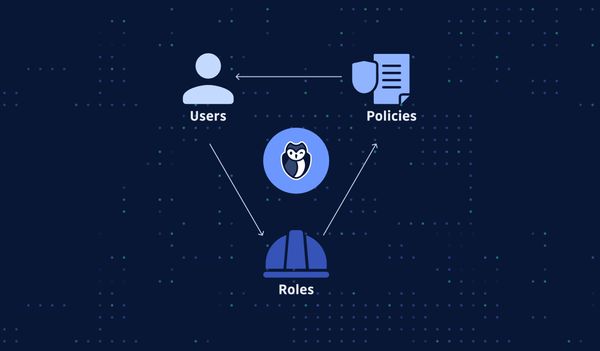
Identity and access management is a pillar of security. With the advent of the cloud, it got a lot more complicated. Here is a recap of the best practices to put in place to secure AWS IAM.

In this article, we’ll be going over the 1.1 revision of The Secure Software Development Framework that was published earlier this year.

In recent years, resorting to MSPs has become very popular for companies wanting to accelerate the digitization of their businesses. With this surge in popularity, MSPs now face the question: how to ensure we can meet our cybersecurity responsibilities?

As Senior SRE, Jon-Erik was aware that many secrets could be hidden in the repositories he supervises, and new ones leaked every day. He told Peerspot how and why he chose GitGuardian and the improvements his team received.